All Articles
Filter by topic:

Online Safety and Privacy
What Is Smishing? How Text Message Scams Work (And How To Avoid Them)
Cybercriminals love to go smishing, but you don’t have to take the bait.

Online Safety and Privacy
What Are Common Crypto Scams?
Cryptocurrency investment scams are big business, but you can keep your wallet safe.

Online Safety and Privacy
Are Passwords Going Away? What You Need to Know About Passkeys
The future of logging in is already on your phone!

Online Safety and Privacy
10 Reasons Why You Need to Be At Convene: Cleveland
If you work at the intersection of people and security, then you got to join us this summer in Cleveland for our Convene conference.

Online Safety and Privacy
Is Microsoft Doing Away With Passwords?
If you use Microsoft Authenticator to store passwords, they will be deleted in August.

Cybersecurity for Business
How You Can Help Secure Smaller Vendors with Limited Budgets and Know-How
If you work in third-party risk management (TPRM), you face a growing challenge: how to keep your supply chain secure when many vendors are small businesses with limited cybersecurity resources?

Cybersecurity for Business
Your Business Has Been Hacked: How to Minimize the Damage
If your small business has been hacked, you need to act fast. Here are some key things to know to fight back, stay open, and build resilience in the event of a cyberattack.

Cybersecurity for Business
Why Physical Security Is Still Necessary for Cybersecurity
Physical security is an essential, but often overlooked, factor in cybersecurity.

Toolkits
Best Vacation and Travel Cybersecurity Tips
Whether you're lounging on a beach or hiking through the mountains, these days, you probably stay connected during your trip.

Cybersecurity for Business
How to Protect Your Small Business from Malware
Malware attacks, including ransomware, are one of the most common threats facing small businesses today.

Cybersecurity for Business
Best Practices for Protecting Your CRM Data
Your customers are the lifeblood of your business and their data is extremely valuable.

Online Safety and Privacy
Tread Lightly Online: How to Check and Manage Your Digital Footprint
While you can’t use the internet completely undetected, you can manage your digital footprint and protect your data privacy. Find out more using our guide.

Online Safety and Privacy
6 Cybersecurity Myths Debunked
There are a lot of myths flying around about cybersecurity. We’ll go over the most common cybersecurity myths and debunk them so we can stay safer online.

Online Safety and Privacy
Cyberbullying in the Workplace: How to Recognize, Address, and Prevent It
Cyberbullying is often associated with teenagers and social media, but some bullies grow up...and enter the workforce.

Online Safety and Privacy
Does AI Take Your Data? AI and Data Privacy
Generative AI, including platforms like ChatGPT, DALL-E, Google Gemini, Apple Intelligence, has revolutionized our relationship with technology.

Online Safety and Privacy
Why Your Family and Coworkers Need a Safe Word in the Age of AI
Scammers always rely on deception to trick people out of their money, but the sudden wide availability of artificial intelligence has increased the convincingness of their schemes.

Toolkits
AI Fools: Stay Sharp!
An awareness campaign on AI-enabled scams & responsible AI use.

Online Safety and Privacy
How to Update Your Software
An easy way to boost your cybersecurity is to always keep software and apps updated.

Online Safety and Privacy
What Is Phishing and How To Avoid It
Cybercriminals love to go phishing, but you don't have to get hooked.

Careers and Education
How To Write a Cyber Resume and LinkedIn That Gets Results
If you're hunting for a job in cybersecurity, you're aware that your resume and LinkedIn profile are critical to getting hired in this competitive field. But how do you create a resume that gets noticed?

Online Safety and Privacy
How to Stop the Flow of Personal Data with Cloaked CEO Arjun Bhatnagar
It’s Data Privacy Week, when we pay special attention to why data privacy is so critical in today’s world.

Online Safety and Privacy
Cybersecurity for Tax Season: Protect Your Identity and Refund
Tax season brings enough stress without adding scammers to the mix. But the reality is that criminals ramp up attacks in the first few months of the year, often impersonating the IRS or trusted services like H&R Block and TurboTax.

Careers and Education
Cyber Groups with Local Chapters You Can Join Today!
Cybersecurity is a community, even if it might not always feel like it with your nose buried in your laptop.

Online Safety and Privacy
What is Multifactor Authentication (MFA) and Why Should You Use It?
You can protect your online accounts with more than just a password.

Online Safety and Privacy
Stay Secure While Job Hunting
When looking for new opportunities, follow these simple steps to protect yourself from fraud.

Online Safety and Privacy
Use Apps and Software to Protect Your Data
Our data is constantly collected and shared, and we often don't even know all the types of data being gathered.

Online Safety and Privacy
Create and Use Strong Passwords
Passwords are the keys to safeguarding your digital and online life. They are your first line of defense. And knowing how to create and store strong passwords is one of the most critical aspects of everyday cybersecurity.

Online Safety and Privacy
What is Data Privacy and Why Should You Care?
Data Privacy Week is January 27 - 31, 2025!

Online Safety and Privacy
Cybersecurity Predictions for 2025: Challenges and Opportunities
The year 2024 was a whirlwind year for cybersecurity. From the fallout of high-profile ransomware attacks to the increasing commoditization of AI tools, the challenges kept mounting.

Online Safety and Privacy
Chinese Telecom Hack: How to Protect Your Messages
Learn how to protect your calls and texts following the Chinese telecom cyberattack with simple tips like using encrypted apps.

Online Safety and Privacy
How to Avoid Scams and Fraud
Online scams are becoming increasingly sophisticated, targeting people of all ages. But with some knowledge, you can protect yourself and your loved ones.

Online Safety and Privacy
Avoid Gift Card Draining Scams This Holiday Season
Gift cards make for easy, versatile gifts, especially during the busy holiday season. But they’re also prime targets for scammers who use "gift card draining" to steal funds before the recipient can even use the card. Let’s break down how these scams work and how you can stay safe.

Cybersecurity for Business
How to Make Cybersecurity Training Accessible
Does your training program reach all employees in your organization?
Online Safety and Privacy
What is Pig Butchering and How to Spot the Scam
"Pig butchering" is a scam that's been muscling into the headlines lately.
Toolkits
Oh Behave! The Annual Cybersecurity Attitudes and Behaviors Report 2024
Each year, the National Cybersecurity Alliance releases research to better understand the public’s security behavior and to act as a call to action for better secure habits online.

External Resources
KnowBe4 Children’s Interactive Cybersecurity Activity Kit
Looking for a way to talk about online safety and security with your children? KnowBe4 provides a fun and interactive cybersecurity kit to help you teach them valuable online safety and security skills.

Online Safety and Privacy
Did Hackers Steal Every Social Security Number? Here's What To Do.
Learn how to protect your social security number.

Careers and Education
The Evolution of Ethical Hacking: From Curiosity to Cybersecurity
The term "ethical hacking" was coined in 1995 by IBM Vice President John Patrick, but the practice itself has roots that stretch back much further.

Online Safety and Privacy
Data Breaches Slim Down Your Wallet
Data breaches are becoming an expensive predicament for all of us, even if your data isn't directly stolen in a breach.

Online Safety and Privacy
When Websites Make It Hard to Cancel...
Some websites and apps are designed to be manipulative – they make it hard to cancel a recurring subscription, obscure the fact that you will be charged, or hide the unsubscribe button.

Online Safety and Privacy
Watch Out for EBT Scams
Scammers target some of the most vulnerable.

Online Safety and Privacy
Protect Your Credit Cards from Skimmers and Shimmers
You can be a target of credit card skimming when you least expect it.

Careers and Education
How to Be an Awesome Cyber Mentor
Help close the cyber workforce gap by mentoring the next generation.

Careers and Education
How to Find a Mentor
Begin your career in cyber with the help of a mentor.

Online Safety and Privacy
Backups
Our digital devices contain vast treasure troves of data, from family photos and music collections to financial data, health records and personal contacts.

Online Safety and Privacy
When Scammers Call Grandma
"Your grandson has been arrested and needs bail money." "Your granddaughter was at fault in a car crash, and you need to pay the other driver's medical bills." What do you do if you receive these calls?

Online Safety and Privacy
Don’t Scam Me Right Now, I’m Trying to Buy a Home
How scammers try to trick home buyers and sellers.

Online Safety and Privacy
What To Do If Your Identity Is Stolen
With data breaches seemingly happening every week, more and more people are victims of identity theft.

Online Safety and Privacy
5 Common Real Estate Scams You Need to Know About
Since every real estate transaction involves a significant sum of money, anyone in the home market today will likely run into scammers on the prowl.

Online Safety and Privacy
Online Safety Basics
With a little prep, you can shield your information online and secure your digital systems and devices.

Online Safety and Privacy
Securing Smart Speakers and Digital Assistants
Smart speakers and digital assistants like Amazon Echo, Google Nest, Apple HomePod, and Sonos Era are integral to many modern households.

Online Safety and Privacy
How Data Breach Fatigue Can Impact Your Digital Health
When you hear your sensitive data was lost in another data breach, is exhaustion your first reaction?

External Resources
Stay Safe Online — Related Links
Here are helpful links from the National Cybersecurity Alliance’s sponsors, partners and friends to help you and your friends and family be safer and more secure online.

Online Safety and Privacy
Reporting Cybercrime
The first step toward bringing cybercriminals to justice is reporting cybercrime when it happens.

Cybersecurity for Business
What to Do if Your Business Facebook Is Hacked
There has been an uptick in cybercriminals attempting to target small businesses' Facebook profiles and ad accounts.

Online Safety and Privacy
Manage Your Privacy Settings
Direct links to manage your privacy settings on popular platforms and apps.

Online Safety and Privacy
How to Restore an MFA Authenticator App
Authenticator apps for multi-factor authentication (MFA) significantly enhance security but users must prepare for potential access loss due to device changes or loss by establishing recovery options and backups.

Online Safety and Privacy
Getting Kids & Teens to Care about Cybersecurity
We all know Kids & Teens today spend a lot of time online, but that doesn't necessarily mean they know how to stay safe.

Online Safety and Privacy
Getting Kids and Teens to Care about Cybersecurity
We all know kids and teens today spend a lot of time online, but that doesn't necessarily mean they know how to stay safe.

Online Safety and Privacy
Guard your Gateway: Internet Router Tips
While internet routers aren't as flashy as the latest VR headset or electric truck, they make internet access in our homes and businesses possible.

Cybersecurity for Business
How to Improve Your Cyber Resilience
We often think of cybersecurity in terms of our physical health—we talk about computer viruses and cyber hygiene. Cyber resilience is another way to think about your online fitness.

Online Safety and Privacy
SIM Card Swap Scams
Protect your phone from this increasingly common scam.

Careers and Education
8 Awesome Cybersecurity Careers
Explore the diverse landscape of careers in cybersecurity!

Toolkits
Cyber Survival Guide
The spirit of adventure beckons you online!

External Resources
Cyber Career Pathways Tool - NICCS
NICCS is the premier online resource for cybersecurity training, education, and career information.

Online Safety and Privacy
Spring Clean Your Online Life
A sloppy digital life can make your data harder to find and leaves your personal information vulnerable to bad actors. With a few steps, you can keep yourself and your family safe online with a squeaky clean digital life.

Cybersecurity for Business
Identity Management? Zero Trust? PIM? Succeed by Getting the Basics Right.
In today’s rapidly evolving online landscape, terms like zero trust, PIM (or Privileged Identity Management), and a series of other acronyms can leave the average person scratching their head.

Online Safety and Privacy
Protect Your Wallet from Payment App Scams
"I made a typo and accidentally sent you $3,000! Can you please send it back?"
External Resources
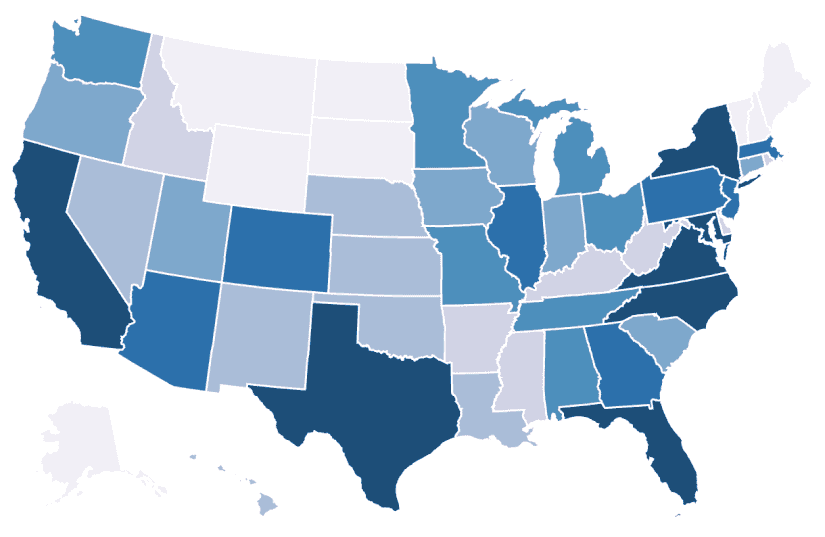
Interactive Cybersecurity Career Map - NICCS
Are you interested in entering the cybersecurity workforce or advancing your career? Explore thousands of federal cybersecurity job openings across the country and outside of the United States by clicking on the map below or using the drop-down menu. Select an area to find open cybersecurity positions in your preferred city, state, country, and salary range.

Cybersecurity for Business
Churning the Digital Waters: Insights from the 2023 Gone Phishing Tournament
Even as our online worlds become more complex, phishing schemes remain the most common type of cybercrime, according to the FBI.

Cybersecurity for Business
Mandate MFA: Take a Bold Step Toward a Secure Future
Making online platforms, services, and devices more secure by default is a good idea. But is it easy? Is it popular?

Online Safety and Privacy
Lessons from Data Privacy Week 2024
Data is now a valuable commodity.

Online Safety and Privacy
Avoiding Voting Scams and Safeguarding Elections
Elections are a cornerstone of American society. However, there are bad actors who don't respect the sanctity of our voting process.

Online Safety and Privacy
Protecting Our Kids' Data Privacy is Paramount
Protecting our children's online data is of utmost importance.

Toolkits
Online Dating and Romance Scams
Love is in the air and online, but so are cybercriminals.
Online Safety and Privacy
Connected Car Cybersecurity: Drive Safe Online
Cars have joined the Internet of Things, and with any connected device, you should follow some security best practices to keep your car's system safe.

Online Safety and Privacy
Safeguarding Your Internet Activity with Incognito Mode
We'll explore how incognito mode works, how it can help protect your browsing data, and, importantly, ways it isn't a magic solution to all your privacy concerns.

Cybersecurity for Business
8 Biggest Small Business Cybersecurity Misconceptions
Small businesses are crucial to the American economy, employing nearly half of the workforce, yet they remain prime targets for cyberattacks.
Online Safety and Privacy
How to Protect Yourself Against Deepfakes
Deepfake technologies can be used to steal your identity even if you don’t use generative AI platforms.

Cybersecurity for Business
No Weak Links: Think About Your Human Firewall
When it comes to fostering a culture of cybersecurity at your organization, sometimes it's best to start with creating awareness of some basic behavior changes.

Online Safety and Privacy
What to Know About Stalkerware
Even though the use of stalkerware to spy on adults is against the law, these duplicitous bits of code still pop up on app stores.

Cybersecurity for Business
Business Email Compromise: What It Is and How to Prevent It
While it has a bland name, Business Email Compromise (BEC) refers to a specific, nasty type of cyberattack that targets businesses of all sizes.
Cybersecurity for Business
Consider Cybersecurity in Your Investment Decisions
As cyberattacks become increasingly frequent and sophisticated, investors have a crucial role in urging companies to prioritize cybersecurity alongside other risk factors.

Online Safety and Privacy
How to Take Back Control of a Social Media Account
Responding to social media account takeover.

Cybersecurity for Business
Securing Success: Talking to the Board About Cyber Risk
Cyber risk across all business levels influences operations, reputation, and compliance.

Online Safety and Privacy
Traveling Securely: A Comprehensive Guide to Protecting Your Digital Footprint While on the Move
Technology accompanies us everywhere these days, and that includes traveling for work. Cybersecurity remains paramount even when you are thousands of miles away from the office.

Online Safety and Privacy
The Benefits of Using a Random Password Generator for Safer Online Access
One way to ensure your passwords are awesome is by using random password generators, often included with password managers.

Cybersecurity for Business
How Cyber Education for Employees Safeguards Your Business
Training employees is the cheapest, easiest way to boost your cybersecurity. Your employees are your first line of defense against as threats, and they are also your greatest asset.

Cybersecurity for Business
The City Secure: Cyber Tips for Local Governments
City governments operate in an increasingly connected world where city services, constituent services, and information sharing are online, digital, and shared on many platforms.

Toolkits
Safe Online Holiday Shopping
Watch out for online shopping scams around the holiday season!

Online Safety and Privacy
Extra! Extra! Avoid Fake News!
What is Misinformation, Disinformation, and Malinformation?

Cybersecurity for Business
Keep Your Business Safe and Connected With IoT
We're living in an era when everything connects to the internet, from your fridge to your car.

Online Safety and Privacy
Securing Higher Ed: 5 Tips for Learning Safe Online
Technology and academia are now seamlessly intertwined. While tech can further educational opportunities for students, it also comes with risk as the ivory tower delves into the Wild West of the internet.

Online Safety and Privacy
Oh Behave! The Annual Cybersecurity Attitudes and Behaviors Report 2023
STUDY: 37% Intimidated, 39% Frustrated with Online Security Highlighting Digital Anxiety

Online Safety and Privacy
Don't Blame the Victim: 'Fraud Shame' and Cybersecurity
There is often a culture of blaming fraud victims for their predicament, rather than focusing on the criminal and the crime.

Cybersecurity for Business
How to Prevent and Recover from Ransomware
Ransomware is a hack with teeth, an attack aimed to cause extreme financial pain to its victims.

Online Safety and Privacy
How Your Phone Number is Exposed: Phone Number Leaks
Your phone number counts as personal data, and you don't just want anyone out on the internet to have it.

Online Safety and Privacy
K-12 Cybersecurity: Keep Kids Secure from Kindergarten to Graduation
Nowadays, kids aren't just polishing apples and stuffing their bookbags before heading to school, they're firing up laptops and using video chat with their teachers.

Online Safety and Privacy
Share with Care: Staying Safe on Social Media
Hey, friends, followers, lurkers, and posters: you don't have to overshare!

Online Safety and Privacy
Pull the Shades Down on Your Browsing With a VPN
Did you know that your cruise around the internet every day might not be totally private?

Cybersecurity for Business
Sell Safe Online: Advice for Online Retailers
Be open for business and closed to cybercriminals.

Online Safety and Privacy
What To Do When Your Data Is Breached
Oh no! You’ve been notified that your sensitive information has been stolen in a data breach.

External Resources
KC7 Cyber: Cybersecurity Training
By playing through dozens of realistic cybersecurity intrusions you will progressively learn how to spot traces of malicious activity.

Cybersecurity for Business
Common Cybersecurity Misconceptions Held By Small and Medium-Sized Organizations
Employees empowered with the resources and knowledge to protect your organization from cyberthreats is one of the best lines of defense you can have.

Cybersecurity for Business
Detect Incidents
How to detect a cyber incident in your business.

External Resources
Helpful Resources for SMBs
Here are helpful links from our sponsors, partners and friends to help you keep your business secure.

Online Safety and Privacy
What LGBTQ+ Communities Should Know About Online Safety
The internet is now crucial for connecting LGBTQ+ people and communities across the globe, but how can you hone your cybersecurity and protect your privacy?

Online Safety and Privacy
Google Users: Fire Up Google Passkeys
In May 2023, Google announced it was launching a new login system called "passkeys."
Online Safety and Privacy
Will Passwords Become a Thing of the Past?
What to know about passwordless authentication and passkeys.

Online Safety and Privacy
Parenting in the Digital Age: 7 Online Dating Rules for Your Teens
Parenting in our always-connected world comes with new challenges, new learning curves, and new awkward moments.

