Press Stories
Filter by Category:

Press
National Cybersecurity Alliance Receives 2025 CSO Award from Foundry’s CSO
National Cybersecurity Alliance Receives 2025 CSO Award from Foundry’s CSO

Press
Newsday: LI's Broadridge, Verint testing new Chinese chatbot DeepSeek for automation, efficiency

Press
Fox Tampa Bay: Tech experts warn of Valentine's Day romance scams as Meta takes steps to protect users

Press
ABC Philly: FBI issues warning on romance scams ahead of Valentine's Day

Press
Kiplinger: Hey Valentine, Beware of Catfishing Romance Scams

Press
PC Mag: Which AI ChatBot Collects the Least of Your Data?

Press
Gizmodo: The Knives are Coming Out for DeepSeek AI

Press
Data Privacy Week 2025 Press Release

Press
Vanity Fair: Is TikTok Really Worth Saving?

Press
Newsweek: PowerSchool Breach Victim Says Hackers Stole All Student Data

Press
The Huffington Post: LA Fire Donation Scams Are Everywhere. Here's How To Spot Them

Press
USA Today: Scammers may be taking advantage of the California wildfires - How to protect yourself

Press
The Wall Street Journal: Shun This Basic Cybersecurity Tactic and Become a Target for Hackers

Press
Washington Post: Congress funds removal of Chinese telecom gear as feds probe home router risks

Press
CNN: They were closing on their dream home. Then they fell for a little-known real estate scam

Press
Forbes: Watch For These Black Friday Scams—Especially Ones Created By AI

Press
Cybernews: How Cyber Hacks Might Change Under Trump's Presidency
Press
Candid Recognition
Candid Recognition

Press
Fortune: How election misinformation thrived online during the 2024 presidential race—and will likely continue in the days to come

Press
Forbes: Does Generative AI Suffer from Shiny Object Syndrome?

Press
Forbes: 55% Of Employees Using AI At Work Have No Training On Its Risks

Press
STUDY: Less Than Half of AI Users Trained on Security and Privacy Risks
STUDY: Less Than Half of AI Users Trained on Security and Privacy Risks

Press
Huffington Post: Are You Being 'Spoofed'? This Specific Type Of Scam Is Hard To Catch.

Press
Forbes: Seattle-Tacoma Airport Still Recovering From Weekend Cyberattack
Press
Business Insider: A former real-estate agent and her husband had to dip into retirement savings to buy a house after being scammed out of $63,000
Press
Fox News: Records of nearly 3 billion people stolen in massive data breach lawsuit

Press
Huffington Post: Take This 1 Step ASAP If Your Social Security Number Is Part Of National Data Leak

Press
CBS News: Hackers may have stolen the Social Security numbers of many Americans. Here's what to know.

Press
CBC: Florida company faces multiple lawsuits after massive data breach

Press
CNBC: 2.9 billion people may have had Social Security numbers, other financial data compromised. What it means for you

Press
Global News: CrowdStrike outage, cyberattacks a ‘wake-up call’ to dangers of big tech reliance

Press
Politico: White House responding to massive IT outage

Press
CNN: CDK Global outage has been hamstringing car dealerships for days. Experts say that’s the new normal for cyberattacks

Press
A.P. News: Car dealerships in North America revert to pens and paper after cyberattacks on software provider

Press
Reuters: CDK hack upends US auto industry, sending dealers back to paper forms

Press
The New York Times: What the Arrival of A.I. Phones and Computers Means for Our Data

Press
National Cybersecurity Alliance receives 2024 CSO Award from Foundry’s CSO
National Cybersecurity Alliance receives 2024 CSO Award from Foundry’s CSO

Press
National Cybersecurity Alliance receives 2024 CSO Award from Foundry's CSO
National Cybersecurity Alliance receives 2024 CSO Award from Foundry's CSO

Press
The Guardian: How Apple plans to usher in ‘new privacy standards’ with its long-awaited AI

Press
CBS News: 5 Tips for Safe Online Shopping

Press
ArtNet NewS: ‘The Scams Keep Proliferating’ - Christie’s Historic Outage Reveals the Art World’s Digital Vulnerabilities

Press
National Cybersecurity Alliance Relaunches Cybersecure My Business Program
National Cybersecurity Alliance Relaunches Cybersecure My Business Program

Press
The Sun: RED ALERT How Chinese hackers could HIJACK EVs to crash cars and trap drivers in terrifying sabotage attacks

Press
New York Post: TikTok vows legal fight after Biden signs ‘unconstitutional’ ban - ‘We aren’t going anywhere’
Press
ExtremeTech: Meta Will Begin Labeling AI-Generated Content. Is It Enough to Combat Misinformation?
Press
NBC10 Boston: Don't forget your digital devices during your spring cleaning

Press
Fox Business: The most common tax season scams - and how to protect yourself

Press
The Verge: Will the Apple antitrust case lawsuit affect your phone’s security?

