Online Safety and Privacy
Apr 6, 2021
|
Min Read
Spotting a Vaccine Phishing Scam: Can You Find the Red Flags?
Many of us have seen COVID-related scams hit our inboxes. It’s no secret that scammers try to take advantage of times of panic and uncertainty, when people are most vulnerable, to steal personal information.
Today, with the rapid development and distribution of COVID vaccines, many Americans are going online and sharing personal information to join waiting lists and book appointments before slots become filled. Scammers are altering their tactics to take advantage of this excitement. As we eagerly check our emails for vaccine updates and confirmations, it can be hard to tell the difference between a legitimate email and a phishing attempt.
The best way to protect yourself from bad actors is by learning to recognize the red flags. Knowing the red flags in advance will make you less likely to click on that convincing email. National Cyber Security Alliance board members, Cofense and Mimecast, captured real examples of phishing attempts, seen below. Test your knowledge and see if you can find the signs of a scam in these images.
This screenshot, captured by Mimecast, shows a typical phishing attempt. How many red flags can you find? Keep scrolling to see if you’ve found them all.

Several red flags of a phishing attempt can be found in this email:
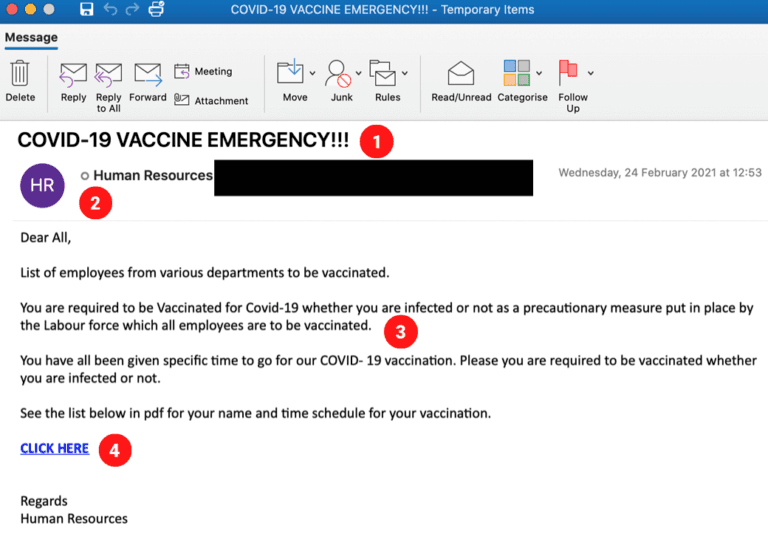
Subject Line – Note the use of all capital letters and exclamation points. The wording and format is used to create a sense of urgency, trying to get you to click on the email in a panic, quickly and without thinking.
Mimicking a trusted source – This phish, likely sent to the employees of a company, is pretending to come from a human resources department. Bad actors will pretend to be people or groups you may already know to gain your trust. If you are unsure if an email really came from someone, reach out to or call that person directly to double check.
Mistakes and misspellings – Poor grammar can be seen throughout the body of the email, as well as random capitalizations of certain words such as “Vaccinated”. One would expect an email coming from an organization’s HR department to use proper wording and grammar. The combination of weird formatting, capitalized letters, and strange grammar all make this email seem “phishy”.
Hyperlinks – The email content is trying to lead the recipient towards clicking on the hyperlink at the bottom of the email. Always be wary of clicking on links (and attachments) in emails, as they may lead you to a fraudulent site.
Mimecast suggests the following tips to avoid scams:
Be proactive. Go directly to your local government website/hospital to double check facts and get the correct information.
Be suspicious of emails, phone calls, or messages from people you don’t know, trying to get your attention with updates about the vaccines.
Always check URLs. Hackers are creating sites that look like official healthcare institutions and vaccine providers. Navigate directly to official websites such as CDC.gov and your state/city’s official website.
Use strong and unique passwords for all your accounts when signing up for an account and use MFA/2FA whenever possible.
Don’t connect to networks you don’t recognize. Research vaccine information on your secure home WiFi network, which should be protected by a strong password.
Be extra cautious if you’re using a company-owned device. Threat actors seek access to the organization you work for, with the intention of stealing data.
Make sure your device has the most current updates and patches.
Be on the lookout for Vishing attempts – Be very suspicious of any caller who asks you to share login information over the phone. A good rule of thumb for catching vishing and phishing attempts is to stop and ask yourself if you were expecting the call or message. If not, contact the company directly to verify if the message or call is, in fact, real.
The below phishing attempt, captured by Cofense, is a bit more detailed, but still contains many red flags:

Red flags in this phishing attempt:

Subject line – Again, note the use of all capital letters and phrase “very important information” trying to make the recipient click on the email without thinking.
Survey link – The URL is spoofing the popular polling platform SurveyMonkey, but note the incorrect spelling and lack of a top-level domain (the segment that typically follows the domain name, such as .com or .org)
Survey hyperlink – The box adjacent to the link appears when you hover over a URL. Hovering over a URL will show you the true destination of the hyperlink. The destination may not match the text in the email, as seen in this example. This is a major red flag that someone is trying to redirect you to an unsafe site.
Misspellings and mistakes – This phish has better grammar than the last, but errors such as “Survey’s” and the capitalization of “Today” show that something about the email is “phishy”.
Mimicking a trusted source – Again, this scammer pretends to be a member of an organization’s human resources department. However, this sender is a bit more detailed than the last. They’ve included a specific name and title: “Dawn, Director of Human Resources”, making it seem more likely this email comes from a legitimate sender.
Many emails, text messages, and phone calls are using more sophisticated messages, with less and less obvious red flags. Remember to read messages carefully. It is always important to slow down, double check the sender, and ask yourself if you were expecting the message or phone call in question.
Confense suggests the following tips to protect yourself against phishing:
Validate the source of the email against official government websites (eg. CDC, WHO, or local city and state health department websites).
If the sender is someone you typically interact with but the message seems ‘off’, validate with them over another channel (phone, text or new email message). It is possible their account may be compromised.
Never give away your personal information to untrusted sources, including your username and password.
Create unique usernames and passwords per website and / or applications. Many websites and apps now allow you to create a username that isn’t your email address.
Set up a password vault to store all these unique logins. Create a habit of opening the vault each time you’re creating a new login for a website or application.
Enable Multifactor (MFA or 2FA) for any website or application that has the capability. If your login information is obtained from a data breach, this is an added level of protection.
If you are notified of a data breach affecting your login information, change it immediately and update your vault.
Additional Resources:
Security Awareness Episode 4: Phishing and Ransomware, from NCSA, Adobe and Speechless Inc
Test your phishing knowledge, try Google’s Phishing Quiz
Cofense’s blog and free resource center
Mimecast’s blog and resource center
Mimecast’s report, “The Year Of Social Distancing”, on the security challenges of the new digital workspace.
Featured Articles
Tags