Online Safety and Privacy
Think Intelligent About Artificial Intelligence
Artificial intelligence, including so-called “large language models” like ChatGPT, has rapidly become a major talking point in the press, amongst governments, and maybe even in your office!

Online Safety and Privacy
Hacked Accounts: What to Do Right Now
If an online account has been hacked, it's important to act fast.

Careers and Education
My Cyber Journey – Jennifer Mahoney
Meet Jennifer Mahoney Senior Consultant II, Data Governance, Privacy & Protection at Optiv.

Online Safety and Privacy
Wedding Planning Cybersecurity: Say "I Do!" to Digital Bliss
Congrats on your nuptials! We have a few tips for keeping your Big Day secure.

External Resources
National Cybersecurity Center: Cyber Force Initiative (Colorado)
The purpose of the Cyber Force Initiative is to quickly help students transition to a career in cybersecurity. Once the program application is completed, students will have access to all courses offered at the NCC: IT Fundamentals, Security Pro, Network Pro, and CyberDefense Pro.

Careers and Education
My Cyber Journey – Tonya Drummonds
Meet Tonya Drummonds, Director of Security & Resiliency at Dell Technologies

Online Safety and Privacy
Why Identity Management Matters to You
Do you worry about the security of your personal data in our digital age?

Online Safety and Privacy
Stay Secure While You Work From Home
Remote work seems like it is here to stay for many of us even as the COVID-19 pandemic recedes in our collective rearview mirror.

Careers and Education
Cybersecurity Internships and Entry Level Jobs
Find a cybersecurity internship or entry level job with our partners!

Online Safety and Privacy
What We're Leaning About Data Privacy in 2023
We are living in an incredible time in history – a time when advancements in technology are creating tools that will help solve society’s greatest challenges and fuel the next wave of innovation.

Online Safety and Privacy
How to Tell If Your Computer Has a Virus and What to Do About It
Computer viruses make your devices sick, but you can usually help them heal if you act fast.

Online Safety and Privacy
Avoid Search Engine Ad Malware!
It's a new year and already there is a type of scam becoming extremely popular with hackers.

External Resources
CybersecurityDegrees.org: Cyber Degree Finder
To help you find your dream job, we have resources on schools offering cyber degrees, plus information on career paths, professional certificates, free online courses in security topics, and more.

Online Safety and Privacy
Online Romance and Dating Scams
Love is in the air and online, but so are cybercriminals

Online Safety and Privacy
Public Computers and Wi-Fi
Surf safe when using public computers and networks.

Online Safety and Privacy
What to Do if Your Password Manager Is Breached
What should you do if your password manager is breached?

Careers and Education
My Cyber Journey – Shawnte Arrington, Support, Technical Account Manager, Tanium
Meet Shawnte Arrington, Support, Technical Account Manager at Tanium

Online Safety and Privacy
What Is Data Privacy?
When you think of privacy, what comes to mind? Closing your window shades? Keeping your phone screen locked? Shutting the door when you have a sensitive conversation?

Online Safety and Privacy
10 Online Safety Tips for Gaming
Play safe while gaming.

Online Safety and Privacy
Dongles, Sticks, Drives, and Keys: What to Know About Removable Media
If you find a USB drive or other removable piece of media in the wild, DO NOT plug it into your computer! Let's break down why.

Online Safety and Privacy
How to Be an Online Privacy Snob
Take control of the data you share by being picky.

Online Safety and Privacy
Securing Your Home Network
A protected home network shuts out cybercriminals, allowing your family to use the internet more safely.

Cybersecurity for Business
Small Business Quick Wins
Follow these "quick wins" to secure every aspect of your small business.

Online Safety and Privacy
Online Shopping
Online shopping may be convenient but it can present many opportunities for scammers and cybercriminals.

External Resources
Best-Trade-Schools.net: Trade Schools Guide
As technology advances rapidly, becoming a Cyber Security Specialist is a smart and timely career choice. This booming field is projected to be worth over $10.5 trillion by 2023, playing a crucial role in safeguarding national security.
Online Safety and Privacy
Take Control of Your Data
All your online activity generates a trail of data.

Cybersecurity for Business
4 Simple Steps to Better Protect Your Company from Cyberattacks
Cyberattacks can happen to companies of all sizes.
Cybersecurity for Business
Advancing Collective Risk Management Efforts in the Financial Sector
The protection of our clients and customers from cyber threats is a foundational part of our business.

Cybersecurity for Business
The Security Culture Connection
Have you noticed the phrase “security culture” being used a lot recently? It’s become a bit of a security phrase de jour. That’s both a good thing and a bad thing.

Online Safety and Privacy
Only half of teens agree they "feel supported online" by parents
Not enough children and teenagers trust their parents to support them online, and not enough parents know exactly how to give the support their children need.

Cybersecurity for Business
6 Ways to Help Employees be Privacy Aware
Promote awareness about privacy, safeguard data and enable trust throughout the workplace with these tips.

Cybersecurity for Business
Cybersecurity awareness starts with people: Microsoft helps you and your team to #BeCyberSmart
Vasu Jakkal, CVP at Microsoft, emphasizes the importance of cybersecurity education for individuals and organizations.

Online Safety and Privacy
What About Password Manager Risks?
In the new Password Policy ebook, What Your Password Policy Should Be, KnowBe4 recommends that all users use a password manager to create and use perfectly random passwords.
Cybersecurity for Business
Cybersecurity collaboration as a national imperative
Bobbie Stempfley emphasizes the urgent need for a collaborative cybersecurity ecosystem to effectively combat the increasing frequency and severity of cyberattacks

Cybersecurity for Business
Building a Security Culture: The Foundation of a Secure Organization
Creating strong cybersecurity defenses for any organization requires a lot of important elements. Everyone knows a strong firewall is an essential first line of defense.

Careers and Education
My Cyber Journey – Jeremy Daniels, Cyber Analyst at HPE
Meet cyber analyst and HBCU grad, Jeremy Daniels.

Online Safety and Privacy
‘It’s easy to stay safe online’ with these 4 steps (plus 1)
When it comes to cybersecurity, good behavior can be rewarding.

Cybersecurity for Business
Making Cybersecurity Relevant for Consumers: The Case for Personal Agency
As Cybersecurity Awareness Month kicks off, one of the questions we often hear is “does consumer education really make a difference?”

Careers and Education
My Cyber Journey – Monique Head
Meet Monique Head, Founder of CyberTorial.org and Sr. Partner, Information Security, Communications, Awareness & Education at Netflix.

Online Safety and Privacy
Raising Digital Citizens
We all know the internet is a fantastic world of learning and entertainment for kids, but, like the real world, there can be dangers, too.

Careers and Education
Reinforcing Cybersecurity: Start with a Diverse Workforce
Looking to reinforce your company’s cybersecurity strategy? A good place to start is to cultivate a diverse workforce.

Online Safety and Privacy
Best Practices for Security and Privacy Settings
Want to lead a Stay Safe Online lifestyle, but don't know where to start?

Toolkits
Teach Others How to Stay Safe Online: Volunteer Toolkit
We're calling on all security professionals to share their expertise and volunteer to teach your community about online safety.

External Resources
Coursera: Developing a Program for Your Business Specialization
Master the Fundamentals of Cybersecurity. Learn to assess cyber threats and protect business information assets.
External Resources
Coursera: Introduction to Cyber Security Specialization
Cyber Security. An introduction to modern information and system protection technology and methods.

External Resources
LinkedIn Learning: Cybersecurity Foundations
Set a rock-solid foundation for your network, users, and data by learning about the basics of cybersecurity.

External Resources
Great Learning: Advanced Cyber Security - Threats and Governance
Learn solutions for cyber-attacks with Advanced Cyber Security-Threats and Governance free course

External Resources
Skill Share: Go From Zero to Hero
The field of technology is growing exponentially with the IT sector flourishing every day. Amidst such growth of the industry and increased concern for privacy, the demand for security is rising. Cybersecurity has become an everyday struggle for many businesses. Recent trends and statistics reveal that there is a huge increase in hacked and breached data from very common sources at workplaces. So go for this course to get a better understanding of cyber security!

Online Safety and Privacy
Password Managers
Don't pass on password managers. Learn more about these useful tools.

Careers and Education
How Free Pizza Led to a Cyber Career
A Chat with Bill.com’s Rinki Sethi

Online Safety and Privacy
You Can Stop Cyberbullying As A Kid!
As a kid using the internet, you've probably heard of cyberbullying. Maybe you or a friend has experienced it.

Online Safety and Privacy
The Modern Teen’s Guide to Handing Out L’s to Cyberbullies
Cyberbullying can make you feel like you can't really be "you" online. Here's what to do.

Online Safety and Privacy
Parents and Educators: What to Do About Cyberbullying
Have you ever texted or posted something online that you would never say to someone in person? You’ve probably experienced how the internet's anonymous nature can sometimes bring out the worst in people.

Online Safety and Privacy
10 Must-Know Tips For Keeping Your Personal Data Safe
The internet has become a vital aspect of our lives.

Cybersecurity for Business
Identity Management and the Second Half of the Chessboard
Ray Kurzweil's concept of the "second half of the chessboard" illustrates how exponential growth in technology and data management can lead to significant economic impacts and inefficiencies if not effectively managed.

Online Safety and Privacy
Secure Your Home
Internet-connected devices are helping homeowners increase efficiency, reduce costs, conserve energy and a whole host of other benefits.

Cybersecurity for Business
9 Security Questions Business Owners Must Ask Vendors
No matter the nature or size of your company, you need to think about cybersecurity in our connected present. This doesn't just mean your own operation's cybersecurity, but the security of every vendor you do business with.

Careers and Education
From Librarian to Cyber Pro
A Chat with the @InfoSecSherpa Tracy Z. Maleeff

Cybersecurity for Business
Cybersecurity: 3 Things Every Small Business Owner Should Know
Cyber attacks can be devastating, and they are increasingly common for small to mid-sized businesses.

Online Safety and Privacy
Respect Privacy
Respecting the privacy of your customers, staff, and all other stakeholders is critical for inspiring trust and enhancing reputation.

Cybersecurity for Business
Covid-19 Cybersecurity Resources for Small Businesses
To respond to the global pandemic and deliver timely information and resources to the nation’s small business community, the National Cybersecurity Alliance’s CyberSecure My Business program created the COVID-19 Small Business Cybersecurity Series.

External Resources
Additional Resources for Businesses
Frameworks, assessments, and guides from across the web.

Cybersecurity for Business
Identify Your “Crown Jewels”
Take an inventory of your business's most valuable assets.

Cybersecurity for Business
Protect Data and Devices
Secure the "crown jewels" of your business.

Cybersecurity for Business
Recover From Cyber Incidents
How to help your business recover from a cyber incident.

Cybersecurity for Business
Respond to Cyber Incidents
Do you have a plan in place to respond to cyber incidents at your business?

Cybersecurity for Business
Cybersecurity, It's More Than IT
As our lives become more digital, the risk of cybercrime grows, making strong cybersecurity measures essential not only for data protection but also for safeguarding customer information.

Careers and Education
Forestry Expert to Cybersecurity Manager: A Chat with Discover’s Sunil Mallik
Despite common perceptions, cybersecurity professionals come from all different walks of life.

Online Safety and Privacy
Talking to Kids & Teens about Security and Privacy
In today’s world, digitally connected families must think about safety and security both online and offline.
Online Safety and Privacy
Online Safety Tips For Older Adults
Just as you fasten your seat belt before driving, take precautions before using the Internet to be sure you are safe and secure.

Online Safety and Privacy
Parental Controls
As a parent, how do you stay involved in your child’s digital life?

Online Safety and Privacy
Talking to Kids and Teens about Security and Privacy
In today’s world, digitally connected families must think about safety and security both online and offline.
External Resources
American Indian Science & Engineering Society: AISES Membership
Opportunities and Resources for Native Students in STEM

External Resources
ApprenticePath: Discover Your Career Path
Jumpstart your career via paid apprenticeships

External Resources
Bold.org: Computer Science Scholarships
The Best Scholarships for Prospective Computer Science Professionals with Upcoming Deadlines

External Resources
The Center for Infrastructure Assurance and Security (CIAS): National Collegiate Cyber Defense Competition
Established in 2001 as part of UTSA’s creation of a cybersecurity program, the CIAS is a research center on a mission to secure the nation’s infrastructure and foster a Culture of Cybersecurity.
External Resources
Culture of CybersecuriTy: Kids Activities
The CIAS K-12 Cybersecurity Program is designed to introduce students to cybersecurity education and possible career paths in STEM disciplines, especially cybersecurity. To increase interest and learning capabilities, this initiative is centered around the CyBear™ family.

External Resources
Code.Org: Computer Science at Home
Anyone can learn Computer Science. Start coding today.

External Resources
Cyber.Org: Browse Free Cyber Curricula
CYBER.ORG empowers educators to teach cyber confidently, resulting in students with the skills and passion needed to succeed in the cyber workforce.

External Resources
Cyber.org: Cyber@Home
There is something here for everyone with fun, project-based activities for elementary, middle, and high school students.

External Resources
Fastport and Purdue University: Purdue Cyber Apprenticeship Program
These programs all provide earn and learn opportunities for participants with compensated experiential, effort-based employment and an industry-recognized educational component.

External Resources
CyberScient: Kids Platform
Share your successes and struggles with a community of like-minded students who share your artistic goals on our public forums.

External Resources
CyberDegrees.org: Cybersecurity Degrees
There are hundreds of different cybersecurity degrees.

External Resources
Cybersecurity Guide: K12 Cybersecurity Guide
If you are a young person interested in pursuing a career in technology, it can be challenging to know where to start. While some schools may offer curriculum in technology, cybersecurity isn’t typically covered.

External Resources
Girls Who Code: College Programs
Girls Who Code offers a wide range of programs designed to support college-aged students and early career professionals (18-25) in persisting in their computer science education and succeeding in their first internships and jobs.

External Resources
IKeepSafe: Faux Paw Cybersecurity Superheros activities
Meet Faux Paw, an adventurous six-toed cat who loves technology. These fun books teach rules to promote the safe and healthy use of digital devices. Read or watch Faux Paw’s adventures using links below each book’s description.

External Resources
IKeepSafe: Data Privacy Educator Training Course
Growing concerns about student data privacy can create hurdles for K12 educators working to expand access to edtech and digital innovations. EduPaths and iKeepSafe partnered to create four courses centered around data privacy in education.

External Resources
Microsoft: Microsoft Learn for Educators
Equip your students with AI and tech skills for today—and tomorrow

External Resources
Natives in Tech
Cultivate a tech ecosystem of Native technologists crafting free and open source technology for Native communities.

External Resources
National Initiative for Cybersecurity Careers and Studies: Cybersecurity in the classroom
Are you a Kindergarten through 12th grade (K-12) teacher or educator looking to incorporate cybersecurity into your lesson plans? Do you want to help your students learn about cyber concepts and career opportunities?

External Resources
National Initiative for Cybersecurity Careers and Studies: Veterans User Guide
Veterans and military personnel looking to transition out of the armed forces, are you ready for your next mission?

External Resources
Carnegie Mellon University: picoCTF.org
Watch our monthly YouTube lecture series on intro cybersecurity principles.

External Resources
Breaking Into Cybersecurity: Podcast by By Renee Small/Christophe Foulon
It’s a conversation about what you did before, why did you pivot into cyber, what the process you went through Breaking Into Cybersecurity, how you keep up, and advice/tips/tricks along the way.

External Resources
GenCyber: GenCyber Camps
GenCyber provides cybersecurity experiences for students and teachers at the secondary level.

External Resources
Roadtrip Nation: Information Security Engineers Career
Information Security Engineers Career Pathway

External Resources
Cyber Center of Excellence (CCOE): Cyber Center of Excellence (CCOE) Cyber Career Map
Chart your personal path to a cyber career with the exploration dashboard and zoom in for jobs, education, resources and much more.

External Resources
Salesforce: Cybersecurity Learning Hub
Learn in-demand skills and build your cybersecurity career path

External Resources
Temple University: Organizations We Love
These are the amazing 309 organizations that strive to make tech and info/cybersecurity opportunities and experiences accessible to everyone [1,2,3], and so they are the Organizations We Love (OWL)
External Resources
Temple University CARE Lab: Collegiate SECTF competition
The CARE Lab hosts social engineering competitions every summer! This event is open to high school, undergraduate, and graduate students. We partner with industry, government, and nonprofits to provide students with the best possible experiences and exposure to real world events.

External Resources
SMARTFENSE – Videojuegos educativos: Las aventuras de Gupi
Las Aventuras de Gupi es un videojuego lanzado por SMARTFENSE en el cual un pez llamado Gupi necesita la ayuda del usuario para no morder el anzuelo.

External Resources
Palo Alto Networks: Cyber A.C.E.S. Program
Cyber A.C.E.S. provides the cybersecurity basics students need to have safer online experiences and become good digital citizens. Lessons are designed so they can be facilitated by anyone, regardless of their knowledge level, with each module tailored to a specific age group.

External Resources
Code.org: Code Break
A weekly challenge to engage students of all abilities, even those without computers.

External Resources
TryHackMe: Cyber security Training
Learn cyber security with fun gamified labs and challenges

External Resources
Women’s Society of Cyberjutsu (WSC): Career Resources
The Women’s Society of Cyberjutsu (WSC), a 501(c)3 non-profit, is dedicated to raising awareness of cybersecurity career opportunities and advancement for women in the field, closing the gender gap and the overall workforce gap in information security roles.

External Resources
Symantec and AAUW: STEMpack: Cyber Security
Cyber Security curriculum to inspire and introduce participants to cyber security and computer science.
External Resources
CISA: Cybersecurity Workforce Training Guide
Released August 2021, the Cybersecurity Workforce Training Guide is for current and future federal, state, local, tribal, and territorial (SLTT) staff looking to expand their cybersecurity skills and career options.

External Resources
Center for Internet Security: Why Consider a Career in Cybersecurity?
As technology evolves and cybersecurity threats continue to grow, the need for qualified cybersecurity candidates only intensifies. But it's not always easy to fill these positions. That's why starting a career in cybersecurity is worth considering, especially for students or individuals who are looking for a career change.

External Resources
CompTIA: State of the Tech Workforce
CompTIA’s State of the Tech Workforce, also known as Cyberstates, provides the definitive guide to tech workforce trends, the number of available jobs in technology, and tech industry employment statistics by state, metro area and nationwide.

External Resources
C.A.K.E: Cyber Academy For Kids through Empowerment
CAKE - Cyber Academy for Kids through Empowerment - Founded by two industry professionals in the field of cybersecurity and information technology is teaching elementary, middle and high school students the fundamentals of cybersecurity.

External Resources
Cybersecurityjobs.com Training Fund
Our mission is to connect cybersecurity professionals with organizations in need of cybersecurity talent but putting people and employers together is just one side of the equation.
External Resources
Cyber Seek
CyberSeek provides detailed, actionable data about supply and demand in the cybersecurity job market.

External Resources
Cyber Virginia: VIRGINIA VETERANS CYBER TRAINING PILOT
In an effort to address the growing demand of over 17,000 cyber jobs available across the state of Virginia, organizations have joined together with the Commonwealth of Virginia to sponsor free cyber training and industry-recognized certifications as part of a pilot program for veterans who want to live and work in the Commonwealth in the cyber field.

External Resources
Cybrary: Cybersecurity Training and Career Development
Cybrary’s structured, hands-on cybersecurity courses and training empowers professionals to better protect their organizations.

External Resources
Cyversity
To achieve the consistent representation of women, underrepresented communities, and all veterans in the cybersecurity industry through programs designed to diversify, educate, and empower.

External Resources
Empow(H)er Cybersecurity
The goal of Empow(H)er Cybersecurity is to provide a platform for all women of color to grow their networks, be inspired, and feel empowered.

External Resources
ESET: Women in Cybersecurity Scholarship
Two $10,000 scholarships will be awarded to graduate/undergraduate women pursuing a career in cybersecurity.