Press
IT Brew: Why NCA Exec Director Lisa Plaggemier assumes no one cares

Press
Forbes: The TikTok Ban Is Truly An Issue Of National Security

Press
Reuters: Healthcare providers hit by frozen payments in ransomware outage

Press
Washington Post: How a health-care cyberattack may affect your prescription drug access

Press
The New York Times: A Cyberattack on a UnitedHealth Unit Disrupts Prescription Drug Orders
Press
The Street: How the company that traced fake Biden robocall identifies a synthetic voice
Press
InformationWeek: NCA’s Plaggemier on Finding a Path to Data Privacy Compliance

Press
NextGov: NCA celebrates National Data Privacy Week while CISA eyes new cybersecurity guidelines

Press
Security Boulevard: News alert - NCA’s Data Privacy Week webinars highlight data protection for consumers, businesses

Press
Business Insider: An Innocent-looking Instagram Trend could be a gift to hackers, according to a cyber-security expert

Press
C&G Newspapers: Experts urge consumers to watch out for scams this holiday season

Press
Gizmodo: How To Spot Misinformation & Scams On TikTok

Press
KIRO7: Medina Police Department warns of imposter pretending to be member of local agencIE
Press
CBS News: How to turn off iPhone's new NameDrop feature, the iOS 17 function authorities are warning about

Press
Bloomberg Markets: Cybersecurity Concerns amid Global Conflicts

Press
Michigan Department of the Attorney General: Attorney General Warns Gen Z May Be More Likely Scam Victims

Press
IT Brew: How to get young people (and everybody else) to care about cybersecurity

Press
Smart Industry: Cybersecurity stakeholders praise AI executive order—but say it’s just a start

Press
WhioTV7: Why scammers target teenagers, parents of young children
Press
Nasdaq: The Potential Cyber Threats of Visual and Audio AI Incorporation

Press
Signal: New AI Regulation to Create New Standards for Developers

Press
Axios: New cyberattack disclosure rules make companies anxious

Press
Engadget: The Best Password Managers for 2023

Press
Wharton on Sirius XM: Lisa Plaggemier on Wharton Business Daily

Press
Dark Reading: From Snooze to Enthuse: Making Security Awareness Training 'Sticky'
Press
National Cybersecurity Alliance Launches Kubikle, A New Video Web Series Demystifying Cybercrime
National Cybersecurity Alliance Launches Kubikle, A New Video Web Series Demystifying Cybercrime
Press
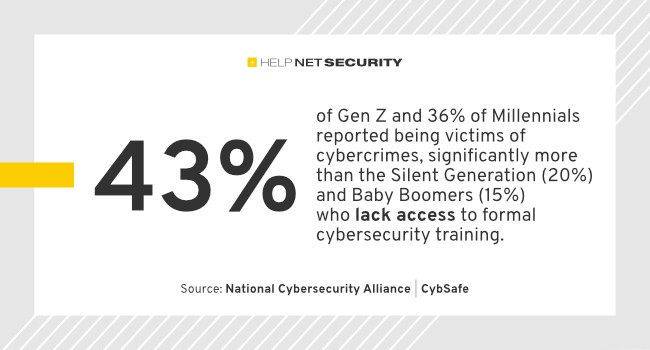
Help Net Security: Incentivizing secure online behavior across generations

Press
DPO Download Podcast: Episode 11 - National Cybersecurity Alliance

Press
National Cybersecurity Alliance Kicks Off 20th Annual Cybersecurity Awareness Month
National Cybersecurity Alliance Kicks Off 20th Annual Cybersecurity Awareness Month

Press
Beta News: Gen Z twice as likely to think cybersecurity isn't worth the effort
Press
Cyberwire: CyberWire Daily Episode 1919

Press
Fortune: Nearly half of Americans have had personal data exposed by cyber criminals. The director of the National Cybersecurity Alliance says 4 behaviors can help reduce the threat

Press
STUDY: 37% Intimidated, 39% Frustrated with Online Security Highlighting Digital Anxiety
STUDY: 37% Intimidated, 39% Frustrated with Online Security Highlighting Digital Anxiety

Press
USA Today: What Is This Charge On My Credit Card?

Press
The Blast: Cybersecurity Expert Shares Information About Cyberattacks Like MGM's

Press
SC Magazine: MGM Resorts ransomware recovery efforts nearly complete

Press
AP News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks

Press
Casino.org: MGM v. Caesars - Cybersecurity Expert Rates Hacking Responses

Press
Las Vegas Sun: Cybersecurity demands that businesses constantly evolve Las Vegas Sun

Press
Silicon Angle: Services at MGM Resorts restored following ransomware attack

Press
Technical.ly: DC Money Moves - Following its SPAC merger and subsequent lawsuit, IronNet is looking at bankruptcy

Press
ABC News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks

Press
NBC Las Vegas: Several systems and functions remain down as MGM says casinos, hotels 'operating normally'

Press
Thrillist: What to Do if a Data Breach Exposes Your Personal Info While Traveling

Press
Hospitality Technology: MGM Data Breach Linked to Vishing

Press
The Record Media: Craigslist founder donates $200,000 to HBCU cybersecurity initiative

Press
Dark Reading: National Cybersecurity Alliance Receives 200K Grant From Craig Newmark Philanthropies for HBCU Cybersecurity Program

Press
National Cybersecurity Alliance Receives Generous 200K Grant from Craig Newmark Philanthropies for HBCU Cybersecurity Program
National Cybersecurity Alliance Receives Generous 200K Grant from Craig Newmark Philanthropies for HBCU Cybersecurity Program

Press
Government Technology: 2023 Cybersecurity Awareness Month Appeal - Make Online Security Easier

Press
Indianapolis Recorder: White House launches an education initiative to diversify the cyber industry
Press
Global News: Have an old Gmail account? Google says inactive ones could be deleted

Press
National Cybersecurity Alliance Kicks-Off 2nd Year of “See Yourself In Cyber” HBCU Career Program
National Cybersecurity Alliance Kicks-Off 2nd Year of “See Yourself In Cyber” HBCU Career Program

Press
Tampa Bay Times: Florida Patients Among Victims of Spate of Data Hacking
Press
Raconteur: Why Gen Z's Lack of Literacy is a Serious Business Risk

Press
BizTech: Elevate Your Ransomware Defenses with a Post Incident Review

Press
Insurance Journal: The Industry Shouldn't Compete on Cybersecurity

Press
BizTech: What Is Active Directory Monitoring and Why Is AD a Target for Hackers?

Press
Erie News Now: Keeping the LGBT+ Community Safe Online

Press
Engadget: The best password managers for 2023

Press
Dark Reading: Volt Typhoon' Breaks Fresh Ground for China-Backed Cyber Campaigns

Press
IT Brew: Asked and answered: 'What is the best defense against polymorphic malware?'

Press
National Geographic: Practical tips for protecting your data while traveling

Press
BizTech: How to Measure Your Team’s Email Security Savviness

Press
The VIP Home Podcast: Top Internet Safety Tips to Keep Your Info Secure at Home

Press
Infosecurity Magazine: Characterless Security Training Fails to Change User Behavior

Press
National Cybersecurity Alliance launches HBCU Scholarship Program

Press
Technical.ly: Two nonprofits teamed up to offer HBCU tech students $20K in scholarships
Press
National Cybersecurity Alliance Partners with One In Tech Foundation to Launch HBCU Scholarship Program
National Cybersecurity Alliance Partners with One In Tech Foundation to Launch HBCU Scholarship Program

Press
Cybersecurity Dive: Women in cybersecurity still fight for inclusion despite the talent shortage
Press
CPO Magazine: Notorious Genesis Dark Web Market Taken Offline by Law Enforcement

Press
Washington Post: Watch out for online scams and vulnerabilities this tax season
Press
National Cybersecurity Alliance Joins RSA Conference with a Discussion on Engagement through Entertainment
National Cybersecurity Alliance Joins RSA Conference with a Discussion on Engagement through Entertainment
Press
MAKE USE OF: 5 Kinds of Spyware You Need to Know About

Press
Boston Globe: New details on LastPass breach mean it’s time for a new password manager

Press
Sahan Journal: Minneapolis Public Schools acknowledges ‘threat actors’ could have accessed district data. Here’s what you need to know to protect yourself

Press
The White House Readout: Office of National Cyber Director Hosts Roundtable on “The State of Cybersecurity in the Black Community”

Press
To the Point Podcast: So Many Cyber Scams - with Names Like Pig Butchering?! With Jennifer Cook

Press
VentureBeat: NCA executive director shares top cybersecurity risks in 2023

Press
Help Net Security: Helping users and organizations build an instinctive data privacy habit

Press
PCMag: Why Tech Companies Are Looking to HBCUs to Expand the Cybersecurity Workforce

Press
Tom's Guide: Don’t get burned this Valentine’s Day — these are the scams to look out forTom's Guide:

Press
Washington Post: Romance scammers could cause unhappy Valentine’s Day

Press
Washington Post: The State of the Union was light on cybersecurity
Press
IT Brew: Three ways to sell a privacy program to an exec who’s not listening

Press
CNBC: How to protect yourself from tax fraud and scams, according to cybersecurity experts

Press
CBS17: Are you a T-Mobile customer? Here’s how to protect yourself against data breaches

Press
CyberWire: DragonSpark hits East Asia. ProxyNotShell in the wild. Privacy investment. IoT supply chain threat.

Press
TechRepublic: Data Privacy Week 2023 - Virtual events and webinars to attend

Press
Channel Futures: 2023 Cybersecurity Outlook - Newer Targets, Tighter Budgets

Press
VentureBeat: T-Mobile data breach shows API security can’t be ignored
Press
National Cybersecurity Alliance Announces Program for 2023 Data Privacy Week Campaign
National Cybersecurity Alliance Announces Program for 2023 Data Privacy Week Campaign
Press
T-Mobile January 2023 Data Breach Announcement: What You Should Do
T-Mobile January 2023 Data Breach Announcement: What You Should Do

Press
Reflections on Winter 2023 Convene
Reflections on Winter 2023 Convene

Press
IT Brew: Despite hacks, password managers are still an important SaaS security measure

Press
SDxCentral: TACKLING TECH’S TALENT SHORTAGE IN 2022

Press
PCMag: 2023 Could Be a Security Nightmare. Here’s Why

Press
Security Intelligence: How to Embed Gen Z in Your Organization’s Security Culture