External Resources
Fortinet: Veterans Program
Transitioning the military community into the cybersecurity industry through world class training.

External Resources
Future Learn: Cybersecurity Courses
Explore online criminal activity and undergo cyber security training to protect yourself and others online, or prepare for a career in cyber security.

External Resources
Girl Scouts: Ambassador Cybersecurity Safeguards Badge: Guard Your Movements
Identify data vulnerabilities in a typical day

External Resources
Girl Scouts: Brownie Cybersecurity Basics Badge Activity: Tech Scavenger Hunt
Do a scavenger hunt to explore how technology replaces everyday objects.

External Resources
Girl Scouts: Cadette Cybersecurity Safeguards Badge Activity: Inventory Your Digital Presence
Explore some of the types of data collected by websites and apps.

External Resources
Girl Scouts: Daisy Cybersecurity Basics Badge Activity: Protect Your Treasure
Explore how to keep something safe, like a computer, with layers of protection.

External Resources
Girl Scouts: Junior Cybersecurity Basics Badge Activity: Roll with Protocols
Explore how computers send and receive information when sending messages.

External Resources
Girl Scouts: Senior Cybersecurity Basics Badge Activity: Identify Functions and Privileges
Explore how cybersecurity professionals keep computer networks safe.

External Resources
Hacker Highschool
Hacker Highschool (HHS) started in 2003 as a means of teaching teens problem solving, resourcefulness, and empathy through hacking.

External Resources
Center for Cyber Safety and Education: Scholarships
The scholarships are part of an effort to bridge the cybersecurity workforce gap by providing future cybersecurity professionals across the globe with scholarships to prepare them for a rewarding career in this important field.

External Resources
(ISC)2: Webcast series
ISC2 produces complimentary webinars with high-quality content on an ongoing basis. Advance your knowledge on emerging issues and stay up-to-date on global trends and hot-button topics.

External Resources
NICE K12 Cybersecurity Education Conference
The NICE K12 Cybersecurity Education Conference is the premier event for K-12th grade cybersecurity educators.

External Resources
Microsoft: MakeCode
Microsoft MakeCode is a free online learn-to-code platform where anyone can build games, code devices, and mod Minecraft!

External Resources
National Cyber Scholarship Foundation
The initiative is designed to identify talent in high school and college students, and includes a comprehensive set of programs and supports that work together to create a more assured pipeline for building the next generation of cyber talent.

External Resources
NextGen CyberTalent: NextGen Candidate Programs
NextGen Cyber Talent conducts a cohort every month to educate and train underserved, underprivileged and diverse talents in Cybersecurity, risk, and compliance domains.

External Resources
National Initiative for Cybersecurity Education: Cybersecurity Career Awareness Week
Cybersecurity Career Week is a campaign to promote the discovery of cybersecurity careers and share resources that increase understanding of multiple learning pathways and credentials that lead to careers.

External Resources
National Initiative for Cybersecurity Education: Free and Low Cost Online Cybersecurity Learning Content
The following links are for free and low-cost online educational content on topics such as information technology and cybersecurity

External Resources
NICE: The Challenge of That First Job in Cybersecurity – Entry Level Roles and How to Qualify
This webinar will explore the unique challenges and opportunities from the perspective of educators, employers, and job-seekers.

External Resources
Palo Alto Networks: Cybersecurity Academy
World-class curriculum and programs specifically designed for K-12, colleges and universities.

External Resources
Palo Alto Networks: Certified Cybersecurity Entry-Level Technician (PCCET) program
The PCCET certification covers fundamental cybersecurity, network security, cloud security, and SOC security principles.

External Resources
PBS: The Cybersecurity Lab
Whenever we go online—to shop, chat with our friends, or do anything else—we put ourselves at risk of cybercrime. Computer viruses can corrupt our files, hackers can steal our data, and criminals can trick us into revealing sensitive information. But luckily there are simple steps we can take to protect our digital lives.

External Resources
RangeForce: Cybersecurity Training
Take your cyber skills to the next level. Access a limited number of hands-on cybersecurity training modules for free, forever.

External Resources
SANS: Diversity Cyber Academy
Facing the cybersecurity challenge, SANS Diversity Cyber Academy offers cybersecurity training scholarships for minorities and women.

External Resources
SANS Institute: Free Cyber Security Training
Learn the Fundamentals of Cyber Security for Free!

External Resources
Scholastic: #CyberSmarts
As your kids discover the power of the internet, make discussing the do’s and don’t’s of online behavior a priority.

External Resources
Tynker: Coding for Kids
Tynker is the fun way to learn programming and develop problem-solving & critical thinking skills.

External Resources
US Cyber Challenge
USCC’s goal is to find 10,000 of America’s best and brightest to fill the ranks of cybersecurity professionals where their skills can be of the greatest value to the nation.

External Resources
Katzcy: US Cyber Games
The mission of the US Cyber Games® is to bring talented cybersecurity athletes, coaches, and industry leaders together to build an elite US Cyber Team for global cybersecurity competition.

External Resources
Air Force Association: Elementary School Cyber Education Initiative
The CyberPatriot Elementary School Cyber Education Initiative (ESCEI) is a set of three fun, interactive learning modules aimed at increasing grade K-6 students’ awareness of online safety and cybersecurity principles. Supplemental activities are also available to get students collaborating with each other about their newly learned cyber skills!
External Resources
Varonis: Which Cybersecurity Career Is Right For Me?
Finding the right career path in the cybersecurity industry isn’t always easy. We interviewed cybersecurity experts to find out what inspired them!

External Resources
University of Washington: Access Computing Team
AccessComputing helps students with disabilities pursue degrees and careers in computing fields through inclusive academic and mentoring programs.

External Resources
Black Girls Code
Since 2011, Black Girls Code has supported girls of color in tech through coding education and more. We partner with schools and organizations to offer a range of programs, both in-person and virtual, for ages 7-25.

External Resources
Women in Security and Privacy
We are advancing women and underrepresented communities to lead the future of security and privacy.

External Resources
Kalinda Raina: Raising the Digital Future
Let's talk real world solutions for raising children in a world where every bad decision they make will exist on the Internet for any curious college admission counselor or job recruiter to find.

External Resources
CompTIA: Cybersecurity: Skills, Tips, and Advice From Our Panel of Experts
CompTIA has brought together a panel of cybersecurity experts to share their knowledge and experience with seasoned IT pros and those interested in starting a career in cybersecurity.

Online Safety and Privacy
COVID-19 Security Resource Library
Free resources to help individuals and organizations through the COVID-19 pandemic.

Toolkits
Cyberbullying
Cyberbullying can range from embarrassing or cruel online posts or digital pictures, to online threats, harassment, and negative comments, to stalking through emails, websites, social media platforms and text messages.

Online Safety and Privacy
Malware, Viruses and Botnets
These 3 types of cybercriminal tools are common online, and you as an internet user might come across them from time to time.

Online Safety and Privacy
Security Awareness Episodes
Watch and download this fun series on security best practices!

Cybersecurity for Business
Did You Notice a Shift in Attitudes Towards Awareness Training at This Year's NCA Conference?
Mike Polatsek, Co-founder and CSO at CybeReady, reflects on Convene: Florida.

Cybersecurity for Business
Top 10 Security Issues in Enterprise Cloud Computing
As a CISO, you know the list of security issues in enterprise cloud computing seems to always be growing.

Careers and Education
Tech Lover...but Cyber Late Bloomer
A Conversation with Prajakta "PJ" Jagdale of Palo Alto Networks

Online Safety and Privacy
Is working on your smartphone a risky business or are you cybersecure?
The increasing use of mobile devices in our personal lives has led to a growing acceptance of smartphone usage at work.

Online Safety and Privacy
Stalkerware
BEFORE YOU CONTINUE: Stalkerware apps can track your browsing history so if you suspect that stalkerware has been installed on your device DO NOT USE IT to research support services such as advocacy, shelter, court information or emergency services.

Online Safety and Privacy
Tips for Higher Education Online Teaching and Learning
As online and hybrid learning environments become more popular, it is essential for students, faculty, and staff to adopt key cybersecurity practices.
Online Safety and Privacy
K-12 Online Learning
Online learning is here to stay. Many K-12 schools will probably use some blend of fully online learning and in-person teaching for the foreseeable future.

Online Safety and Privacy
Mobile Devices
That smartphone in your pocket, that tablet on your coffee table or that laptop on your desk contains a treasure chest of information about you, your friends and your family.

Online Safety and Privacy
A Teacher’s Guide To Student Online Safety
Students are more connected than ever before thanks to the internet.

Careers and Education
Lawyer, Children's Book Author, and Career Changer to Cybersecurity
Meet Zinet Kemal

Cybersecurity for Business
Human Challenges in Implementing Multifactor Authentication (MFA)
How to implement an effective MFA program in your business.

Cybersecurity for Business
How Smart Card Technology Uses Network Security
The concept of network security has been in existence for decades. With organizations using more sensitive information, the need to create policies that would limit access and control of a network has increased.

Online Safety and Privacy
7 Tips for a Safer Internet of Things
The "Internet of Things" (IoT) has been a realm of technological innovation that has grown exponentially over the past decade.

Cybersecurity for Business
As an Employee or a Business Owner, You Need to Be Cyber Aware and Resilient
As our world becomes increasingly connected, it’s more important than ever to be cyber aware. There’s no question, cyber attacks are evolving in sophistication and attackers are broadening the entities they’re willing to target.

Cybersecurity for Business
The Top Cybersecurity Trends for 2022
Here are the top three cybersecurity trends we think are worth watching as we approach 2022

Online Safety and Privacy
Be Cyber Smart: A guide to help you do your part
Let’s brush up on cyber hygiene — basic steps we can take to stay safe in a connected world.

Cybersecurity for Business
5 Cybersecurity Trends in 2021
As remote work becomes the norm post-COVID-19, the cybersecurity landscape is evolving rapidly, presenting new threats and necessitating a reassessment of strategies to protect organizations from increasingly sophisticated attacks.

Careers and Education
From math-hater to DEFCON-lover: An unlikely path to Cybersecurity
Would you let a fear of math scare you away from a career in cybersecurity?

Online Safety and Privacy
Reporting Matters – even for a Smishing Message
With the increased use of mobile devices to manage so much of our lives, it’s no surprise scammers have moved to this medium to target your sensitive information.

Online Safety and Privacy
7 Tips to Manage Your Identity and Protect Your Privacy Online
Worried about how much of your private information is on the internet and vulnerable to theft or misuse? You’re not alone.

Online Safety and Privacy
Spotting a Vaccine Phishing Scam: Can You Find the Red Flags?
Many of us have seen COVID-related scams hit our inboxes. It’s no secret that scammers try to take advantage of times of panic and uncertainty, when people are most vulnerable, to steal personal information.

Online Safety and Privacy
Take It Personally: Ten Tips for Protecting Your Personally Identifiable Information (PII)
When we're online, we accumulate a significant amount of personally identifiable information (PII), which can be exploited by cybercriminals.

Cybersecurity for Business
The Impact of Data Breaches and Cyberattacks on SMBs and Their Employees
It is always important for businesses to ensure their employees work securely, both at the office and home, as threat actors continually look for ways to attack.

Cybersecurity for Business
How to Run a Virtual Cybersecurity Awareness Month Campaign
Engage your employees online during Cybersecurity Awareness Month.

Online Safety and Privacy
Security Awareness: Episode 4 – Phishing and Ransomware
We’re bringing you another free security awareness video! These videos are brought to you by Adobe, National Cyber Security Alliance, and Speechless Inc.

Online Safety and Privacy
Owning Your Privacy by Managing Your Digital Footprint
The information you share online can reveal more details then you intend and make you vulnerable to compromise.
Online Safety and Privacy
How to Secure and Maintain Your Digital Identity
Individuals must take proactive steps to safeguard their digital identities by being cautious about personal information sharing, connection requests, and message links.

Online Safety and Privacy
Sextortion: What to Look Out For and What to Do If You’re a Victim
An explanation of sextortion and how it works.

Cybersecurity for Business
How Your IT System Could Be at Risk from a Physical Attack
Don't overlook the physical risks to your IT system.

Online Safety and Privacy
The Secret Language of Emoji
Emoji appeared in 1999 with a set of 176 symbols that were meant to convey weather, traffic, technology and time. Today, there are 2,823 emoji that convey information across language, culture, lifestyle and diversity.
Cybersecurity for Business
You’ve Been Hacked: 5 Ways to Minimize the Damage
Getting hacked is a nightmare scenario for every business. Fifty percent of small businesses in the U.S. have experienced a cyberattack. And this fact is not surprising – most small businesses lack the advanced security resources and technology that large enterprises can afford.

Online Safety and Privacy
Stay Secure On Public Wi-Fi When Traveling
Twink twice before connecting to a public wi-fi network when you're on the go.

Online Safety and Privacy
Protecting Baby Monitors From Hacking
The use of Wi-Fi-capable baby monitors has become indispensable to many parents.

Cybersecurity for Business
How to Protect Your Customer Relationship Management (CRM) Data from Hackers
CRM systems are some of the most useful assets for an organization, enabling businesses to build meaningful customer relationships, find new prospective customers and drive revenues.

Online Safety and Privacy
Security and Privacy Tips for Cryptocurrency Holders
The cryptocurrency trend is definitely a big boom in today’s financial market.

Online Safety and Privacy
Data Privacy Is Crucial for the LGBT Community
It is vitally important to consider how compromised online privacy can specifically affect marginalized groups such as the LGBT community.

Online Safety and Privacy
Health Technology in the Digital Era – Benefits + Risks
Examining the evolution of health technologies and their implications for patient privacy and security.

Online Safety and Privacy
Health Information Privacy – Why Should We Care?
Recent data breaches involving health information pose significant risks to our online privacy. Learn how to protect your valuable health data.

Online Safety and Privacy
15 Online Security + Privacy Tips for College Students
You’re responsible for your own online security at college, so follow these tips to help you be safe and privacy-savvy on campus.

Cybersecurity for Business
Key Ways to Protect Your Business From Malware
Cyberattacks are a serious threat to businesses and consumers, with large-scale attacks having nationwide effects, thus making national security a serious concern.

Cybersecurity for Business
What Happens When Cyberbullies Join the Workforce?
Cyberbullying has been stereotyped in the media as a problem that occurs with teenagers, cell phones, sexualized photographs and social media.

Online Safety and Privacy
What Is Smishing? How Text Message Scams Work (And How To Avoid Them)
Cybercriminals love to go smishing, but you don’t have to take the bait.

Online Safety and Privacy
What Are Common Crypto Scams?
Cryptocurrency investment scams are big business, but you can keep your wallet safe.

Online Safety and Privacy
Are Passwords Going Away? What You Need to Know About Passkeys
The future of logging in is already on your phone!

Online Safety and Privacy
10 Reasons Why You Need to Be At Convene: Cleveland
If you work at the intersection of people and security, then you got to join us this summer in Cleveland for our Convene conference.

Online Safety and Privacy
Is Microsoft Doing Away With Passwords?
If you use Microsoft Authenticator to store passwords, they will be deleted in August.

Cybersecurity for Business
How You Can Help Secure Smaller Vendors with Limited Budgets and Know-How
If you work in third-party risk management (TPRM), you face a growing challenge: how to keep your supply chain secure when many vendors are small businesses with limited cybersecurity resources?

Cybersecurity for Business
Your Business Has Been Hacked: How to Minimize the Damage
If your small business has been hacked, you need to act fast. Here are some key things to know to fight back, stay open, and build resilience in the event of a cyberattack.

Cybersecurity for Business
Why Physical Security Is Still Necessary for Cybersecurity
Physical security is an essential, but often overlooked, factor in cybersecurity.

Toolkits
Best Vacation and Travel Cybersecurity Tips
Whether you're lounging on a beach or hiking through the mountains, these days, you probably stay connected during your trip.

Cybersecurity for Business
How to Protect Your Small Business from Malware
Malware attacks, including ransomware, are one of the most common threats facing small businesses today.

Cybersecurity for Business
Best Practices for Protecting Your CRM Data
Your customers are the lifeblood of your business and their data is extremely valuable.

Online Safety and Privacy
Tread Lightly Online: How to Check and Manage Your Digital Footprint
While you can’t use the internet completely undetected, you can manage your digital footprint and protect your data privacy. Find out more using our guide.

Online Safety and Privacy
6 Cybersecurity Myths Debunked
There are a lot of myths flying around about cybersecurity. We’ll go over the most common cybersecurity myths and debunk them so we can stay safer online.

Online Safety and Privacy
Cyberbullying in the Workplace: How to Recognize, Address, and Prevent It
Cyberbullying is often associated with teenagers and social media, but some bullies grow up...and enter the workforce.

Online Safety and Privacy
Does AI Take Your Data? AI and Data Privacy
Generative AI, including platforms like ChatGPT, DALL-E, Google Gemini, Apple Intelligence, has revolutionized our relationship with technology.

Online Safety and Privacy
Why Your Family and Coworkers Need a Safe Word in the Age of AI
Scammers always rely on deception to trick people out of their money, but the sudden wide availability of artificial intelligence has increased the convincingness of their schemes.

Toolkits
AI Fools: Stay Sharp!
An awareness campaign on AI-enabled scams & responsible AI use.

Online Safety and Privacy
How to Update Your Software
An easy way to boost your cybersecurity is to always keep software and apps updated.

Online Safety and Privacy
What Is Phishing and How To Avoid It
Cybercriminals love to go phishing, but you don't have to get hooked.

Careers and Education
How To Write a Cyber Resume and LinkedIn That Gets Results
If you're hunting for a job in cybersecurity, you're aware that your resume and LinkedIn profile are critical to getting hired in this competitive field. But how do you create a resume that gets noticed?

Online Safety and Privacy
How to Stop the Flow of Personal Data with Cloaked CEO Arjun Bhatnagar
It’s Data Privacy Week, when we pay special attention to why data privacy is so critical in today’s world.

Online Safety and Privacy
Cybersecurity for Tax Season: Protect Your Identity and Refund
Tax season brings enough stress without adding scammers to the mix. But the reality is that criminals ramp up attacks in the first few months of the year, often impersonating the IRS or trusted services like H&R Block and TurboTax.

Careers and Education
Cyber Groups with Local Chapters You Can Join Today!
Cybersecurity is a community, even if it might not always feel like it with your nose buried in your laptop.

Online Safety and Privacy
What is Multifactor Authentication (MFA) and Why Should You Use It?
You can protect your online accounts with more than just a password.

Online Safety and Privacy
Stay Secure While Job Hunting
When looking for new opportunities, follow these simple steps to protect yourself from fraud.

Online Safety and Privacy
Use Apps and Software to Protect Your Data
Our data is constantly collected and shared, and we often don't even know all the types of data being gathered.

Online Safety and Privacy
Create and Use Strong Passwords
Passwords are the keys to safeguarding your digital and online life. They are your first line of defense. And knowing how to create and store strong passwords is one of the most critical aspects of everyday cybersecurity.

Online Safety and Privacy
What is Data Privacy and Why Should You Care?
Data Privacy Week is January 27 - 31, 2025!

Online Safety and Privacy
Cybersecurity Predictions for 2025: Challenges and Opportunities
The year 2024 was a whirlwind year for cybersecurity. From the fallout of high-profile ransomware attacks to the increasing commoditization of AI tools, the challenges kept mounting.

Online Safety and Privacy
Chinese Telecom Hack: How to Protect Your Messages
Learn how to protect your calls and texts following the Chinese telecom cyberattack with simple tips like using encrypted apps.

Online Safety and Privacy
How to Avoid Scams and Fraud
Online scams are becoming increasingly sophisticated, targeting people of all ages. But with some knowledge, you can protect yourself and your loved ones.

Online Safety and Privacy
Avoid Gift Card Draining Scams This Holiday Season
Gift cards make for easy, versatile gifts, especially during the busy holiday season. But they’re also prime targets for scammers who use "gift card draining" to steal funds before the recipient can even use the card. Let’s break down how these scams work and how you can stay safe.