Press
Cyberwire: Updates on the cyber phases of a hybrid war

Press
Cybernews: How to avoid hacking hangover at the airport this holiday season

Press
AARP: 4 Tips for Talking to Your Kids and Grandkids about Fraud

Press
GitHub repojacking attack: 10 lessons for software teams

Press
Law360: Small Firms Need Cyber Protection As Much As Large Ones

Press
SpiceWorks: A Defense Playbook for Diffusing CCTV Cybersecurity Threats

Press
Cyberwire: CISA releases voluntary CPGs. Trojans and scanners. Cyber venture investing, and some insights into corporate culture. "Opportunistic" cyberops in a hybrid war.

Press
AiThority: Predictions Series 2022 - Interview with Lisa Plaggemier, Executive Director at National Cybersecurity Alliance

Press
Plex breach exposes usernames, emails, and encrypted passwords

Press
Cheddar: U.S. Cable Wake Up with Cheddar

Press
CNBC: U.S. Cable Squawk on the street
Press
The Verge: How to rescue your hacked account: Facebook, Instagram, Snapchat, and more

Press
BizTech: How Nonprofits Can Protect Their Donor Data in the Cloud
Press
Channel Features: Pro-Russian Hacktivist Groups Take Down Numerous U.S. Airport Websites

Press
National Cybersecurity Alliance Kicks Off 19th Annual Cybersecurity Awareness Month
National Cybersecurity Alliance Kicks Off 19th Annual Cybersecurity Awareness Month

Press
Beta News: A third of people fall victim to cyberattacks despite training

Press
STUDY: More than One-Third of Tech Users Fell Victim to Phishing Despite Access to Training Geared Towards Identifying Attacks
STUDY: More than One-Third of Tech Users Fell Victim to Phishing Despite Access to Training Geared Towards Identifying Attacks

Press
CRN: Experts At Amazon, Google, Dell - Cybersecurity Begins At Home
Press
SecureWorld: Cybersecurity Awareness Month Focuses on People

Press
Infosecurity Magazine: Initiative Aims to Encourage Diverse Talent into Cyber

Press
SDX Central: Daily Roundup - Ericsson Releases Power-Efficient 5G Radio

Press
SDX Central: National Cybersecurity Alliance Launches Outreach, Mentorship Program

Press
The Record: CISA, Dell and more partner for HBCU cybersecurity program

Press
SC Magazine: National Cybersecurity Alliance launches HBCU career training program

Press
National Cybersecurity Alliance Launches HBCU Career Program
National Cybersecurity Alliance Launches HBCU Career Program
Press
Channel Futures: Data Breach Hits Media Streaming Platform
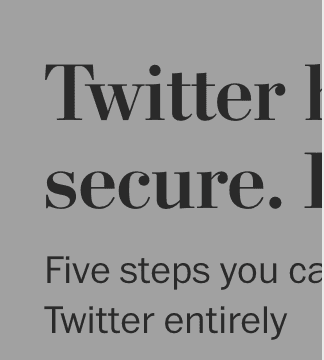
Press
Washington Post: Twitter has issues keeping your data secure. Here’s what you can do.

Press
NCA Partners with Amazon on PSA Campaign to Educate Consumers about Online Cyber Threats and Best Practices to Protect Themselves
NCA Partners with Amazon on PSA Campaign to Educate Consumers about Online Cyber Threats and Best Practices to Protect Themselves

Press
AP Archive: Apple issues security warning for iPhones, devices

Press
Dark Reading: Patch Now - 2 Apple Zero-Days Exploited in Wild

Press
Washington Post: Mandatory password updates are passe

Press
Forbes: Coalition Of Cybersecurity Leaders Launch Open Cybersecurity Schema Framework (OCSF)

Press
IT Brew: Lazarus attackers mimic job recruiters

Press
Morning Brew: Five remote-onboarding tips for IT pros

Press
USA Today: Helping small businesses and rural communities thwart cyberattacks

Press
CPO Magazine: Game Publisher Bandai Namco Confirms a Suspected BlackCat Ransomware Attack

Press
Washington Post: Howard University cancels online, hybrid classes as it investigates alleged ransomware attack

Press
CyberWire: New hack de-anonymizes website users

Press
Silicon Angle: Japanese video game publisher Bandai Namco targeted in ransomware attack

Press
Street Fight Magazine: Retailers Prepare for Increased Cyber Attacks During Prime Day
Press
The National Cybersecurity Alliance Named to CSO50
The National Cybersecurity Alliance Named to CSO50
Press
National Cybersecurity Alliance Named to CSO50
National Cybersecurity Alliance Named to CSO50

Press
Medscape: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks

Press
Get Involved In Identity Management Day
Get Involved In Identity Management Day

Press
Reader's Digest: How to Spot a Fake QR Code and Avoid Getting Scammed
Press
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy
Press
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity
Press
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity

Press
The Register: Biden signs cybercrime tracking bill into law
Press
National Cyber Security Alliance Statement Regarding Incorrect Small Business Statistic
National Cyber Security Alliance Statement Regarding Incorrect Small Business Statistic

Press
Forbes: Biden Signs Bill To Create Cybercrime Reporting System
Press
News Radio 1120 KMOX: Stop writing down passwords

Press
CSO: Meta, Apple emergency data request scam holds lessons for CISOs

Press
Technical.ly: 5 reasons to consider a cybersecurity career in 2022
Press
CSO: U.S. State Department unveils new Bureau of Cyberspace and Digital Policy

Press
Channel Futures: The Gately Report - Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022

Press
Channel Futures: Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022

Press
Channel Futures: FCC Says Kaspersky Software Poses National Security Threat

Press
The Cyberwire: Russia's hybrid war with Ukraine: strategy, norms, and alliances
Press
Washington Post: Want to avoid a cyberattack? Stop ignoring those pesky software updates.
Press
MarketWatch: The prospect of more Russian cyberattacks seems increasingly likely. What can you do to protect yourself? Quite a lot, it turns out.

Press
CSO: NIST seeks information on updating its Cybersecurity Framework

Press
Washington Post: The Online Security Reset Guide: Keeping you safe from scammers, hackers and digital threats

Press
Gov Info Security: Ukrainian Government Prepared to Wipe Servers

Press
American Banker: Ransomware attacks are rising, payment security consortium warns

Press
Techspective: Lisa Plaggemier Discusses Cybersecurity at the Winter Olympics

Press
Well+Good: How To Spot a Scammer and Protect Yourself From Them, According to a Relationship Therapist and Cyber Security Expert

Press
AdWeek: How QR Codes Made Waves at the 2022 Super Bowl

Press
Media Post: 83.4 Million U.S. Smartphone Users Will Scan QR Codes This Year

Press
PC Magazine: Coinbase's Mystery QR Code Super Bowl Ad Is a Security Nightmare

Press
Gov Info Security: US SEC Proposes 48-Hour Incident Reporting Requirement
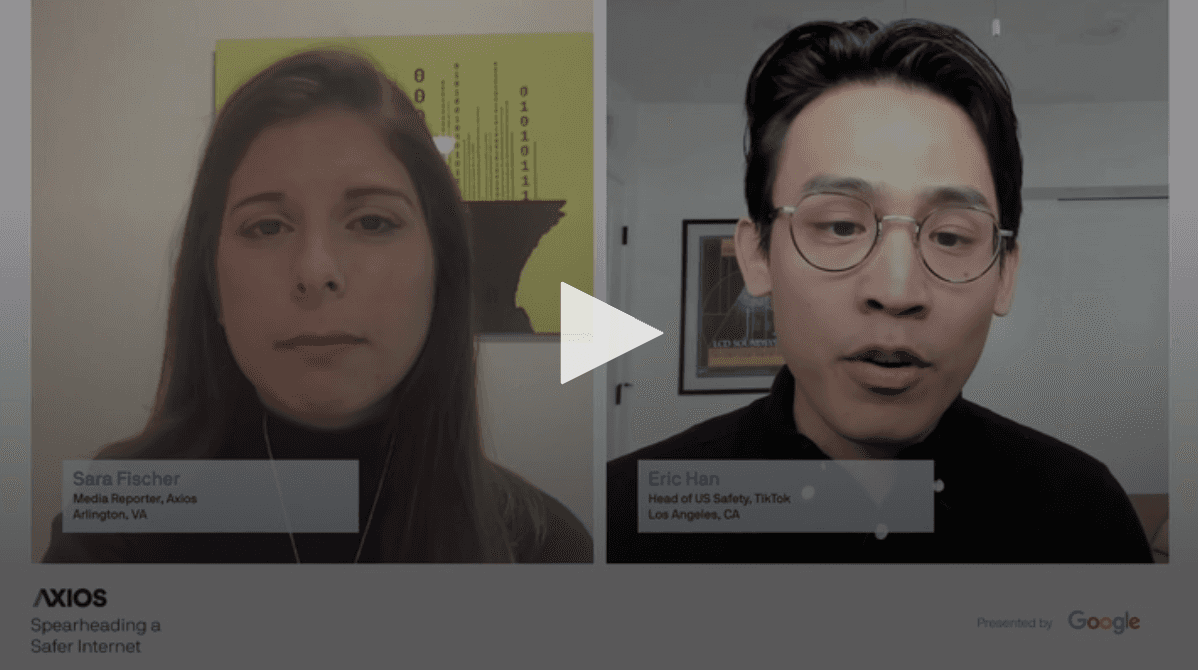
Press
Axios: Watch A conversation on internet safety in the modern digital era

Press
Broad and Breakfast: Companies Should Mandate Two-Factor Authentication, Says Head of National Cybersecurity Alliance

Press
Digital Anarchist: Data Privacy Week – Lisa Plaggemier, National Cyber Security Alliance

Press
Inside the Games: Lisa Plaggemier - After Pyeongchang 2018 cyberattack, will Beijing 2022 be safe and secure?