Cybersecurity for Business
How to Make Cybersecurity Training Accessible
Does your training program reach all employees in your organization?

Online Safety and Privacy
What is Pig Butchering and How to Spot the Scam
"Pig butchering" is a scam that's been muscling into the headlines lately.

Toolkits
Oh Behave! The Annual Cybersecurity Attitudes and Behaviors Report 2024
Each year, the National Cybersecurity Alliance releases research to better understand the public’s security behavior and to act as a call to action for better secure habits online.

External Resources
KnowBe4 Children’s Interactive Cybersecurity Activity Kit
Looking for a way to talk about online safety and security with your children? KnowBe4 provides a fun and interactive cybersecurity kit to help you teach them valuable online safety and security skills.

Online Safety and Privacy
Did Hackers Steal Every Social Security Number? Here's What To Do.
Learn how to protect your social security number.

Careers and Education
The Evolution of Ethical Hacking: From Curiosity to Cybersecurity
The term "ethical hacking" was coined in 1995 by IBM Vice President John Patrick, but the practice itself has roots that stretch back much further.

Online Safety and Privacy
Data Breaches Slim Down Your Wallet
Data breaches are becoming an expensive predicament for all of us, even if your data isn't directly stolen in a breach.

Online Safety and Privacy
When Websites Make It Hard to Cancel...
Some websites and apps are designed to be manipulative – they make it hard to cancel a recurring subscription, obscure the fact that you will be charged, or hide the unsubscribe button.

Online Safety and Privacy
Watch Out for EBT Scams
Scammers target some of the most vulnerable.

Online Safety and Privacy
Protect Your Credit Cards from Skimmers and Shimmers
You can be a target of credit card skimming when you least expect it.

Careers and Education
How to Be an Awesome Cyber Mentor
Help close the cyber workforce gap by mentoring the next generation.

Careers and Education
How to Find a Mentor
Begin your career in cyber with the help of a mentor.

Online Safety and Privacy
Backups
Our digital devices contain vast treasure troves of data, from family photos and music collections to financial data, health records and personal contacts.

Online Safety and Privacy
When Scammers Call Grandma
"Your grandson has been arrested and needs bail money." "Your granddaughter was at fault in a car crash, and you need to pay the other driver's medical bills." What do you do if you receive these calls?

Online Safety and Privacy
Don’t Scam Me Right Now, I’m Trying to Buy a Home
How scammers try to trick home buyers and sellers.

Online Safety and Privacy
What To Do If Your Identity Is Stolen
With data breaches seemingly happening every week, more and more people are victims of identity theft.

Online Safety and Privacy
5 Common Real Estate Scams You Need to Know About
Since every real estate transaction involves a significant sum of money, anyone in the home market today will likely run into scammers on the prowl.

Online Safety and Privacy
Online Safety Basics
With a little prep, you can shield your information online and secure your digital systems and devices.

Online Safety and Privacy
Securing Smart Speakers and Digital Assistants
Smart speakers and digital assistants like Amazon Echo, Google Nest, Apple HomePod, and Sonos Era are integral to many modern households.

Online Safety and Privacy
How Data Breach Fatigue Can Impact Your Digital Health
When you hear your sensitive data was lost in another data breach, is exhaustion your first reaction?

External Resources
Stay Safe Online — Related Links
Here are helpful links from the National Cybersecurity Alliance’s sponsors, partners and friends to help you and your friends and family be safer and more secure online.

Online Safety and Privacy
Reporting Cybercrime
The first step toward bringing cybercriminals to justice is reporting cybercrime when it happens.

Cybersecurity for Business
What to Do if Your Business Facebook Is Hacked
There has been an uptick in cybercriminals attempting to target small businesses' Facebook profiles and ad accounts.

Online Safety and Privacy
Manage Your Privacy Settings
Direct links to manage your privacy settings on popular platforms and apps.

Online Safety and Privacy
How to Restore an MFA Authenticator App
Authenticator apps for multi-factor authentication (MFA) significantly enhance security but users must prepare for potential access loss due to device changes or loss by establishing recovery options and backups.

Online Safety and Privacy
Getting Kids & Teens to Care about Cybersecurity
We all know Kids & Teens today spend a lot of time online, but that doesn't necessarily mean they know how to stay safe.

Online Safety and Privacy
Getting Kids and Teens to Care about Cybersecurity
We all know kids and teens today spend a lot of time online, but that doesn't necessarily mean they know how to stay safe.

Online Safety and Privacy
Guard your Gateway: Internet Router Tips
While internet routers aren't as flashy as the latest VR headset or electric truck, they make internet access in our homes and businesses possible.

Cybersecurity for Business
How to Improve Your Cyber Resilience
We often think of cybersecurity in terms of our physical health—we talk about computer viruses and cyber hygiene. Cyber resilience is another way to think about your online fitness.

Online Safety and Privacy
SIM Card Swap Scams
Protect your phone from this increasingly common scam.

Careers and Education
8 Awesome Cybersecurity Careers
Explore the diverse landscape of careers in cybersecurity!

Toolkits
Cyber Survival Guide
The spirit of adventure beckons you online!

External Resources
Cyber Career Pathways Tool - NICCS
NICCS is the premier online resource for cybersecurity training, education, and career information.

Online Safety and Privacy
Spring Clean Your Online Life
A sloppy digital life can make your data harder to find and leaves your personal information vulnerable to bad actors. With a few steps, you can keep yourself and your family safe online with a squeaky clean digital life.

Cybersecurity for Business
Identity Management? Zero Trust? PIM? Succeed by Getting the Basics Right.
In today’s rapidly evolving online landscape, terms like zero trust, PIM (or Privileged Identity Management), and a series of other acronyms can leave the average person scratching their head.

Online Safety and Privacy
Protect Your Wallet from Payment App Scams
"I made a typo and accidentally sent you $3,000! Can you please send it back?"

External Resources
Interactive Cybersecurity Career Map - NICCS
Are you interested in entering the cybersecurity workforce or advancing your career? Explore thousands of federal cybersecurity job openings across the country and outside of the United States by clicking on the map below or using the drop-down menu. Select an area to find open cybersecurity positions in your preferred city, state, country, and salary range.

Cybersecurity for Business
Churning the Digital Waters: Insights from the 2023 Gone Phishing Tournament
Even as our online worlds become more complex, phishing schemes remain the most common type of cybercrime, according to the FBI.

Cybersecurity for Business
Mandate MFA: Take a Bold Step Toward a Secure Future
Making online platforms, services, and devices more secure by default is a good idea. But is it easy? Is it popular?

Online Safety and Privacy
Lessons from Data Privacy Week 2024
Data is now a valuable commodity.

Online Safety and Privacy
Avoiding Voting Scams and Safeguarding Elections
Elections are a cornerstone of American society. However, there are bad actors who don't respect the sanctity of our voting process.

Online Safety and Privacy
Protecting Our Kids' Data Privacy is Paramount
Protecting our children's online data is of utmost importance.

Toolkits
Online Dating and Romance Scams
Love is in the air and online, but so are cybercriminals.

Online Safety and Privacy
Connected Car Cybersecurity: Drive Safe Online
Cars have joined the Internet of Things, and with any connected device, you should follow some security best practices to keep your car's system safe.

Online Safety and Privacy
Safeguarding Your Internet Activity with Incognito Mode
We'll explore how incognito mode works, how it can help protect your browsing data, and, importantly, ways it isn't a magic solution to all your privacy concerns.

Cybersecurity for Business
8 Biggest Small Business Cybersecurity Misconceptions
Small businesses are crucial to the American economy, employing nearly half of the workforce, yet they remain prime targets for cyberattacks.

Online Safety and Privacy
How to Protect Yourself Against Deepfakes
Deepfake technologies can be used to steal your identity even if you don’t use generative AI platforms.

Cybersecurity for Business
No Weak Links: Think About Your Human Firewall
When it comes to fostering a culture of cybersecurity at your organization, sometimes it's best to start with creating awareness of some basic behavior changes.

Online Safety and Privacy
What to Know About Stalkerware
Even though the use of stalkerware to spy on adults is against the law, these duplicitous bits of code still pop up on app stores.

Cybersecurity for Business
Business Email Compromise: What It Is and How to Prevent It
While it has a bland name, Business Email Compromise (BEC) refers to a specific, nasty type of cyberattack that targets businesses of all sizes.

Cybersecurity for Business
Consider Cybersecurity in Your Investment Decisions
As cyberattacks become increasingly frequent and sophisticated, investors have a crucial role in urging companies to prioritize cybersecurity alongside other risk factors.

Online Safety and Privacy
How to Take Back Control of a Social Media Account
Responding to social media account takeover.

Cybersecurity for Business
Securing Success: Talking to the Board About Cyber Risk
Cyber risk across all business levels influences operations, reputation, and compliance.

Online Safety and Privacy
Traveling Securely: A Comprehensive Guide to Protecting Your Digital Footprint While on the Move
Technology accompanies us everywhere these days, and that includes traveling for work. Cybersecurity remains paramount even when you are thousands of miles away from the office.

Online Safety and Privacy
The Benefits of Using a Random Password Generator for Safer Online Access
One way to ensure your passwords are awesome is by using random password generators, often included with password managers.

Cybersecurity for Business
How Cyber Education for Employees Safeguards Your Business
Training employees is the cheapest, easiest way to boost your cybersecurity. Your employees are your first line of defense against as threats, and they are also your greatest asset.

Cybersecurity for Business
The City Secure: Cyber Tips for Local Governments
City governments operate in an increasingly connected world where city services, constituent services, and information sharing are online, digital, and shared on many platforms.

Toolkits
Safe Online Holiday Shopping
Watch out for online shopping scams around the holiday season!

Online Safety and Privacy
Extra! Extra! Avoid Fake News!
What is Misinformation, Disinformation, and Malinformation?

Cybersecurity for Business
Keep Your Business Safe and Connected With IoT
We're living in an era when everything connects to the internet, from your fridge to your car.

Online Safety and Privacy
Securing Higher Ed: 5 Tips for Learning Safe Online
Technology and academia are now seamlessly intertwined. While tech can further educational opportunities for students, it also comes with risk as the ivory tower delves into the Wild West of the internet.

Online Safety and Privacy
Oh Behave! The Annual Cybersecurity Attitudes and Behaviors Report 2023
STUDY: 37% Intimidated, 39% Frustrated with Online Security Highlighting Digital Anxiety

Online Safety and Privacy
Don't Blame the Victim: 'Fraud Shame' and Cybersecurity
There is often a culture of blaming fraud victims for their predicament, rather than focusing on the criminal and the crime.

Cybersecurity for Business
How to Prevent and Recover from Ransomware
Ransomware is a hack with teeth, an attack aimed to cause extreme financial pain to its victims.

Online Safety and Privacy
How Your Phone Number is Exposed: Phone Number Leaks
Your phone number counts as personal data, and you don't just want anyone out on the internet to have it.

Online Safety and Privacy
K-12 Cybersecurity: Keep Kids Secure from Kindergarten to Graduation
Nowadays, kids aren't just polishing apples and stuffing their bookbags before heading to school, they're firing up laptops and using video chat with their teachers.

Online Safety and Privacy
Share with Care: Staying Safe on Social Media
Hey, friends, followers, lurkers, and posters: you don't have to overshare!

Online Safety and Privacy
Pull the Shades Down on Your Browsing With a VPN
Did you know that your cruise around the internet every day might not be totally private?

Cybersecurity for Business
Sell Safe Online: Advice for Online Retailers
Be open for business and closed to cybercriminals.

Online Safety and Privacy
What To Do When Your Data Is Breached
Oh no! You’ve been notified that your sensitive information has been stolen in a data breach.

External Resources
KC7 Cyber: Cybersecurity Training
By playing through dozens of realistic cybersecurity intrusions you will progressively learn how to spot traces of malicious activity.

Cybersecurity for Business
Common Cybersecurity Misconceptions Held By Small and Medium-Sized Organizations
Employees empowered with the resources and knowledge to protect your organization from cyberthreats is one of the best lines of defense you can have.

Cybersecurity for Business
Detect Incidents
How to detect a cyber incident in your business.

External Resources
Helpful Resources for SMBs
Here are helpful links from our sponsors, partners and friends to help you keep your business secure.

Online Safety and Privacy
What LGBTQ+ Communities Should Know About Online Safety
The internet is now crucial for connecting LGBTQ+ people and communities across the globe, but how can you hone your cybersecurity and protect your privacy?

Online Safety and Privacy
Google Users: Fire Up Google Passkeys
In May 2023, Google announced it was launching a new login system called "passkeys."

Online Safety and Privacy
Will Passwords Become a Thing of the Past?
What to know about passwordless authentication and passkeys.

Online Safety and Privacy
Parenting in the Digital Age: 7 Online Dating Rules for Your Teens
Parenting in our always-connected world comes with new challenges, new learning curves, and new awkward moments.

Online Safety and Privacy
Think Intelligent About Artificial Intelligence
Artificial intelligence, including so-called “large language models” like ChatGPT, has rapidly become a major talking point in the press, amongst governments, and maybe even in your office!

Online Safety and Privacy
Hacked Accounts: What to Do Right Now
If an online account has been hacked, it's important to act fast.

Careers and Education
My Cyber Journey – Jennifer Mahoney
Meet Jennifer Mahoney Senior Consultant II, Data Governance, Privacy & Protection at Optiv.

Online Safety and Privacy
Wedding Planning Cybersecurity: Say "I Do!" to Digital Bliss
Congrats on your nuptials! We have a few tips for keeping your Big Day secure.

External Resources
National Cybersecurity Center: Cyber Force Initiative (Colorado)
The purpose of the Cyber Force Initiative is to quickly help students transition to a career in cybersecurity. Once the program application is completed, students will have access to all courses offered at the NCC: IT Fundamentals, Security Pro, Network Pro, and CyberDefense Pro.

Careers and Education
My Cyber Journey – Tonya Drummonds
Meet Tonya Drummonds, Director of Security & Resiliency at Dell Technologies

Online Safety and Privacy
Why Identity Management Matters to You
Do you worry about the security of your personal data in our digital age?

Online Safety and Privacy
Stay Secure While You Work From Home
Remote work seems like it is here to stay for many of us even as the COVID-19 pandemic recedes in our collective rearview mirror.

Careers and Education
Cybersecurity Internships and Entry Level Jobs
Find a cybersecurity internship or entry level job with our partners!

Online Safety and Privacy
What We're Leaning About Data Privacy in 2023
We are living in an incredible time in history – a time when advancements in technology are creating tools that will help solve society’s greatest challenges and fuel the next wave of innovation.

Online Safety and Privacy
How to Tell If Your Computer Has a Virus and What to Do About It
Computer viruses make your devices sick, but you can usually help them heal if you act fast.

Online Safety and Privacy
Avoid Search Engine Ad Malware!
It's a new year and already there is a type of scam becoming extremely popular with hackers.

External Resources
CybersecurityDegrees.org: Cyber Degree Finder
To help you find your dream job, we have resources on schools offering cyber degrees, plus information on career paths, professional certificates, free online courses in security topics, and more.

Online Safety and Privacy
Online Romance and Dating Scams
Love is in the air and online, but so are cybercriminals

Online Safety and Privacy
Public Computers and Wi-Fi
Surf safe when using public computers and networks.

Online Safety and Privacy
What to Do if Your Password Manager Is Breached
What should you do if your password manager is breached?

Careers and Education
My Cyber Journey – Shawnte Arrington, Support, Technical Account Manager, Tanium
Meet Shawnte Arrington, Support, Technical Account Manager at Tanium

Online Safety and Privacy
What Is Data Privacy?
When you think of privacy, what comes to mind? Closing your window shades? Keeping your phone screen locked? Shutting the door when you have a sensitive conversation?

Online Safety and Privacy
10 Online Safety Tips for Gaming
Play safe while gaming.

Online Safety and Privacy
Dongles, Sticks, Drives, and Keys: What to Know About Removable Media
If you find a USB drive or other removable piece of media in the wild, DO NOT plug it into your computer! Let's break down why.

Online Safety and Privacy
How to Be an Online Privacy Snob
Take control of the data you share by being picky.

Online Safety and Privacy
Securing Your Home Network
A protected home network shuts out cybercriminals, allowing your family to use the internet more safely.

Cybersecurity for Business
Small Business Quick Wins
Follow these "quick wins" to secure every aspect of your small business.

Online Safety and Privacy
Online Shopping
Online shopping may be convenient but it can present many opportunities for scammers and cybercriminals.

External Resources
Best-Trade-Schools.net: Trade Schools Guide
As technology advances rapidly, becoming a Cyber Security Specialist is a smart and timely career choice. This booming field is projected to be worth over $10.5 trillion by 2023, playing a crucial role in safeguarding national security.

Online Safety and Privacy
Take Control of Your Data
All your online activity generates a trail of data.

Cybersecurity for Business
4 Simple Steps to Better Protect Your Company from Cyberattacks
Cyberattacks can happen to companies of all sizes.

Cybersecurity for Business
Advancing Collective Risk Management Efforts in the Financial Sector
The protection of our clients and customers from cyber threats is a foundational part of our business.

Cybersecurity for Business
The Security Culture Connection
Have you noticed the phrase “security culture” being used a lot recently? It’s become a bit of a security phrase de jour. That’s both a good thing and a bad thing.

Online Safety and Privacy
Only half of teens agree they "feel supported online" by parents
Not enough children and teenagers trust their parents to support them online, and not enough parents know exactly how to give the support their children need.

Cybersecurity for Business
6 Ways to Help Employees be Privacy Aware
Promote awareness about privacy, safeguard data and enable trust throughout the workplace with these tips.

Cybersecurity for Business
Cybersecurity awareness starts with people: Microsoft helps you and your team to #BeCyberSmart
Vasu Jakkal, CVP at Microsoft, emphasizes the importance of cybersecurity education for individuals and organizations.

Online Safety and Privacy
What About Password Manager Risks?
In the new Password Policy ebook, What Your Password Policy Should Be, KnowBe4 recommends that all users use a password manager to create and use perfectly random passwords.

Cybersecurity for Business
Cybersecurity collaboration as a national imperative
Bobbie Stempfley emphasizes the urgent need for a collaborative cybersecurity ecosystem to effectively combat the increasing frequency and severity of cyberattacks

Cybersecurity for Business
Building a Security Culture: The Foundation of a Secure Organization
Creating strong cybersecurity defenses for any organization requires a lot of important elements. Everyone knows a strong firewall is an essential first line of defense.

Careers and Education
My Cyber Journey – Jeremy Daniels, Cyber Analyst at HPE
Meet cyber analyst and HBCU grad, Jeremy Daniels.

Online Safety and Privacy
‘It’s easy to stay safe online’ with these 4 steps (plus 1)
When it comes to cybersecurity, good behavior can be rewarding.

Cybersecurity for Business
Making Cybersecurity Relevant for Consumers: The Case for Personal Agency
As Cybersecurity Awareness Month kicks off, one of the questions we often hear is “does consumer education really make a difference?”

Careers and Education
My Cyber Journey – Monique Head
Meet Monique Head, Founder of CyberTorial.org and Sr. Partner, Information Security, Communications, Awareness & Education at Netflix.

Online Safety and Privacy
Raising Digital Citizens
We all know the internet is a fantastic world of learning and entertainment for kids, but, like the real world, there can be dangers, too.

Careers and Education
Reinforcing Cybersecurity: Start with a Diverse Workforce
Looking to reinforce your company’s cybersecurity strategy? A good place to start is to cultivate a diverse workforce.

Online Safety and Privacy
Best Practices for Security and Privacy Settings
Want to lead a Stay Safe Online lifestyle, but don't know where to start?

Toolkits
Teach Others How to Stay Safe Online: Volunteer Toolkit
We're calling on all security professionals to share their expertise and volunteer to teach your community about online safety.

External Resources
Coursera: Developing a Program for Your Business Specialization
Master the Fundamentals of Cybersecurity. Learn to assess cyber threats and protect business information assets.