Press
Database Trends: Data Privacy Day 2022 - Industry Leaders Reflect on the Current State of Data Security

Press
SD Times: The NCSA expands annual Data Privacy Day into Data Privacy Week

Press
Tech and Science Daily Podcast: Samsung's new Galaxy S22 - What to expect

Press
Auto Remarketing: KAR licenses privacy & security training program to NAAA-member auctions
Press
Fox News: It's Data Privacy Week—here are some tips on staying safe while online

Press
KMOX: Expert - Protecting your data can make a 'massive dent' in cybercrime

Press
Washington Post: Cyber fears mount amid prospect of Russian invasion of Ukraine

Press
FOX NEWS: Online security and privacy is easy, not complicated
Press
National Cybersecurity Alliance Announces Program for Data Privacy Week
National Cybersecurity Alliance Announces Program for Data Privacy Week
Press
SECURITY BOULEVARD: FCC Proposes Stricter Regulations for Data Breach Disclosure
Press
SECURITY BOULEVARD: Why 2022 Should be a Year of Cybersecurity Optimism
Press
Why 2022 Is the Year of the Password Manager

Press
CHANNEL FUTURES: 2022 Cybersecurity Predictions: Even More Reasonware, But Reason for Optimism

Press
CSO: Security leaders on how to cope with stress of Log4j

Press
Dark Reading: Meta Files Federal Lawsuit Against Phishing Operators

Press
Channel Futures: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks

Press
Gov Info Security: US, Allies to Tighten Export Controls on Cyber Tools
Press
Politico: Washington’s cybersecurity wish list for 2022

Press
Spiceworks: Tackling the Cybersecurity Talent Gap: 4 Tips for Employers

Press
The Stevie® Awards: Honoring Excellence in Business Worldwide
The Stevie® Awards: Honoring Excellence in Business Worldwide

Press
KKTV: Don’t let grinches steal Christmas! How to stay safe when holiday shopping

Press
Security Boulevard: US, EU Join Paris Call for Cybersecurity

Press
Bank Info Security: VP Kamala Harris: US Will Join 80-Nation Cybersecurity Pact

Press
USA Today: After 7 million impacted in Robinhood data breach, experts offer some tips for amateur investors

Press
Fast Company Robinhood data breach - Here’s what stock traders who use the platform need to know

Press
Gov Info Security: Infrastructure Bill Features $1.9 Billion in Cyber Funding

Press
Ping: How to Be Cyber Smart this Cybersecurity Awareness Month

Press
NBC: How to Keep Children Safe From Online Scams, Identity Theft

Press
State Scoop: It’s October. Are you aware of cybersecurity yet?
Press
RBR: The InFOCUS Podcast - National Cybersecurity Alliance

Press
EdTech: Next-Generation Firewall and IPSs Offer Proactive Protection for Higher Ed Networks

Press
Light Reading: Sinclair hit by ransomware attack

Press
NBC: Authorities See Rise in Ransomware Attacks, Urge Businesses to Prioritize Cybersecurity

Press
Bank Info Security: US Agencies to Water Facilities - You May Be Next Target
Press
Best Practices for People and Enterprise to #StaySafeOnline

Press
Gov Info Security: CISA to Access Agencies' Endpoints, Help Enhance Security
Press
NBC: Top 5 Things You Should Be Doing to Keep Your Information Safe Online

Press
Security Boulevard: Public’s Knowledge of Cybersecurity Best Practices Sorely Lacking

Press
Beta News: Highlighting the cybersecurity generation gap

Press
NBC: #BeCyberSmart - The Rise of Online Scams

Press
Venture Beat: Cyberattacks are getting worse, but most people aren’t taking basic security steps

Press
Venture Beat: It’s Cybersecurity Awareness Month. Does your business have a viable plan yet?

Press
STUDY: Millennials and Gen Z Say They are Bigger Victims of Cybercrime
STUDY: Millennials and Gen Z Say They are Bigger Victims of Cybercrime
Press
National Cyber Security Alliance Kicks Off 18th Annual Cybersecurity Awareness Month
National Cyber Security Alliance Kicks Off 18th Annual Cybersecurity Awareness Month

Press
Forensics: CYBERSECURITY AWARENESS MONTH 2021 - AN EXPERT’S ADVOCACY GUIDE

Press
CBS: Apple says its security flaw was fixed. Cyber analysts warn zero-click threats will persist.

Press
The Learning Counsel: How To Safeguard Schools Against Cyber Attacks this School Year

Press
Venture Beat: Why cyber scare tactics have missed the mark

Press
Healthcare IT News: FBI, CISA warn: Hackers won't take a vacation

Press
The Cyberwire: WhatsApp patches bug. Twitter updates its features to promote “social privacy.” Labor Day threats to data privacy.
Press
Channel Futures: Hackers Again Setting Sights on Microsoft Exchange Vulnerabilities

Press
TDWI: How Organizations Can Stay Protected Online
Press
Bank Info Security: World Bank Launches Global Cybersecurity Fund

Press
Techinal.ly: Resource Roundup: Level up in cyber, IT and entrepreneurship with these 4 DC-area programs

Press
Cyber Magazine: National Cyber Security Alliance to launch new resource bank

Press
Washington Post: The Cybersecurity 202: There was another massive data breach. People will probably forget it in a week.
Press
SC Magazine: NCSA creates cyber career resource library to educate our future infosec workforce

Press
Security Magazine: National Cyber Security Alliance launches new cyber initiative

Press
National Cyber Security Alliance Unveils Cybersecurity Education and Career Resource Library
National Cyber Security Alliance Unveils Cybersecurity Education and Career Resource Library

Press
Cybersecurity Dive: How the $1.2 trillion infrastructure bill invests in cyber

Press
Gov Info Security: OMB Spells Out Agencies' Cybersecurity Timelines

Press
CIO Dive: Preparedness, checklists, leadership buy-in - How to build a rapid IT response
Press
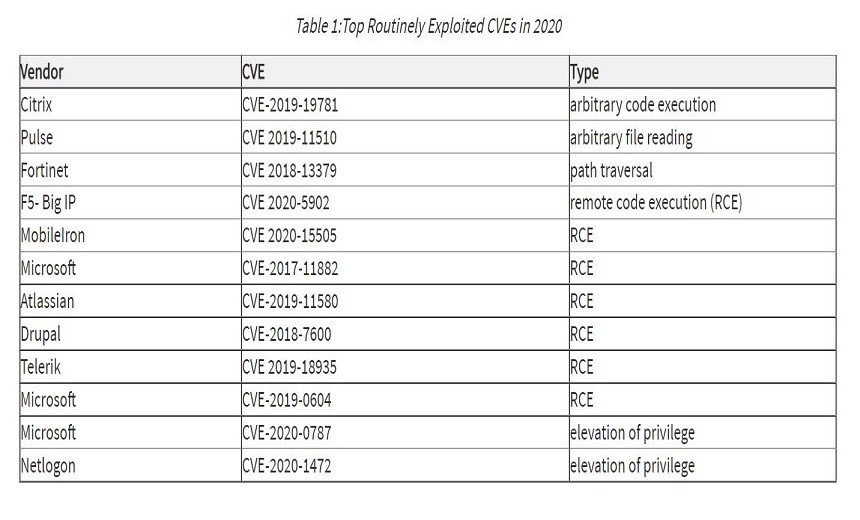
Gov Info Security: Patching Woes: Most Frequently Exploited CVEs Listed

Press
What the Dev? Cybersecurity and the Tokyo Olympics - Episode 113

Press
Fox: Tokyo Olympics could be threatened by cyberattack, FBI warns

Press
Channel Futures: Tokyo Olympics Contending with Cyber Threats, FBI Warns of More Coming

Press
Threat Post: Indictments, Attribution Unlikely to Deter Chinese Hacking, Researchers Say
Press
Auto Remarketing: National Cyber Security Alliance on trends in automotive
Press
National Cyber Security Alliance Announces Leadership Transition
National Cyber Security Alliance Announces Leadership Transition
Press
Law 360: Kaseya Ransomware Hit Casts Wide Net Of Potential Liability

Press
Bloomberg: Kaseya Software Hack Highlights Small Business Security Squeeze
Press
Washington Post: The Cybersecurity 202: The Kaseya attack is a revolution in sophistication for ransomware hackers

Press
Auto News: Ransomware attacks could crimp industry’s recovery from pandemic, report says

Press
Healthcare Info Security: Battling Ongoing COVID-19-Themed Attacks and Scams

Press
Digital Anarchist: Cybersecurity Safety Review Board – Kelvin Coleman, NCSA

Press
WSJ: Hackers Stole $650,000 From Nonprofit and Got Away, Showing Limits to Law Enforcement’s Reach

Press
NBC: Who's in charge here? Colonial Pipeline hack exposes huge holes in U.S. cyber defenses, say experts

Press
Channel Futures: Significant Ramifications

Press
Ed Tech: To Improve Higher Ed Data Security, Address These Risks in Research Projects

Press
Endpoint: Why We Still Need World Password Day

Press
Health IT Security: Google Sued, Lawsuit Claims COVID-19 Contact Tracing Tool Exposes Data

Press
Associations Now: Spring Clean Your Digital Files

Press
Hacked.com: Why Every Business Should Train Employees to Spot Phishing Emails
Press
TechTarget: SolarWinds puts national cybersecurity strategy on display

Press
Hacked.com: The Top 5 Reasons Hackers Might Target Your Small Business

Press
Martech Series: Beyond Identity Integration With Auth0 Enables Completely Passwordless Authentication

Press
SC Magazine: On first-ever Identity Management Day, experts detail steps to a better IAM program

Press
Dark Reading: Biden Nominates Former NSA Officials for Top Cybersecurity Roles
Press
WSJ: Biden Administration Announces National Cyber, CISA Director Nominations

Press
Accounting Today: IRS and COVID vaccine email scams proliferating this tax season

Press
Healthcare IT News: How cybercriminals exploit COVID-19, and how to protect against them

Press
Security Magazine: 5 minutes with Kelvin Coleman - Remote learning and data privacy issues

Press
Gov Info Security: Exchange Hacks: How Will the Biden Administration Respond?