External Resources
Coursera: Introduction to Cyber Security Specialization
Cyber Security. An introduction to modern information and system protection technology and methods.

External Resources
LinkedIn Learning: Cybersecurity Foundations
Set a rock-solid foundation for your network, users, and data by learning about the basics of cybersecurity.

External Resources
Great Learning: Advanced Cyber Security - Threats and Governance
Learn solutions for cyber-attacks with Advanced Cyber Security-Threats and Governance free course

External Resources
Skill Share: Go From Zero to Hero
The field of technology is growing exponentially with the IT sector flourishing every day. Amidst such growth of the industry and increased concern for privacy, the demand for security is rising. Cybersecurity has become an everyday struggle for many businesses. Recent trends and statistics reveal that there is a huge increase in hacked and breached data from very common sources at workplaces. So go for this course to get a better understanding of cyber security!

Online Safety and Privacy
Password Managers
Don't pass on password managers. Learn more about these useful tools.

Careers and Education
How Free Pizza Led to a Cyber Career
A Chat with Bill.com’s Rinki Sethi

Online Safety and Privacy
You Can Stop Cyberbullying As A Kid!
As a kid using the internet, you've probably heard of cyberbullying. Maybe you or a friend has experienced it.

Online Safety and Privacy
The Modern Teen’s Guide to Handing Out L’s to Cyberbullies
Cyberbullying can make you feel like you can't really be "you" online. Here's what to do.

Online Safety and Privacy
Parents and Educators: What to Do About Cyberbullying
Have you ever texted or posted something online that you would never say to someone in person? You’ve probably experienced how the internet's anonymous nature can sometimes bring out the worst in people.

Online Safety and Privacy
10 Must-Know Tips For Keeping Your Personal Data Safe
The internet has become a vital aspect of our lives.

Cybersecurity for Business
Identity Management and the Second Half of the Chessboard
Ray Kurzweil's concept of the "second half of the chessboard" illustrates how exponential growth in technology and data management can lead to significant economic impacts and inefficiencies if not effectively managed.

Online Safety and Privacy
Secure Your Home
Internet-connected devices are helping homeowners increase efficiency, reduce costs, conserve energy and a whole host of other benefits.

Cybersecurity for Business
9 Security Questions Business Owners Must Ask Vendors
No matter the nature or size of your company, you need to think about cybersecurity in our connected present. This doesn't just mean your own operation's cybersecurity, but the security of every vendor you do business with.

Careers and Education
From Librarian to Cyber Pro
A Chat with the @InfoSecSherpa Tracy Z. Maleeff

Cybersecurity for Business
Cybersecurity: 3 Things Every Small Business Owner Should Know
Cyber attacks can be devastating, and they are increasingly common for small to mid-sized businesses.

Online Safety and Privacy
Respect Privacy
Respecting the privacy of your customers, staff, and all other stakeholders is critical for inspiring trust and enhancing reputation.

Cybersecurity for Business
Covid-19 Cybersecurity Resources for Small Businesses
To respond to the global pandemic and deliver timely information and resources to the nation’s small business community, the National Cybersecurity Alliance’s CyberSecure My Business program created the COVID-19 Small Business Cybersecurity Series.

External Resources
Additional Resources for Businesses
Frameworks, assessments, and guides from across the web.

Cybersecurity for Business
Identify Your “Crown Jewels”
Take an inventory of your business's most valuable assets.

Cybersecurity for Business
Protect Data and Devices
Secure the "crown jewels" of your business.

Cybersecurity for Business
Recover From Cyber Incidents
How to help your business recover from a cyber incident.

Cybersecurity for Business
Respond to Cyber Incidents
Do you have a plan in place to respond to cyber incidents at your business?

Cybersecurity for Business
Cybersecurity, It's More Than IT
As our lives become more digital, the risk of cybercrime grows, making strong cybersecurity measures essential not only for data protection but also for safeguarding customer information.

Careers and Education
Forestry Expert to Cybersecurity Manager: A Chat with Discover’s Sunil Mallik
Despite common perceptions, cybersecurity professionals come from all different walks of life.

Online Safety and Privacy
Talking to Kids & Teens about Security and Privacy
In today’s world, digitally connected families must think about safety and security both online and offline.

Online Safety and Privacy
Online Safety Tips For Older Adults
Just as you fasten your seat belt before driving, take precautions before using the Internet to be sure you are safe and secure.

Online Safety and Privacy
Parental Controls
As a parent, how do you stay involved in your child’s digital life?

Online Safety and Privacy
Talking to Kids and Teens about Security and Privacy
In today’s world, digitally connected families must think about safety and security both online and offline.
External Resources
American Indian Science & Engineering Society: AISES Membership
Opportunities and Resources for Native Students in STEM

External Resources
ApprenticePath: Discover Your Career Path
Jumpstart your career via paid apprenticeships

External Resources
Bold.org: Computer Science Scholarships
The Best Scholarships for Prospective Computer Science Professionals with Upcoming Deadlines

External Resources
The Center for Infrastructure Assurance and Security (CIAS): National Collegiate Cyber Defense Competition
Established in 2001 as part of UTSA’s creation of a cybersecurity program, the CIAS is a research center on a mission to secure the nation’s infrastructure and foster a Culture of Cybersecurity.

External Resources
Culture of CybersecuriTy: Kids Activities
The CIAS K-12 Cybersecurity Program is designed to introduce students to cybersecurity education and possible career paths in STEM disciplines, especially cybersecurity. To increase interest and learning capabilities, this initiative is centered around the CyBear™ family.

External Resources
Code.Org: Computer Science at Home
Anyone can learn Computer Science. Start coding today.

External Resources
Cyber.Org: Browse Free Cyber Curricula
CYBER.ORG empowers educators to teach cyber confidently, resulting in students with the skills and passion needed to succeed in the cyber workforce.

External Resources
Cyber.org: Cyber@Home
There is something here for everyone with fun, project-based activities for elementary, middle, and high school students.

External Resources
Fastport and Purdue University: Purdue Cyber Apprenticeship Program
These programs all provide earn and learn opportunities for participants with compensated experiential, effort-based employment and an industry-recognized educational component.

External Resources
CyberScient: Kids Platform
Share your successes and struggles with a community of like-minded students who share your artistic goals on our public forums.

External Resources
CyberDegrees.org: Cybersecurity Degrees
There are hundreds of different cybersecurity degrees.

External Resources
Cybersecurity Guide: K12 Cybersecurity Guide
If you are a young person interested in pursuing a career in technology, it can be challenging to know where to start. While some schools may offer curriculum in technology, cybersecurity isn’t typically covered.

External Resources
Girls Who Code: College Programs
Girls Who Code offers a wide range of programs designed to support college-aged students and early career professionals (18-25) in persisting in their computer science education and succeeding in their first internships and jobs.

External Resources
IKeepSafe: Faux Paw Cybersecurity Superheros activities
Meet Faux Paw, an adventurous six-toed cat who loves technology. These fun books teach rules to promote the safe and healthy use of digital devices. Read or watch Faux Paw’s adventures using links below each book’s description.

External Resources
IKeepSafe: Data Privacy Educator Training Course
Growing concerns about student data privacy can create hurdles for K12 educators working to expand access to edtech and digital innovations. EduPaths and iKeepSafe partnered to create four courses centered around data privacy in education.

External Resources
Microsoft: Microsoft Learn for Educators
Equip your students with AI and tech skills for today—and tomorrow

External Resources
Natives in Tech
Cultivate a tech ecosystem of Native technologists crafting free and open source technology for Native communities.

External Resources
National Initiative for Cybersecurity Careers and Studies: Cybersecurity in the classroom
Are you a Kindergarten through 12th grade (K-12) teacher or educator looking to incorporate cybersecurity into your lesson plans? Do you want to help your students learn about cyber concepts and career opportunities?

External Resources
National Initiative for Cybersecurity Careers and Studies: Veterans User Guide
Veterans and military personnel looking to transition out of the armed forces, are you ready for your next mission?

External Resources
Carnegie Mellon University: picoCTF.org
Watch our monthly YouTube lecture series on intro cybersecurity principles.

External Resources
Breaking Into Cybersecurity: Podcast by By Renee Small/Christophe Foulon
It’s a conversation about what you did before, why did you pivot into cyber, what the process you went through Breaking Into Cybersecurity, how you keep up, and advice/tips/tricks along the way.

External Resources
GenCyber: GenCyber Camps
GenCyber provides cybersecurity experiences for students and teachers at the secondary level.

External Resources
Roadtrip Nation: Information Security Engineers Career
Information Security Engineers Career Pathway

External Resources
Cyber Center of Excellence (CCOE): Cyber Center of Excellence (CCOE) Cyber Career Map
Chart your personal path to a cyber career with the exploration dashboard and zoom in for jobs, education, resources and much more.

External Resources
Salesforce: Cybersecurity Learning Hub
Learn in-demand skills and build your cybersecurity career path

External Resources
Temple University: Organizations We Love
These are the amazing 309 organizations that strive to make tech and info/cybersecurity opportunities and experiences accessible to everyone [1,2,3], and so they are the Organizations We Love (OWL)

External Resources
Temple University CARE Lab: Collegiate SECTF competition
The CARE Lab hosts social engineering competitions every summer! This event is open to high school, undergraduate, and graduate students. We partner with industry, government, and nonprofits to provide students with the best possible experiences and exposure to real world events.

External Resources
SMARTFENSE – Videojuegos educativos: Las aventuras de Gupi
Las Aventuras de Gupi es un videojuego lanzado por SMARTFENSE en el cual un pez llamado Gupi necesita la ayuda del usuario para no morder el anzuelo.

External Resources
Palo Alto Networks: Cyber A.C.E.S. Program
Cyber A.C.E.S. provides the cybersecurity basics students need to have safer online experiences and become good digital citizens. Lessons are designed so they can be facilitated by anyone, regardless of their knowledge level, with each module tailored to a specific age group.

External Resources
Code.org: Code Break
A weekly challenge to engage students of all abilities, even those without computers.

External Resources
TryHackMe: Cyber security Training
Learn cyber security with fun gamified labs and challenges

External Resources
Women’s Society of Cyberjutsu (WSC): Career Resources
The Women’s Society of Cyberjutsu (WSC), a 501(c)3 non-profit, is dedicated to raising awareness of cybersecurity career opportunities and advancement for women in the field, closing the gender gap and the overall workforce gap in information security roles.

External Resources
Symantec and AAUW: STEMpack: Cyber Security
Cyber Security curriculum to inspire and introduce participants to cyber security and computer science.

External Resources
CISA: Cybersecurity Workforce Training Guide
Released August 2021, the Cybersecurity Workforce Training Guide is for current and future federal, state, local, tribal, and territorial (SLTT) staff looking to expand their cybersecurity skills and career options.

External Resources
Center for Internet Security: Why Consider a Career in Cybersecurity?
As technology evolves and cybersecurity threats continue to grow, the need for qualified cybersecurity candidates only intensifies. But it's not always easy to fill these positions. That's why starting a career in cybersecurity is worth considering, especially for students or individuals who are looking for a career change.

External Resources
CompTIA: State of the Tech Workforce
CompTIA’s State of the Tech Workforce, also known as Cyberstates, provides the definitive guide to tech workforce trends, the number of available jobs in technology, and tech industry employment statistics by state, metro area and nationwide.

External Resources
C.A.K.E: Cyber Academy For Kids through Empowerment
CAKE - Cyber Academy for Kids through Empowerment - Founded by two industry professionals in the field of cybersecurity and information technology is teaching elementary, middle and high school students the fundamentals of cybersecurity.

External Resources
Cybersecurityjobs.com Training Fund
Our mission is to connect cybersecurity professionals with organizations in need of cybersecurity talent but putting people and employers together is just one side of the equation.

External Resources
Cyber Seek
CyberSeek provides detailed, actionable data about supply and demand in the cybersecurity job market.

External Resources
Cyber Virginia: VIRGINIA VETERANS CYBER TRAINING PILOT
In an effort to address the growing demand of over 17,000 cyber jobs available across the state of Virginia, organizations have joined together with the Commonwealth of Virginia to sponsor free cyber training and industry-recognized certifications as part of a pilot program for veterans who want to live and work in the Commonwealth in the cyber field.

External Resources
Cybrary: Cybersecurity Training and Career Development
Cybrary’s structured, hands-on cybersecurity courses and training empowers professionals to better protect their organizations.

External Resources
Cyversity
To achieve the consistent representation of women, underrepresented communities, and all veterans in the cybersecurity industry through programs designed to diversify, educate, and empower.

External Resources
Empow(H)er Cybersecurity
The goal of Empow(H)er Cybersecurity is to provide a platform for all women of color to grow their networks, be inspired, and feel empowered.

External Resources
ESET: Women in Cybersecurity Scholarship
Two $10,000 scholarships will be awarded to graduate/undergraduate women pursuing a career in cybersecurity.

External Resources
Fortinet: Veterans Program
Transitioning the military community into the cybersecurity industry through world class training.

External Resources
Future Learn: Cybersecurity Courses
Explore online criminal activity and undergo cyber security training to protect yourself and others online, or prepare for a career in cyber security.

External Resources
Girl Scouts: Ambassador Cybersecurity Safeguards Badge: Guard Your Movements
Identify data vulnerabilities in a typical day

External Resources
Girl Scouts: Brownie Cybersecurity Basics Badge Activity: Tech Scavenger Hunt
Do a scavenger hunt to explore how technology replaces everyday objects.

External Resources
Girl Scouts: Cadette Cybersecurity Safeguards Badge Activity: Inventory Your Digital Presence
Explore some of the types of data collected by websites and apps.

External Resources
Girl Scouts: Daisy Cybersecurity Basics Badge Activity: Protect Your Treasure
Explore how to keep something safe, like a computer, with layers of protection.

External Resources
Girl Scouts: Junior Cybersecurity Basics Badge Activity: Roll with Protocols
Explore how computers send and receive information when sending messages.

External Resources
Girl Scouts: Senior Cybersecurity Basics Badge Activity: Identify Functions and Privileges
Explore how cybersecurity professionals keep computer networks safe.

External Resources
Hacker Highschool
Hacker Highschool (HHS) started in 2003 as a means of teaching teens problem solving, resourcefulness, and empathy through hacking.

External Resources
Center for Cyber Safety and Education: Scholarships
The scholarships are part of an effort to bridge the cybersecurity workforce gap by providing future cybersecurity professionals across the globe with scholarships to prepare them for a rewarding career in this important field.

External Resources
(ISC)2: Webcast series
ISC2 produces complimentary webinars with high-quality content on an ongoing basis. Advance your knowledge on emerging issues and stay up-to-date on global trends and hot-button topics.

External Resources
NICE K12 Cybersecurity Education Conference
The NICE K12 Cybersecurity Education Conference is the premier event for K-12th grade cybersecurity educators.

External Resources
Microsoft: MakeCode
Microsoft MakeCode is a free online learn-to-code platform where anyone can build games, code devices, and mod Minecraft!

External Resources
National Cyber Scholarship Foundation
The initiative is designed to identify talent in high school and college students, and includes a comprehensive set of programs and supports that work together to create a more assured pipeline for building the next generation of cyber talent.

External Resources
NextGen CyberTalent: NextGen Candidate Programs
NextGen Cyber Talent conducts a cohort every month to educate and train underserved, underprivileged and diverse talents in Cybersecurity, risk, and compliance domains.

External Resources
National Initiative for Cybersecurity Education: Cybersecurity Career Awareness Week
Cybersecurity Career Week is a campaign to promote the discovery of cybersecurity careers and share resources that increase understanding of multiple learning pathways and credentials that lead to careers.

External Resources
National Initiative for Cybersecurity Education: Free and Low Cost Online Cybersecurity Learning Content
The following links are for free and low-cost online educational content on topics such as information technology and cybersecurity

External Resources
NICE: The Challenge of That First Job in Cybersecurity – Entry Level Roles and How to Qualify
This webinar will explore the unique challenges and opportunities from the perspective of educators, employers, and job-seekers.

External Resources
Palo Alto Networks: Cybersecurity Academy
World-class curriculum and programs specifically designed for K-12, colleges and universities.

External Resources
Palo Alto Networks: Certified Cybersecurity Entry-Level Technician (PCCET) program
The PCCET certification covers fundamental cybersecurity, network security, cloud security, and SOC security principles.

External Resources
PBS: The Cybersecurity Lab
Whenever we go online—to shop, chat with our friends, or do anything else—we put ourselves at risk of cybercrime. Computer viruses can corrupt our files, hackers can steal our data, and criminals can trick us into revealing sensitive information. But luckily there are simple steps we can take to protect our digital lives.

External Resources
RangeForce: Cybersecurity Training
Take your cyber skills to the next level. Access a limited number of hands-on cybersecurity training modules for free, forever.

External Resources
SANS: Diversity Cyber Academy
Facing the cybersecurity challenge, SANS Diversity Cyber Academy offers cybersecurity training scholarships for minorities and women.

External Resources
SANS Institute: Free Cyber Security Training
Learn the Fundamentals of Cyber Security for Free!

External Resources
Scholastic: #CyberSmarts
As your kids discover the power of the internet, make discussing the do’s and don’t’s of online behavior a priority.

External Resources
Tynker: Coding for Kids
Tynker is the fun way to learn programming and develop problem-solving & critical thinking skills.

External Resources
US Cyber Challenge
USCC’s goal is to find 10,000 of America’s best and brightest to fill the ranks of cybersecurity professionals where their skills can be of the greatest value to the nation.

External Resources
Katzcy: US Cyber Games
The mission of the US Cyber Games® is to bring talented cybersecurity athletes, coaches, and industry leaders together to build an elite US Cyber Team for global cybersecurity competition.

External Resources
Air Force Association: Elementary School Cyber Education Initiative
The CyberPatriot Elementary School Cyber Education Initiative (ESCEI) is a set of three fun, interactive learning modules aimed at increasing grade K-6 students’ awareness of online safety and cybersecurity principles. Supplemental activities are also available to get students collaborating with each other about their newly learned cyber skills!

External Resources
Varonis: Which Cybersecurity Career Is Right For Me?
Finding the right career path in the cybersecurity industry isn’t always easy. We interviewed cybersecurity experts to find out what inspired them!

External Resources
University of Washington: Access Computing Team
AccessComputing helps students with disabilities pursue degrees and careers in computing fields through inclusive academic and mentoring programs.

External Resources
Black Girls Code
Since 2011, Black Girls Code has supported girls of color in tech through coding education and more. We partner with schools and organizations to offer a range of programs, both in-person and virtual, for ages 7-25.

External Resources
Women in Security and Privacy
We are advancing women and underrepresented communities to lead the future of security and privacy.

External Resources
Kalinda Raina: Raising the Digital Future
Let's talk real world solutions for raising children in a world where every bad decision they make will exist on the Internet for any curious college admission counselor or job recruiter to find.

External Resources
CompTIA: Cybersecurity: Skills, Tips, and Advice From Our Panel of Experts
CompTIA has brought together a panel of cybersecurity experts to share their knowledge and experience with seasoned IT pros and those interested in starting a career in cybersecurity.

Online Safety and Privacy
COVID-19 Security Resource Library
Free resources to help individuals and organizations through the COVID-19 pandemic.

Toolkits
Cyberbullying
Cyberbullying can range from embarrassing or cruel online posts or digital pictures, to online threats, harassment, and negative comments, to stalking through emails, websites, social media platforms and text messages.

Online Safety and Privacy
Malware, Viruses and Botnets
These 3 types of cybercriminal tools are common online, and you as an internet user might come across them from time to time.

Online Safety and Privacy
Security Awareness Episodes
Watch and download this fun series on security best practices!

Cybersecurity for Business
Did You Notice a Shift in Attitudes Towards Awareness Training at This Year's NCA Conference?
Mike Polatsek, Co-founder and CSO at CybeReady, reflects on Convene: Florida.

Cybersecurity for Business
Top 10 Security Issues in Enterprise Cloud Computing
As a CISO, you know the list of security issues in enterprise cloud computing seems to always be growing.

Careers and Education
Tech Lover...but Cyber Late Bloomer
A Conversation with Prajakta "PJ" Jagdale of Palo Alto Networks

Online Safety and Privacy
Is working on your smartphone a risky business or are you cybersecure?
The increasing use of mobile devices in our personal lives has led to a growing acceptance of smartphone usage at work.

Online Safety and Privacy
Stalkerware
BEFORE YOU CONTINUE: Stalkerware apps can track your browsing history so if you suspect that stalkerware has been installed on your device DO NOT USE IT to research support services such as advocacy, shelter, court information or emergency services.

Online Safety and Privacy
Tips for Higher Education Online Teaching and Learning
As online and hybrid learning environments become more popular, it is essential for students, faculty, and staff to adopt key cybersecurity practices.
Online Safety and Privacy
K-12 Online Learning
Online learning is here to stay. Many K-12 schools will probably use some blend of fully online learning and in-person teaching for the foreseeable future.

Online Safety and Privacy
Mobile Devices
That smartphone in your pocket, that tablet on your coffee table or that laptop on your desk contains a treasure chest of information about you, your friends and your family.

Online Safety and Privacy
A Teacher’s Guide To Student Online Safety
Students are more connected than ever before thanks to the internet.

Careers and Education
Lawyer, Children's Book Author, and Career Changer to Cybersecurity
Meet Zinet Kemal

Cybersecurity for Business
Human Challenges in Implementing Multifactor Authentication (MFA)
How to implement an effective MFA program in your business.

Cybersecurity for Business
How Smart Card Technology Uses Network Security
The concept of network security has been in existence for decades. With organizations using more sensitive information, the need to create policies that would limit access and control of a network has increased.

Online Safety and Privacy
7 Tips for a Safer Internet of Things
The "Internet of Things" (IoT) has been a realm of technological innovation that has grown exponentially over the past decade.

Cybersecurity for Business
As an Employee or a Business Owner, You Need to Be Cyber Aware and Resilient
As our world becomes increasingly connected, it’s more important than ever to be cyber aware. There’s no question, cyber attacks are evolving in sophistication and attackers are broadening the entities they’re willing to target.

Cybersecurity for Business
The Top Cybersecurity Trends for 2022
Here are the top three cybersecurity trends we think are worth watching as we approach 2022

Online Safety and Privacy
Be Cyber Smart: A guide to help you do your part
Let’s brush up on cyber hygiene — basic steps we can take to stay safe in a connected world.

Cybersecurity for Business
5 Cybersecurity Trends in 2021
As remote work becomes the norm post-COVID-19, the cybersecurity landscape is evolving rapidly, presenting new threats and necessitating a reassessment of strategies to protect organizations from increasingly sophisticated attacks.

Careers and Education
From math-hater to DEFCON-lover: An unlikely path to Cybersecurity
Would you let a fear of math scare you away from a career in cybersecurity?

Online Safety and Privacy
Reporting Matters – even for a Smishing Message
With the increased use of mobile devices to manage so much of our lives, it’s no surprise scammers have moved to this medium to target your sensitive information.

Online Safety and Privacy
7 Tips to Manage Your Identity and Protect Your Privacy Online
Worried about how much of your private information is on the internet and vulnerable to theft or misuse? You’re not alone.

Online Safety and Privacy
Spotting a Vaccine Phishing Scam: Can You Find the Red Flags?
Many of us have seen COVID-related scams hit our inboxes. It’s no secret that scammers try to take advantage of times of panic and uncertainty, when people are most vulnerable, to steal personal information.

Online Safety and Privacy
Take It Personally: Ten Tips for Protecting Your Personally Identifiable Information (PII)
When we're online, we accumulate a significant amount of personally identifiable information (PII), which can be exploited by cybercriminals.

Cybersecurity for Business
The Impact of Data Breaches and Cyberattacks on SMBs and Their Employees
It is always important for businesses to ensure their employees work securely, both at the office and home, as threat actors continually look for ways to attack.

Cybersecurity for Business
How to Run a Virtual Cybersecurity Awareness Month Campaign
Engage your employees online during Cybersecurity Awareness Month.

Online Safety and Privacy
Security Awareness: Episode 4 – Phishing and Ransomware
We’re bringing you another free security awareness video! These videos are brought to you by Adobe, National Cyber Security Alliance, and Speechless Inc.

Online Safety and Privacy
Owning Your Privacy by Managing Your Digital Footprint
The information you share online can reveal more details then you intend and make you vulnerable to compromise.

Online Safety and Privacy
How to Secure and Maintain Your Digital Identity
Individuals must take proactive steps to safeguard their digital identities by being cautious about personal information sharing, connection requests, and message links.

Online Safety and Privacy
Sextortion: What to Look Out For and What to Do If You’re a Victim
An explanation of sextortion and how it works.

Cybersecurity for Business
How Your IT System Could Be at Risk from a Physical Attack
Don't overlook the physical risks to your IT system.

Online Safety and Privacy
The Secret Language of Emoji
Emoji appeared in 1999 with a set of 176 symbols that were meant to convey weather, traffic, technology and time. Today, there are 2,823 emoji that convey information across language, culture, lifestyle and diversity.

Cybersecurity for Business
You’ve Been Hacked: 5 Ways to Minimize the Damage
Getting hacked is a nightmare scenario for every business. Fifty percent of small businesses in the U.S. have experienced a cyberattack. And this fact is not surprising – most small businesses lack the advanced security resources and technology that large enterprises can afford.

Online Safety and Privacy
Stay Secure On Public Wi-Fi When Traveling
Twink twice before connecting to a public wi-fi network when you're on the go.

Online Safety and Privacy
Protecting Baby Monitors From Hacking
The use of Wi-Fi-capable baby monitors has become indispensable to many parents.

Cybersecurity for Business
How to Protect Your Customer Relationship Management (CRM) Data from Hackers
CRM systems are some of the most useful assets for an organization, enabling businesses to build meaningful customer relationships, find new prospective customers and drive revenues.

Online Safety and Privacy
Security and Privacy Tips for Cryptocurrency Holders
The cryptocurrency trend is definitely a big boom in today’s financial market.

Online Safety and Privacy
Data Privacy Is Crucial for the LGBT Community
It is vitally important to consider how compromised online privacy can specifically affect marginalized groups such as the LGBT community.

Online Safety and Privacy
Health Technology in the Digital Era – Benefits + Risks
Examining the evolution of health technologies and their implications for patient privacy and security.

Online Safety and Privacy
Health Information Privacy – Why Should We Care?
Recent data breaches involving health information pose significant risks to our online privacy. Learn how to protect your valuable health data.

Online Safety and Privacy
15 Online Security + Privacy Tips for College Students
You’re responsible for your own online security at college, so follow these tips to help you be safe and privacy-savvy on campus.

Cybersecurity for Business
Key Ways to Protect Your Business From Malware
Cyberattacks are a serious threat to businesses and consumers, with large-scale attacks having nationwide effects, thus making national security a serious concern.

Cybersecurity for Business
What Happens When Cyberbullies Join the Workforce?
Cyberbullying has been stereotyped in the media as a problem that occurs with teenagers, cell phones, sexualized photographs and social media.

Online Safety and Privacy
What Is Smishing? How Text Message Scams Work (And How To Avoid Them)
Cybercriminals love to go smishing, but you don’t have to take the bait.

Online Safety and Privacy
What Are Common Crypto Scams?
Cryptocurrency investment scams are big business, but you can keep your wallet safe.

Online Safety and Privacy
Are Passwords Going Away? What You Need to Know About Passkeys
The future of logging in is already on your phone!

Online Safety and Privacy
10 Reasons Why You Need to Be At Convene: Cleveland
If you work at the intersection of people and security, then you got to join us this summer in Cleveland for our Convene conference.

Online Safety and Privacy
Is Microsoft Doing Away With Passwords?
If you use Microsoft Authenticator to store passwords, they will be deleted in August.

Cybersecurity for Business
How You Can Help Secure Smaller Vendors with Limited Budgets and Know-How
If you work in third-party risk management (TPRM), you face a growing challenge: how to keep your supply chain secure when many vendors are small businesses with limited cybersecurity resources?

Cybersecurity for Business
Your Business Has Been Hacked: How to Minimize the Damage
If your small business has been hacked, you need to act fast. Here are some key things to know to fight back, stay open, and build resilience in the event of a cyberattack.

Cybersecurity for Business
Why Physical Security Is Still Necessary for Cybersecurity
Physical security is an essential, but often overlooked, factor in cybersecurity.

Toolkits
Best Vacation and Travel Cybersecurity Tips
Whether you're lounging on a beach or hiking through the mountains, these days, you probably stay connected during your trip.

Cybersecurity for Business
How to Protect Your Small Business from Malware
Malware attacks, including ransomware, are one of the most common threats facing small businesses today.

Cybersecurity for Business
Best Practices for Protecting Your CRM Data
Your customers are the lifeblood of your business and their data is extremely valuable.

Online Safety and Privacy
Tread Lightly Online: How to Check and Manage Your Digital Footprint
While you can’t use the internet completely undetected, you can manage your digital footprint and protect your data privacy. Find out more using our guide.

Online Safety and Privacy
6 Cybersecurity Myths Debunked
There are a lot of myths flying around about cybersecurity. We’ll go over the most common cybersecurity myths and debunk them so we can stay safer online.

Online Safety and Privacy
Cyberbullying in the Workplace: How to Recognize, Address, and Prevent It
Cyberbullying is often associated with teenagers and social media, but some bullies grow up...and enter the workforce.

Online Safety and Privacy
Does AI Take Your Data? AI and Data Privacy
Generative AI, including platforms like ChatGPT, DALL-E, Google Gemini, Apple Intelligence, has revolutionized our relationship with technology.

Online Safety and Privacy
Why Your Family and Coworkers Need a Safe Word in the Age of AI
Scammers always rely on deception to trick people out of their money, but the sudden wide availability of artificial intelligence has increased the convincingness of their schemes.

Toolkits
AI Fools: Stay Sharp!
An awareness campaign on AI-enabled scams & responsible AI use.

Online Safety and Privacy
How to Update Your Software
An easy way to boost your cybersecurity is to always keep software and apps updated.

Online Safety and Privacy
What Is Phishing and How To Avoid It
Cybercriminals love to go phishing, but you don't have to get hooked.

Careers and Education
How To Write a Cyber Resume and LinkedIn That Gets Results
If you're hunting for a job in cybersecurity, you're aware that your resume and LinkedIn profile are critical to getting hired in this competitive field. But how do you create a resume that gets noticed?

Online Safety and Privacy
How to Stop the Flow of Personal Data with Cloaked CEO Arjun Bhatnagar
It’s Data Privacy Week, when we pay special attention to why data privacy is so critical in today’s world.

Online Safety and Privacy
Cybersecurity for Tax Season: Protect Your Identity and Refund
Tax season brings enough stress without adding scammers to the mix. But the reality is that criminals ramp up attacks in the first few months of the year, often impersonating the IRS or trusted services like H&R Block and TurboTax.

Careers and Education
Cyber Groups with Local Chapters You Can Join Today!
Cybersecurity is a community, even if it might not always feel like it with your nose buried in your laptop.

Online Safety and Privacy
What is Multifactor Authentication (MFA) and Why Should You Use It?
You can protect your online accounts with more than just a password.

Online Safety and Privacy
Stay Secure While Job Hunting
When looking for new opportunities, follow these simple steps to protect yourself from fraud.

Online Safety and Privacy
Use Apps and Software to Protect Your Data
Our data is constantly collected and shared, and we often don't even know all the types of data being gathered.

Online Safety and Privacy
Create and Use Strong Passwords
Passwords are the keys to safeguarding your digital and online life. They are your first line of defense. And knowing how to create and store strong passwords is one of the most critical aspects of everyday cybersecurity.

Online Safety and Privacy
What is Data Privacy and Why Should You Care?
Data Privacy Week is January 27 - 31, 2025!

Online Safety and Privacy
Cybersecurity Predictions for 2025: Challenges and Opportunities
The year 2024 was a whirlwind year for cybersecurity. From the fallout of high-profile ransomware attacks to the increasing commoditization of AI tools, the challenges kept mounting.

Online Safety and Privacy
Chinese Telecom Hack: How to Protect Your Messages
Learn how to protect your calls and texts following the Chinese telecom cyberattack with simple tips like using encrypted apps.

Online Safety and Privacy
How to Avoid Scams and Fraud
Online scams are becoming increasingly sophisticated, targeting people of all ages. But with some knowledge, you can protect yourself and your loved ones.

Online Safety and Privacy
Avoid Gift Card Draining Scams This Holiday Season
Gift cards make for easy, versatile gifts, especially during the busy holiday season. But they’re also prime targets for scammers who use "gift card draining" to steal funds before the recipient can even use the card. Let’s break down how these scams work and how you can stay safe.

Cybersecurity for Business
How to Make Cybersecurity Training Accessible
Does your training program reach all employees in your organization?

Online Safety and Privacy
What is Pig Butchering and How to Spot the Scam
"Pig butchering" is a scam that's been muscling into the headlines lately.

Toolkits
Oh Behave! The Annual Cybersecurity Attitudes and Behaviors Report 2024
Each year, the National Cybersecurity Alliance releases research to better understand the public’s security behavior and to act as a call to action for better secure habits online.

External Resources
KnowBe4 Children’s Interactive Cybersecurity Activity Kit
Looking for a way to talk about online safety and security with your children? KnowBe4 provides a fun and interactive cybersecurity kit to help you teach them valuable online safety and security skills.

Online Safety and Privacy
Did Hackers Steal Every Social Security Number? Here's What To Do.
Learn how to protect your social security number.

Careers and Education
The Evolution of Ethical Hacking: From Curiosity to Cybersecurity
The term "ethical hacking" was coined in 1995 by IBM Vice President John Patrick, but the practice itself has roots that stretch back much further.

Online Safety and Privacy
Data Breaches Slim Down Your Wallet
Data breaches are becoming an expensive predicament for all of us, even if your data isn't directly stolen in a breach.

Online Safety and Privacy
When Websites Make It Hard to Cancel...
Some websites and apps are designed to be manipulative – they make it hard to cancel a recurring subscription, obscure the fact that you will be charged, or hide the unsubscribe button.

Online Safety and Privacy
Watch Out for EBT Scams
Scammers target some of the most vulnerable.

Online Safety and Privacy
Protect Your Credit Cards from Skimmers and Shimmers
You can be a target of credit card skimming when you least expect it.

Careers and Education
How to Be an Awesome Cyber Mentor
Help close the cyber workforce gap by mentoring the next generation.

Careers and Education
How to Find a Mentor
Begin your career in cyber with the help of a mentor.

Online Safety and Privacy
Backups
Our digital devices contain vast treasure troves of data, from family photos and music collections to financial data, health records and personal contacts.

Online Safety and Privacy
When Scammers Call Grandma
"Your grandson has been arrested and needs bail money." "Your granddaughter was at fault in a car crash, and you need to pay the other driver's medical bills." What do you do if you receive these calls?

Online Safety and Privacy
Don’t Scam Me Right Now, I’m Trying to Buy a Home
How scammers try to trick home buyers and sellers.

Online Safety and Privacy
What To Do If Your Identity Is Stolen
With data breaches seemingly happening every week, more and more people are victims of identity theft.

Online Safety and Privacy
5 Common Real Estate Scams You Need to Know About
Since every real estate transaction involves a significant sum of money, anyone in the home market today will likely run into scammers on the prowl.

Online Safety and Privacy
Online Safety Basics
With a little prep, you can shield your information online and secure your digital systems and devices.

Online Safety and Privacy
Securing Smart Speakers and Digital Assistants
Smart speakers and digital assistants like Amazon Echo, Google Nest, Apple HomePod, and Sonos Era are integral to many modern households.

Online Safety and Privacy
How Data Breach Fatigue Can Impact Your Digital Health
When you hear your sensitive data was lost in another data breach, is exhaustion your first reaction?

External Resources
Stay Safe Online — Related Links
Here are helpful links from the National Cybersecurity Alliance’s sponsors, partners and friends to help you and your friends and family be safer and more secure online.

Online Safety and Privacy
Reporting Cybercrime
The first step toward bringing cybercriminals to justice is reporting cybercrime when it happens.

Cybersecurity for Business
What to Do if Your Business Facebook Is Hacked
There has been an uptick in cybercriminals attempting to target small businesses' Facebook profiles and ad accounts.

Online Safety and Privacy
Manage Your Privacy Settings
Direct links to manage your privacy settings on popular platforms and apps.

Online Safety and Privacy
How to Restore an MFA Authenticator App
Authenticator apps for multi-factor authentication (MFA) significantly enhance security but users must prepare for potential access loss due to device changes or loss by establishing recovery options and backups.

Online Safety and Privacy
Getting Kids & Teens to Care about Cybersecurity
We all know Kids & Teens today spend a lot of time online, but that doesn't necessarily mean they know how to stay safe.

Online Safety and Privacy
Getting Kids and Teens to Care about Cybersecurity
We all know kids and teens today spend a lot of time online, but that doesn't necessarily mean they know how to stay safe.

Online Safety and Privacy
Guard your Gateway: Internet Router Tips
While internet routers aren't as flashy as the latest VR headset or electric truck, they make internet access in our homes and businesses possible.

Cybersecurity for Business
How to Improve Your Cyber Resilience
We often think of cybersecurity in terms of our physical health—we talk about computer viruses and cyber hygiene. Cyber resilience is another way to think about your online fitness.

Online Safety and Privacy
SIM Card Swap Scams
Protect your phone from this increasingly common scam.

Careers and Education
8 Awesome Cybersecurity Careers
Explore the diverse landscape of careers in cybersecurity!

Toolkits
Cyber Survival Guide
The spirit of adventure beckons you online!

External Resources
Cyber Career Pathways Tool - NICCS
NICCS is the premier online resource for cybersecurity training, education, and career information.

Online Safety and Privacy
Spring Clean Your Online Life
A sloppy digital life can make your data harder to find and leaves your personal information vulnerable to bad actors. With a few steps, you can keep yourself and your family safe online with a squeaky clean digital life.

Cybersecurity for Business
Identity Management? Zero Trust? PIM? Succeed by Getting the Basics Right.
In today’s rapidly evolving online landscape, terms like zero trust, PIM (or Privileged Identity Management), and a series of other acronyms can leave the average person scratching their head.

Online Safety and Privacy
Protect Your Wallet from Payment App Scams
"I made a typo and accidentally sent you $3,000! Can you please send it back?"

External Resources
Interactive Cybersecurity Career Map - NICCS
Are you interested in entering the cybersecurity workforce or advancing your career? Explore thousands of federal cybersecurity job openings across the country and outside of the United States by clicking on the map below or using the drop-down menu. Select an area to find open cybersecurity positions in your preferred city, state, country, and salary range.

Cybersecurity for Business
Churning the Digital Waters: Insights from the 2023 Gone Phishing Tournament
Even as our online worlds become more complex, phishing schemes remain the most common type of cybercrime, according to the FBI.

Cybersecurity for Business
Mandate MFA: Take a Bold Step Toward a Secure Future
Making online platforms, services, and devices more secure by default is a good idea. But is it easy? Is it popular?

Online Safety and Privacy
Lessons from Data Privacy Week 2024
Data is now a valuable commodity.

Online Safety and Privacy
Avoiding Voting Scams and Safeguarding Elections
Elections are a cornerstone of American society. However, there are bad actors who don't respect the sanctity of our voting process.

Online Safety and Privacy
Protecting Our Kids' Data Privacy is Paramount
Protecting our children's online data is of utmost importance.

Toolkits
Online Dating and Romance Scams
Love is in the air and online, but so are cybercriminals.

Online Safety and Privacy
Connected Car Cybersecurity: Drive Safe Online
Cars have joined the Internet of Things, and with any connected device, you should follow some security best practices to keep your car's system safe.

Online Safety and Privacy
Safeguarding Your Internet Activity with Incognito Mode
We'll explore how incognito mode works, how it can help protect your browsing data, and, importantly, ways it isn't a magic solution to all your privacy concerns.

Cybersecurity for Business
8 Biggest Small Business Cybersecurity Misconceptions
Small businesses are crucial to the American economy, employing nearly half of the workforce, yet they remain prime targets for cyberattacks.

Online Safety and Privacy
How to Protect Yourself Against Deepfakes
Deepfake technologies can be used to steal your identity even if you don’t use generative AI platforms.

Cybersecurity for Business
No Weak Links: Think About Your Human Firewall
When it comes to fostering a culture of cybersecurity at your organization, sometimes it's best to start with creating awareness of some basic behavior changes.

Online Safety and Privacy
What to Know About Stalkerware
Even though the use of stalkerware to spy on adults is against the law, these duplicitous bits of code still pop up on app stores.

Cybersecurity for Business
Business Email Compromise: What It Is and How to Prevent It
While it has a bland name, Business Email Compromise (BEC) refers to a specific, nasty type of cyberattack that targets businesses of all sizes.

Cybersecurity for Business
Consider Cybersecurity in Your Investment Decisions
As cyberattacks become increasingly frequent and sophisticated, investors have a crucial role in urging companies to prioritize cybersecurity alongside other risk factors.

Online Safety and Privacy
How to Take Back Control of a Social Media Account
Responding to social media account takeover.

Cybersecurity for Business
Securing Success: Talking to the Board About Cyber Risk
Cyber risk across all business levels influences operations, reputation, and compliance.

Online Safety and Privacy
Traveling Securely: A Comprehensive Guide to Protecting Your Digital Footprint While on the Move
Technology accompanies us everywhere these days, and that includes traveling for work. Cybersecurity remains paramount even when you are thousands of miles away from the office.

Online Safety and Privacy
The Benefits of Using a Random Password Generator for Safer Online Access
One way to ensure your passwords are awesome is by using random password generators, often included with password managers.

Cybersecurity for Business
How Cyber Education for Employees Safeguards Your Business
Training employees is the cheapest, easiest way to boost your cybersecurity. Your employees are your first line of defense against as threats, and they are also your greatest asset.

Cybersecurity for Business
The City Secure: Cyber Tips for Local Governments
City governments operate in an increasingly connected world where city services, constituent services, and information sharing are online, digital, and shared on many platforms.

Toolkits
Safe Online Holiday Shopping
Watch out for online shopping scams around the holiday season!

Online Safety and Privacy
Extra! Extra! Avoid Fake News!
What is Misinformation, Disinformation, and Malinformation?

Cybersecurity for Business
Keep Your Business Safe and Connected With IoT
We're living in an era when everything connects to the internet, from your fridge to your car.

Online Safety and Privacy
Securing Higher Ed: 5 Tips for Learning Safe Online
Technology and academia are now seamlessly intertwined. While tech can further educational opportunities for students, it also comes with risk as the ivory tower delves into the Wild West of the internet.

Online Safety and Privacy
Oh Behave! The Annual Cybersecurity Attitudes and Behaviors Report 2023
STUDY: 37% Intimidated, 39% Frustrated with Online Security Highlighting Digital Anxiety

Online Safety and Privacy
Don't Blame the Victim: 'Fraud Shame' and Cybersecurity
There is often a culture of blaming fraud victims for their predicament, rather than focusing on the criminal and the crime.

Cybersecurity for Business
How to Prevent and Recover from Ransomware
Ransomware is a hack with teeth, an attack aimed to cause extreme financial pain to its victims.

Online Safety and Privacy
How Your Phone Number is Exposed: Phone Number Leaks
Your phone number counts as personal data, and you don't just want anyone out on the internet to have it.

Online Safety and Privacy
K-12 Cybersecurity: Keep Kids Secure from Kindergarten to Graduation
Nowadays, kids aren't just polishing apples and stuffing their bookbags before heading to school, they're firing up laptops and using video chat with their teachers.

Online Safety and Privacy
Share with Care: Staying Safe on Social Media
Hey, friends, followers, lurkers, and posters: you don't have to overshare!

Online Safety and Privacy
Pull the Shades Down on Your Browsing With a VPN
Did you know that your cruise around the internet every day might not be totally private?

Cybersecurity for Business
Sell Safe Online: Advice for Online Retailers
Be open for business and closed to cybercriminals.

Online Safety and Privacy
What To Do When Your Data Is Breached
Oh no! You’ve been notified that your sensitive information has been stolen in a data breach.

External Resources
KC7 Cyber: Cybersecurity Training
By playing through dozens of realistic cybersecurity intrusions you will progressively learn how to spot traces of malicious activity.

Cybersecurity for Business
Common Cybersecurity Misconceptions Held By Small and Medium-Sized Organizations
Employees empowered with the resources and knowledge to protect your organization from cyberthreats is one of the best lines of defense you can have.

Cybersecurity for Business
Detect Incidents
How to detect a cyber incident in your business.

External Resources
Helpful Resources for SMBs
Here are helpful links from our sponsors, partners and friends to help you keep your business secure.

Online Safety and Privacy
What LGBTQ+ Communities Should Know About Online Safety
The internet is now crucial for connecting LGBTQ+ people and communities across the globe, but how can you hone your cybersecurity and protect your privacy?

Online Safety and Privacy
Google Users: Fire Up Google Passkeys
In May 2023, Google announced it was launching a new login system called "passkeys."

Online Safety and Privacy
Will Passwords Become a Thing of the Past?
What to know about passwordless authentication and passkeys.

Online Safety and Privacy
Parenting in the Digital Age: 7 Online Dating Rules for Your Teens
Parenting in our always-connected world comes with new challenges, new learning curves, and new awkward moments.

Online Safety and Privacy
Think Intelligent About Artificial Intelligence
Artificial intelligence, including so-called “large language models” like ChatGPT, has rapidly become a major talking point in the press, amongst governments, and maybe even in your office!

Online Safety and Privacy
Hacked Accounts: What to Do Right Now
If an online account has been hacked, it's important to act fast.

Careers and Education
My Cyber Journey – Jennifer Mahoney
Meet Jennifer Mahoney Senior Consultant II, Data Governance, Privacy & Protection at Optiv.

Online Safety and Privacy
Wedding Planning Cybersecurity: Say "I Do!" to Digital Bliss
Congrats on your nuptials! We have a few tips for keeping your Big Day secure.

External Resources
National Cybersecurity Center: Cyber Force Initiative (Colorado)
The purpose of the Cyber Force Initiative is to quickly help students transition to a career in cybersecurity. Once the program application is completed, students will have access to all courses offered at the NCC: IT Fundamentals, Security Pro, Network Pro, and CyberDefense Pro.

Careers and Education
My Cyber Journey – Tonya Drummonds
Meet Tonya Drummonds, Director of Security & Resiliency at Dell Technologies

Online Safety and Privacy
Why Identity Management Matters to You
Do you worry about the security of your personal data in our digital age?

Online Safety and Privacy
Stay Secure While You Work From Home
Remote work seems like it is here to stay for many of us even as the COVID-19 pandemic recedes in our collective rearview mirror.

Careers and Education
Cybersecurity Internships and Entry Level Jobs
Find a cybersecurity internship or entry level job with our partners!

Online Safety and Privacy
What We're Leaning About Data Privacy in 2023
We are living in an incredible time in history – a time when advancements in technology are creating tools that will help solve society’s greatest challenges and fuel the next wave of innovation.

Online Safety and Privacy
How to Tell If Your Computer Has a Virus and What to Do About It
Computer viruses make your devices sick, but you can usually help them heal if you act fast.

Online Safety and Privacy
Avoid Search Engine Ad Malware!
It's a new year and already there is a type of scam becoming extremely popular with hackers.

External Resources
CybersecurityDegrees.org: Cyber Degree Finder
To help you find your dream job, we have resources on schools offering cyber degrees, plus information on career paths, professional certificates, free online courses in security topics, and more.

Online Safety and Privacy
Online Romance and Dating Scams
Love is in the air and online, but so are cybercriminals

Online Safety and Privacy
Public Computers and Wi-Fi
Surf safe when using public computers and networks.

Online Safety and Privacy
What to Do if Your Password Manager Is Breached
What should you do if your password manager is breached?

Careers and Education
My Cyber Journey – Shawnte Arrington, Support, Technical Account Manager, Tanium
Meet Shawnte Arrington, Support, Technical Account Manager at Tanium

Online Safety and Privacy
What Is Data Privacy?
When you think of privacy, what comes to mind? Closing your window shades? Keeping your phone screen locked? Shutting the door when you have a sensitive conversation?

Online Safety and Privacy
10 Online Safety Tips for Gaming
Play safe while gaming.

Online Safety and Privacy
Dongles, Sticks, Drives, and Keys: What to Know About Removable Media
If you find a USB drive or other removable piece of media in the wild, DO NOT plug it into your computer! Let's break down why.

Online Safety and Privacy
How to Be an Online Privacy Snob
Take control of the data you share by being picky.

Online Safety and Privacy
Securing Your Home Network
A protected home network shuts out cybercriminals, allowing your family to use the internet more safely.

Cybersecurity for Business
Small Business Quick Wins
Follow these "quick wins" to secure every aspect of your small business.

Online Safety and Privacy
Online Shopping
Online shopping may be convenient but it can present many opportunities for scammers and cybercriminals.

External Resources
Best-Trade-Schools.net: Trade Schools Guide
As technology advances rapidly, becoming a Cyber Security Specialist is a smart and timely career choice. This booming field is projected to be worth over $10.5 trillion by 2023, playing a crucial role in safeguarding national security.

Online Safety and Privacy
Take Control of Your Data
All your online activity generates a trail of data.

Cybersecurity for Business
4 Simple Steps to Better Protect Your Company from Cyberattacks
Cyberattacks can happen to companies of all sizes.

Cybersecurity for Business
Advancing Collective Risk Management Efforts in the Financial Sector
The protection of our clients and customers from cyber threats is a foundational part of our business.

Cybersecurity for Business
The Security Culture Connection
Have you noticed the phrase “security culture” being used a lot recently? It’s become a bit of a security phrase de jour. That’s both a good thing and a bad thing.

Online Safety and Privacy
Only half of teens agree they "feel supported online" by parents
Not enough children and teenagers trust their parents to support them online, and not enough parents know exactly how to give the support their children need.

Cybersecurity for Business
6 Ways to Help Employees be Privacy Aware
Promote awareness about privacy, safeguard data and enable trust throughout the workplace with these tips.

Cybersecurity for Business
Cybersecurity awareness starts with people: Microsoft helps you and your team to #BeCyberSmart
Vasu Jakkal, CVP at Microsoft, emphasizes the importance of cybersecurity education for individuals and organizations.

Online Safety and Privacy
What About Password Manager Risks?
In the new Password Policy ebook, What Your Password Policy Should Be, KnowBe4 recommends that all users use a password manager to create and use perfectly random passwords.

Cybersecurity for Business
Cybersecurity collaboration as a national imperative
Bobbie Stempfley emphasizes the urgent need for a collaborative cybersecurity ecosystem to effectively combat the increasing frequency and severity of cyberattacks

Cybersecurity for Business
Building a Security Culture: The Foundation of a Secure Organization
Creating strong cybersecurity defenses for any organization requires a lot of important elements. Everyone knows a strong firewall is an essential first line of defense.

Careers and Education
My Cyber Journey – Jeremy Daniels, Cyber Analyst at HPE
Meet cyber analyst and HBCU grad, Jeremy Daniels.

Online Safety and Privacy
‘It’s easy to stay safe online’ with these 4 steps (plus 1)
When it comes to cybersecurity, good behavior can be rewarding.

Cybersecurity for Business
Making Cybersecurity Relevant for Consumers: The Case for Personal Agency
As Cybersecurity Awareness Month kicks off, one of the questions we often hear is “does consumer education really make a difference?”

Careers and Education
My Cyber Journey – Monique Head
Meet Monique Head, Founder of CyberTorial.org and Sr. Partner, Information Security, Communications, Awareness & Education at Netflix.

Online Safety and Privacy
Raising Digital Citizens
We all know the internet is a fantastic world of learning and entertainment for kids, but, like the real world, there can be dangers, too.

Careers and Education
Reinforcing Cybersecurity: Start with a Diverse Workforce
Looking to reinforce your company’s cybersecurity strategy? A good place to start is to cultivate a diverse workforce.

Online Safety and Privacy
Best Practices for Security and Privacy Settings
Want to lead a Stay Safe Online lifestyle, but don't know where to start?

Toolkits
Teach Others How to Stay Safe Online: Volunteer Toolkit
We're calling on all security professionals to share their expertise and volunteer to teach your community about online safety.

External Resources
Coursera: Developing a Program for Your Business Specialization
Master the Fundamentals of Cybersecurity. Learn to assess cyber threats and protect business information assets.

External Resources
Coursera: Introduction to Cyber Security Specialization
Cyber Security. An introduction to modern information and system protection technology and methods.

External Resources
LinkedIn Learning: Cybersecurity Foundations
Set a rock-solid foundation for your network, users, and data by learning about the basics of cybersecurity.

External Resources
Great Learning: Advanced Cyber Security - Threats and Governance
Learn solutions for cyber-attacks with Advanced Cyber Security-Threats and Governance free course

External Resources
Skill Share: Go From Zero to Hero
The field of technology is growing exponentially with the IT sector flourishing every day. Amidst such growth of the industry and increased concern for privacy, the demand for security is rising. Cybersecurity has become an everyday struggle for many businesses. Recent trends and statistics reveal that there is a huge increase in hacked and breached data from very common sources at workplaces. So go for this course to get a better understanding of cyber security!

Online Safety and Privacy
Password Managers
Don't pass on password managers. Learn more about these useful tools.

Careers and Education
How Free Pizza Led to a Cyber Career
A Chat with Bill.com’s Rinki Sethi

Online Safety and Privacy
You Can Stop Cyberbullying As A Kid!
As a kid using the internet, you've probably heard of cyberbullying. Maybe you or a friend has experienced it.

Online Safety and Privacy
The Modern Teen’s Guide to Handing Out L’s to Cyberbullies
Cyberbullying can make you feel like you can't really be "you" online. Here's what to do.

Online Safety and Privacy
Parents and Educators: What to Do About Cyberbullying
Have you ever texted or posted something online that you would never say to someone in person? You’ve probably experienced how the internet's anonymous nature can sometimes bring out the worst in people.

Online Safety and Privacy
10 Must-Know Tips For Keeping Your Personal Data Safe
The internet has become a vital aspect of our lives.

Cybersecurity for Business
Identity Management and the Second Half of the Chessboard
Ray Kurzweil's concept of the "second half of the chessboard" illustrates how exponential growth in technology and data management can lead to significant economic impacts and inefficiencies if not effectively managed.

Online Safety and Privacy
Secure Your Home
Internet-connected devices are helping homeowners increase efficiency, reduce costs, conserve energy and a whole host of other benefits.

Cybersecurity for Business
9 Security Questions Business Owners Must Ask Vendors
No matter the nature or size of your company, you need to think about cybersecurity in our connected present. This doesn't just mean your own operation's cybersecurity, but the security of every vendor you do business with.

Careers and Education
From Librarian to Cyber Pro
A Chat with the @InfoSecSherpa Tracy Z. Maleeff

Cybersecurity for Business
Cybersecurity: 3 Things Every Small Business Owner Should Know
Cyber attacks can be devastating, and they are increasingly common for small to mid-sized businesses.

Online Safety and Privacy
Respect Privacy
Respecting the privacy of your customers, staff, and all other stakeholders is critical for inspiring trust and enhancing reputation.

Cybersecurity for Business
Covid-19 Cybersecurity Resources for Small Businesses
To respond to the global pandemic and deliver timely information and resources to the nation’s small business community, the National Cybersecurity Alliance’s CyberSecure My Business program created the COVID-19 Small Business Cybersecurity Series.

External Resources
Additional Resources for Businesses
Frameworks, assessments, and guides from across the web.

Cybersecurity for Business
Identify Your “Crown Jewels”
Take an inventory of your business's most valuable assets.

Cybersecurity for Business
Protect Data and Devices
Secure the "crown jewels" of your business.

Cybersecurity for Business
Recover From Cyber Incidents
How to help your business recover from a cyber incident.

Cybersecurity for Business
Respond to Cyber Incidents
Do you have a plan in place to respond to cyber incidents at your business?

Cybersecurity for Business
Cybersecurity, It's More Than IT
As our lives become more digital, the risk of cybercrime grows, making strong cybersecurity measures essential not only for data protection but also for safeguarding customer information.

Careers and Education
Forestry Expert to Cybersecurity Manager: A Chat with Discover’s Sunil Mallik
Despite common perceptions, cybersecurity professionals come from all different walks of life.

Online Safety and Privacy
Talking to Kids & Teens about Security and Privacy
In today’s world, digitally connected families must think about safety and security both online and offline.

Online Safety and Privacy
Online Safety Tips For Older Adults
Just as you fasten your seat belt before driving, take precautions before using the Internet to be sure you are safe and secure.

Online Safety and Privacy
Parental Controls
As a parent, how do you stay involved in your child’s digital life?

Online Safety and Privacy
Talking to Kids and Teens about Security and Privacy
In today’s world, digitally connected families must think about safety and security both online and offline.
External Resources
American Indian Science & Engineering Society: AISES Membership
Opportunities and Resources for Native Students in STEM

External Resources
ApprenticePath: Discover Your Career Path
Jumpstart your career via paid apprenticeships

External Resources
Bold.org: Computer Science Scholarships
The Best Scholarships for Prospective Computer Science Professionals with Upcoming Deadlines

External Resources
The Center for Infrastructure Assurance and Security (CIAS): National Collegiate Cyber Defense Competition
Established in 2001 as part of UTSA’s creation of a cybersecurity program, the CIAS is a research center on a mission to secure the nation’s infrastructure and foster a Culture of Cybersecurity.

External Resources
Culture of CybersecuriTy: Kids Activities
The CIAS K-12 Cybersecurity Program is designed to introduce students to cybersecurity education and possible career paths in STEM disciplines, especially cybersecurity. To increase interest and learning capabilities, this initiative is centered around the CyBear™ family.

External Resources
Code.Org: Computer Science at Home
Anyone can learn Computer Science. Start coding today.

External Resources
Cyber.Org: Browse Free Cyber Curricula
CYBER.ORG empowers educators to teach cyber confidently, resulting in students with the skills and passion needed to succeed in the cyber workforce.

External Resources
Cyber.org: Cyber@Home
There is something here for everyone with fun, project-based activities for elementary, middle, and high school students.

External Resources
Fastport and Purdue University: Purdue Cyber Apprenticeship Program
These programs all provide earn and learn opportunities for participants with compensated experiential, effort-based employment and an industry-recognized educational component.

External Resources
CyberScient: Kids Platform
Share your successes and struggles with a community of like-minded students who share your artistic goals on our public forums.

External Resources
CyberDegrees.org: Cybersecurity Degrees
There are hundreds of different cybersecurity degrees.

External Resources
Cybersecurity Guide: K12 Cybersecurity Guide
If you are a young person interested in pursuing a career in technology, it can be challenging to know where to start. While some schools may offer curriculum in technology, cybersecurity isn’t typically covered.

External Resources
Girls Who Code: College Programs
Girls Who Code offers a wide range of programs designed to support college-aged students and early career professionals (18-25) in persisting in their computer science education and succeeding in their first internships and jobs.

External Resources
IKeepSafe: Faux Paw Cybersecurity Superheros activities
Meet Faux Paw, an adventurous six-toed cat who loves technology. These fun books teach rules to promote the safe and healthy use of digital devices. Read or watch Faux Paw’s adventures using links below each book’s description.

External Resources
IKeepSafe: Data Privacy Educator Training Course
Growing concerns about student data privacy can create hurdles for K12 educators working to expand access to edtech and digital innovations. EduPaths and iKeepSafe partnered to create four courses centered around data privacy in education.

External Resources
Microsoft: Microsoft Learn for Educators
Equip your students with AI and tech skills for today—and tomorrow

External Resources
Natives in Tech
Cultivate a tech ecosystem of Native technologists crafting free and open source technology for Native communities.

External Resources
National Initiative for Cybersecurity Careers and Studies: Cybersecurity in the classroom
Are you a Kindergarten through 12th grade (K-12) teacher or educator looking to incorporate cybersecurity into your lesson plans? Do you want to help your students learn about cyber concepts and career opportunities?

External Resources
National Initiative for Cybersecurity Careers and Studies: Veterans User Guide
Veterans and military personnel looking to transition out of the armed forces, are you ready for your next mission?

External Resources
Carnegie Mellon University: picoCTF.org
Watch our monthly YouTube lecture series on intro cybersecurity principles.

External Resources
Breaking Into Cybersecurity: Podcast by By Renee Small/Christophe Foulon
It’s a conversation about what you did before, why did you pivot into cyber, what the process you went through Breaking Into Cybersecurity, how you keep up, and advice/tips/tricks along the way.

External Resources
GenCyber: GenCyber Camps
GenCyber provides cybersecurity experiences for students and teachers at the secondary level.

External Resources
Roadtrip Nation: Information Security Engineers Career
Information Security Engineers Career Pathway

External Resources
Cyber Center of Excellence (CCOE): Cyber Center of Excellence (CCOE) Cyber Career Map
Chart your personal path to a cyber career with the exploration dashboard and zoom in for jobs, education, resources and much more.

External Resources
Salesforce: Cybersecurity Learning Hub
Learn in-demand skills and build your cybersecurity career path

External Resources
Temple University: Organizations We Love
These are the amazing 309 organizations that strive to make tech and info/cybersecurity opportunities and experiences accessible to everyone [1,2,3], and so they are the Organizations We Love (OWL)

External Resources
Temple University CARE Lab: Collegiate SECTF competition
The CARE Lab hosts social engineering competitions every summer! This event is open to high school, undergraduate, and graduate students. We partner with industry, government, and nonprofits to provide students with the best possible experiences and exposure to real world events.

External Resources
SMARTFENSE – Videojuegos educativos: Las aventuras de Gupi
Las Aventuras de Gupi es un videojuego lanzado por SMARTFENSE en el cual un pez llamado Gupi necesita la ayuda del usuario para no morder el anzuelo.

External Resources
Palo Alto Networks: Cyber A.C.E.S. Program
Cyber A.C.E.S. provides the cybersecurity basics students need to have safer online experiences and become good digital citizens. Lessons are designed so they can be facilitated by anyone, regardless of their knowledge level, with each module tailored to a specific age group.

External Resources
Code.org: Code Break
A weekly challenge to engage students of all abilities, even those without computers.

External Resources
TryHackMe: Cyber security Training
Learn cyber security with fun gamified labs and challenges

External Resources
Women’s Society of Cyberjutsu (WSC): Career Resources
The Women’s Society of Cyberjutsu (WSC), a 501(c)3 non-profit, is dedicated to raising awareness of cybersecurity career opportunities and advancement for women in the field, closing the gender gap and the overall workforce gap in information security roles.

External Resources
Symantec and AAUW: STEMpack: Cyber Security
Cyber Security curriculum to inspire and introduce participants to cyber security and computer science.

External Resources
CISA: Cybersecurity Workforce Training Guide
Released August 2021, the Cybersecurity Workforce Training Guide is for current and future federal, state, local, tribal, and territorial (SLTT) staff looking to expand their cybersecurity skills and career options.

External Resources
Center for Internet Security: Why Consider a Career in Cybersecurity?
As technology evolves and cybersecurity threats continue to grow, the need for qualified cybersecurity candidates only intensifies. But it's not always easy to fill these positions. That's why starting a career in cybersecurity is worth considering, especially for students or individuals who are looking for a career change.

External Resources
CompTIA: State of the Tech Workforce
CompTIA’s State of the Tech Workforce, also known as Cyberstates, provides the definitive guide to tech workforce trends, the number of available jobs in technology, and tech industry employment statistics by state, metro area and nationwide.

External Resources
C.A.K.E: Cyber Academy For Kids through Empowerment
CAKE - Cyber Academy for Kids through Empowerment - Founded by two industry professionals in the field of cybersecurity and information technology is teaching elementary, middle and high school students the fundamentals of cybersecurity.

External Resources
Cybersecurityjobs.com Training Fund
Our mission is to connect cybersecurity professionals with organizations in need of cybersecurity talent but putting people and employers together is just one side of the equation.

External Resources
Cyber Seek
CyberSeek provides detailed, actionable data about supply and demand in the cybersecurity job market.

External Resources
Cyber Virginia: VIRGINIA VETERANS CYBER TRAINING PILOT
In an effort to address the growing demand of over 17,000 cyber jobs available across the state of Virginia, organizations have joined together with the Commonwealth of Virginia to sponsor free cyber training and industry-recognized certifications as part of a pilot program for veterans who want to live and work in the Commonwealth in the cyber field.

External Resources
Cybrary: Cybersecurity Training and Career Development
Cybrary’s structured, hands-on cybersecurity courses and training empowers professionals to better protect their organizations.

External Resources
Cyversity
To achieve the consistent representation of women, underrepresented communities, and all veterans in the cybersecurity industry through programs designed to diversify, educate, and empower.

External Resources
Empow(H)er Cybersecurity
The goal of Empow(H)er Cybersecurity is to provide a platform for all women of color to grow their networks, be inspired, and feel empowered.

External Resources
ESET: Women in Cybersecurity Scholarship
Two $10,000 scholarships will be awarded to graduate/undergraduate women pursuing a career in cybersecurity.

External Resources
Fortinet: Veterans Program
Transitioning the military community into the cybersecurity industry through world class training.

External Resources
Future Learn: Cybersecurity Courses
Explore online criminal activity and undergo cyber security training to protect yourself and others online, or prepare for a career in cyber security.

External Resources
Girl Scouts: Ambassador Cybersecurity Safeguards Badge: Guard Your Movements
Identify data vulnerabilities in a typical day

External Resources
Girl Scouts: Brownie Cybersecurity Basics Badge Activity: Tech Scavenger Hunt
Do a scavenger hunt to explore how technology replaces everyday objects.

External Resources
Girl Scouts: Cadette Cybersecurity Safeguards Badge Activity: Inventory Your Digital Presence
Explore some of the types of data collected by websites and apps.

External Resources
Girl Scouts: Daisy Cybersecurity Basics Badge Activity: Protect Your Treasure
Explore how to keep something safe, like a computer, with layers of protection.

External Resources
Girl Scouts: Junior Cybersecurity Basics Badge Activity: Roll with Protocols
Explore how computers send and receive information when sending messages.

External Resources
Girl Scouts: Senior Cybersecurity Basics Badge Activity: Identify Functions and Privileges
Explore how cybersecurity professionals keep computer networks safe.

External Resources
Hacker Highschool
Hacker Highschool (HHS) started in 2003 as a means of teaching teens problem solving, resourcefulness, and empathy through hacking.

External Resources
Center for Cyber Safety and Education: Scholarships
The scholarships are part of an effort to bridge the cybersecurity workforce gap by providing future cybersecurity professionals across the globe with scholarships to prepare them for a rewarding career in this important field.

External Resources
(ISC)2: Webcast series
ISC2 produces complimentary webinars with high-quality content on an ongoing basis. Advance your knowledge on emerging issues and stay up-to-date on global trends and hot-button topics.

External Resources
NICE K12 Cybersecurity Education Conference
The NICE K12 Cybersecurity Education Conference is the premier event for K-12th grade cybersecurity educators.

External Resources
Microsoft: MakeCode
Microsoft MakeCode is a free online learn-to-code platform where anyone can build games, code devices, and mod Minecraft!

External Resources
National Cyber Scholarship Foundation
The initiative is designed to identify talent in high school and college students, and includes a comprehensive set of programs and supports that work together to create a more assured pipeline for building the next generation of cyber talent.

External Resources
NextGen CyberTalent: NextGen Candidate Programs
NextGen Cyber Talent conducts a cohort every month to educate and train underserved, underprivileged and diverse talents in Cybersecurity, risk, and compliance domains.

External Resources
National Initiative for Cybersecurity Education: Cybersecurity Career Awareness Week
Cybersecurity Career Week is a campaign to promote the discovery of cybersecurity careers and share resources that increase understanding of multiple learning pathways and credentials that lead to careers.

External Resources
National Initiative for Cybersecurity Education: Free and Low Cost Online Cybersecurity Learning Content
The following links are for free and low-cost online educational content on topics such as information technology and cybersecurity

External Resources
NICE: The Challenge of That First Job in Cybersecurity – Entry Level Roles and How to Qualify
This webinar will explore the unique challenges and opportunities from the perspective of educators, employers, and job-seekers.

External Resources
Palo Alto Networks: Cybersecurity Academy
World-class curriculum and programs specifically designed for K-12, colleges and universities.

External Resources
Palo Alto Networks: Certified Cybersecurity Entry-Level Technician (PCCET) program
The PCCET certification covers fundamental cybersecurity, network security, cloud security, and SOC security principles.

External Resources
PBS: The Cybersecurity Lab
Whenever we go online—to shop, chat with our friends, or do anything else—we put ourselves at risk of cybercrime. Computer viruses can corrupt our files, hackers can steal our data, and criminals can trick us into revealing sensitive information. But luckily there are simple steps we can take to protect our digital lives.

External Resources
RangeForce: Cybersecurity Training
Take your cyber skills to the next level. Access a limited number of hands-on cybersecurity training modules for free, forever.

External Resources
SANS: Diversity Cyber Academy
Facing the cybersecurity challenge, SANS Diversity Cyber Academy offers cybersecurity training scholarships for minorities and women.

External Resources
SANS Institute: Free Cyber Security Training
Learn the Fundamentals of Cyber Security for Free!

External Resources
Scholastic: #CyberSmarts
As your kids discover the power of the internet, make discussing the do’s and don’t’s of online behavior a priority.

External Resources
Tynker: Coding for Kids
Tynker is the fun way to learn programming and develop problem-solving & critical thinking skills.

External Resources
US Cyber Challenge
USCC’s goal is to find 10,000 of America’s best and brightest to fill the ranks of cybersecurity professionals where their skills can be of the greatest value to the nation.

External Resources
Katzcy: US Cyber Games
The mission of the US Cyber Games® is to bring talented cybersecurity athletes, coaches, and industry leaders together to build an elite US Cyber Team for global cybersecurity competition.

External Resources
Air Force Association: Elementary School Cyber Education Initiative
The CyberPatriot Elementary School Cyber Education Initiative (ESCEI) is a set of three fun, interactive learning modules aimed at increasing grade K-6 students’ awareness of online safety and cybersecurity principles. Supplemental activities are also available to get students collaborating with each other about their newly learned cyber skills!

External Resources
Varonis: Which Cybersecurity Career Is Right For Me?
Finding the right career path in the cybersecurity industry isn’t always easy. We interviewed cybersecurity experts to find out what inspired them!

External Resources
University of Washington: Access Computing Team
AccessComputing helps students with disabilities pursue degrees and careers in computing fields through inclusive academic and mentoring programs.

External Resources
Black Girls Code
Since 2011, Black Girls Code has supported girls of color in tech through coding education and more. We partner with schools and organizations to offer a range of programs, both in-person and virtual, for ages 7-25.

External Resources
Women in Security and Privacy
We are advancing women and underrepresented communities to lead the future of security and privacy.

External Resources
Kalinda Raina: Raising the Digital Future
Let's talk real world solutions for raising children in a world where every bad decision they make will exist on the Internet for any curious college admission counselor or job recruiter to find.

External Resources
CompTIA: Cybersecurity: Skills, Tips, and Advice From Our Panel of Experts
CompTIA has brought together a panel of cybersecurity experts to share their knowledge and experience with seasoned IT pros and those interested in starting a career in cybersecurity.

Online Safety and Privacy
COVID-19 Security Resource Library
Free resources to help individuals and organizations through the COVID-19 pandemic.

Toolkits
Cyberbullying
Cyberbullying can range from embarrassing or cruel online posts or digital pictures, to online threats, harassment, and negative comments, to stalking through emails, websites, social media platforms and text messages.

Online Safety and Privacy
Malware, Viruses and Botnets
These 3 types of cybercriminal tools are common online, and you as an internet user might come across them from time to time.

Online Safety and Privacy
Security Awareness Episodes
Watch and download this fun series on security best practices!

Cybersecurity for Business
Did You Notice a Shift in Attitudes Towards Awareness Training at This Year's NCA Conference?
Mike Polatsek, Co-founder and CSO at CybeReady, reflects on Convene: Florida.

Cybersecurity for Business
Top 10 Security Issues in Enterprise Cloud Computing
As a CISO, you know the list of security issues in enterprise cloud computing seems to always be growing.

Careers and Education
Tech Lover...but Cyber Late Bloomer
A Conversation with Prajakta "PJ" Jagdale of Palo Alto Networks

Online Safety and Privacy
Is working on your smartphone a risky business or are you cybersecure?
The increasing use of mobile devices in our personal lives has led to a growing acceptance of smartphone usage at work.

Online Safety and Privacy
Stalkerware
BEFORE YOU CONTINUE: Stalkerware apps can track your browsing history so if you suspect that stalkerware has been installed on your device DO NOT USE IT to research support services such as advocacy, shelter, court information or emergency services.

Online Safety and Privacy
Tips for Higher Education Online Teaching and Learning
As online and hybrid learning environments become more popular, it is essential for students, faculty, and staff to adopt key cybersecurity practices.
Online Safety and Privacy
K-12 Online Learning
Online learning is here to stay. Many K-12 schools will probably use some blend of fully online learning and in-person teaching for the foreseeable future.

Online Safety and Privacy
Mobile Devices
That smartphone in your pocket, that tablet on your coffee table or that laptop on your desk contains a treasure chest of information about you, your friends and your family.

Online Safety and Privacy
A Teacher’s Guide To Student Online Safety
Students are more connected than ever before thanks to the internet.

Careers and Education
Lawyer, Children's Book Author, and Career Changer to Cybersecurity
Meet Zinet Kemal

Cybersecurity for Business
Human Challenges in Implementing Multifactor Authentication (MFA)
How to implement an effective MFA program in your business.

Cybersecurity for Business
How Smart Card Technology Uses Network Security
The concept of network security has been in existence for decades. With organizations using more sensitive information, the need to create policies that would limit access and control of a network has increased.

Online Safety and Privacy
7 Tips for a Safer Internet of Things
The "Internet of Things" (IoT) has been a realm of technological innovation that has grown exponentially over the past decade.

Cybersecurity for Business
As an Employee or a Business Owner, You Need to Be Cyber Aware and Resilient
As our world becomes increasingly connected, it’s more important than ever to be cyber aware. There’s no question, cyber attacks are evolving in sophistication and attackers are broadening the entities they’re willing to target.

Cybersecurity for Business
The Top Cybersecurity Trends for 2022
Here are the top three cybersecurity trends we think are worth watching as we approach 2022

Online Safety and Privacy
Be Cyber Smart: A guide to help you do your part
Let’s brush up on cyber hygiene — basic steps we can take to stay safe in a connected world.

Cybersecurity for Business
5 Cybersecurity Trends in 2021
As remote work becomes the norm post-COVID-19, the cybersecurity landscape is evolving rapidly, presenting new threats and necessitating a reassessment of strategies to protect organizations from increasingly sophisticated attacks.

Careers and Education
From math-hater to DEFCON-lover: An unlikely path to Cybersecurity
Would you let a fear of math scare you away from a career in cybersecurity?

Online Safety and Privacy
Reporting Matters – even for a Smishing Message
With the increased use of mobile devices to manage so much of our lives, it’s no surprise scammers have moved to this medium to target your sensitive information.

Online Safety and Privacy
7 Tips to Manage Your Identity and Protect Your Privacy Online
Worried about how much of your private information is on the internet and vulnerable to theft or misuse? You’re not alone.

Online Safety and Privacy
Spotting a Vaccine Phishing Scam: Can You Find the Red Flags?
Many of us have seen COVID-related scams hit our inboxes. It’s no secret that scammers try to take advantage of times of panic and uncertainty, when people are most vulnerable, to steal personal information.

Online Safety and Privacy
Take It Personally: Ten Tips for Protecting Your Personally Identifiable Information (PII)
When we're online, we accumulate a significant amount of personally identifiable information (PII), which can be exploited by cybercriminals.

Cybersecurity for Business
The Impact of Data Breaches and Cyberattacks on SMBs and Their Employees
It is always important for businesses to ensure their employees work securely, both at the office and home, as threat actors continually look for ways to attack.

Cybersecurity for Business
How to Run a Virtual Cybersecurity Awareness Month Campaign
Engage your employees online during Cybersecurity Awareness Month.

Online Safety and Privacy
Security Awareness: Episode 4 – Phishing and Ransomware
We’re bringing you another free security awareness video! These videos are brought to you by Adobe, National Cyber Security Alliance, and Speechless Inc.

Online Safety and Privacy
Owning Your Privacy by Managing Your Digital Footprint
The information you share online can reveal more details then you intend and make you vulnerable to compromise.

Online Safety and Privacy
How to Secure and Maintain Your Digital Identity
Individuals must take proactive steps to safeguard their digital identities by being cautious about personal information sharing, connection requests, and message links.

Online Safety and Privacy
Sextortion: What to Look Out For and What to Do If You’re a Victim
An explanation of sextortion and how it works.

Cybersecurity for Business
How Your IT System Could Be at Risk from a Physical Attack
Don't overlook the physical risks to your IT system.

Online Safety and Privacy
The Secret Language of Emoji
Emoji appeared in 1999 with a set of 176 symbols that were meant to convey weather, traffic, technology and time. Today, there are 2,823 emoji that convey information across language, culture, lifestyle and diversity.

Cybersecurity for Business
You’ve Been Hacked: 5 Ways to Minimize the Damage
Getting hacked is a nightmare scenario for every business. Fifty percent of small businesses in the U.S. have experienced a cyberattack. And this fact is not surprising – most small businesses lack the advanced security resources and technology that large enterprises can afford.

Online Safety and Privacy
Stay Secure On Public Wi-Fi When Traveling
Twink twice before connecting to a public wi-fi network when you're on the go.

Online Safety and Privacy
Protecting Baby Monitors From Hacking
The use of Wi-Fi-capable baby monitors has become indispensable to many parents.

Cybersecurity for Business
How to Protect Your Customer Relationship Management (CRM) Data from Hackers
CRM systems are some of the most useful assets for an organization, enabling businesses to build meaningful customer relationships, find new prospective customers and drive revenues.

Online Safety and Privacy
Security and Privacy Tips for Cryptocurrency Holders
The cryptocurrency trend is definitely a big boom in today’s financial market.

Online Safety and Privacy
Data Privacy Is Crucial for the LGBT Community
It is vitally important to consider how compromised online privacy can specifically affect marginalized groups such as the LGBT community.

Online Safety and Privacy
Health Technology in the Digital Era – Benefits + Risks
Examining the evolution of health technologies and their implications for patient privacy and security.

Online Safety and Privacy
Health Information Privacy – Why Should We Care?
Recent data breaches involving health information pose significant risks to our online privacy. Learn how to protect your valuable health data.

Online Safety and Privacy
15 Online Security + Privacy Tips for College Students
You’re responsible for your own online security at college, so follow these tips to help you be safe and privacy-savvy on campus.

Cybersecurity for Business
Key Ways to Protect Your Business From Malware
Cyberattacks are a serious threat to businesses and consumers, with large-scale attacks having nationwide effects, thus making national security a serious concern.

Cybersecurity for Business
What Happens When Cyberbullies Join the Workforce?
Cyberbullying has been stereotyped in the media as a problem that occurs with teenagers, cell phones, sexualized photographs and social media.