Press
Above the Law: Keeping Your Data Safe In The Remote Work Era

Press
The Cyberwire: Patching, with special attention to Hafnium and the rest. Responding to the SolarWinds incident. Hactivists don’t like cameras. Dragnet in the Low Countries.
Press
Health Leaders Media: NCSA ON CYBERSECURITY: 'UPDATE, UPDATE, UPDATE'

Press
MedCity News: When it comes to healthcare cybersecurity, the best defense is also the most simple

Press
Washington Post: The Cybersecurity 202: Scammers are already targeting the next round of coronavirus relief checks

Press
Healthcare Info Security: Fraudsters Devise More COVID-19 Vaccine Schemes

Press
CIO Dive: Legacy tech, privacy and security issues bog down healthcare innovation

Press
Identity Defined Security Alliance Partners with National Cyber Security Alliance to Launch First-Ever ‘Identity Management Day’ April 13, 2021
Identity Defined Security Alliance Partners with National Cyber Security Alliance to Launch First-Ever ‘Identity Management Day’ April 13, 2021

Press
CNET: Apple AirTags: How to Protect Yourself From Being Tracked

Press
FedTech Magazine: The Importance of Supply Chain Risk Management in Government

Press
NBC: Fraud Investigations Holding Up Unemployment Payments

Press
WSJ: U.S. Water Supply Has Few Protections Against Hacking

Press
Digital Anarchist: Kelvin Coleman – TechStrong TV

Press
HealthTech Magazine: How to Keep Telehealth Secure

Press
SDX Central: Is Biden’s $10B Enough to Make US Cybersecurity Great Again?

Press
Datanami: Data Privacy in the Crosshairs
Press
SC Magazine: Speed of White House cyber appointments should make CISOs ‘a bit more confident’

Press
National Cyber Security Alliance Kicks off Data Privacy Day This Week to Raise Awareness for Responsible Data Privacy Practices
National Cyber Security Alliance Kicks off Data Privacy Day This Week to Raise Awareness for Responsible Data Privacy Practices

Press
Protocol: Why an ‘internet blackout’ probably isn’t coming on inauguration day

Press
SC Magazine: Free cyber career training coursework emerges as a perk in tough times

Press
Digital Anarchist: TechStrong TV – January 14, 2021
Press
Security Boulevard: Data Privacy Day - Understanding COVID-19’s Impact

Press
GCN: IT cleanup at U.S. Capitol presents massive challenge
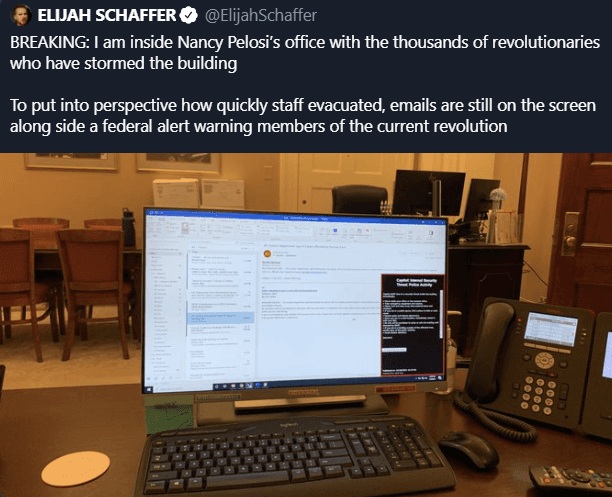
Press
Security Week: Experts Weigh In on Cybersecurity Risks of Capitol-Like Attacks
Press
TidBITS: Cybersecurity Ramifications of the 2021 Storming of the United States Capitol

Press
Wired: Post-Riot, the Capitol Hill IT Staff Faces a Security Mess

Press
Channel Futures: US Capitol Rioters Pose Cybersecurity Threat Due to Device Access, Theft

Press
Data Center Knowledge: What Data Center IT Security Pros Must Know About the SolarWinds Vulnerability

Press
In wake of SolarWinds hack, here are the critical responses required of all businesses

Press
Tech Targets: Cybersecurity employee training: How to build a solid plan

Press
The Hill: Scammers step up efforts to target older Americans during pandemic
Press
Digital Trends: The digital switch that blocks all websites from selling your personal data

Press
Faith, Health & Home Podcast: How to Keep Your Family Safe Online | Kelvin Coleman, Exec. Director, Nat'l Cyber Security Alliance

Press
Bank Info Security: APT Groups Target Firms Working on COVID-19 Vaccines

Press
Forbes: 6 Cybersecurity Tips When You Work From Home

Press
Barracuda: Age plays a role in end-user security training

Press
Dark Reading: 7 Online Shopping Tips for the Holidays

Press
The Daily Swig: Europol campaign urges e-commerce retailers to #SellSafe this Black Friday

Press
Healthcare IT News: Hospitals said to tighten email security in response to CEO spear phishing attempts

Press
Dark Reading: Online Users Feel Safe, But Risky Behavior Abounds

Press
Healthcare IT News: NCSA Confidence in security of connected devices often misplaced

Press
The Cyberwire: CISA says no evidence of successful foreign election hacks. QBot’s voting-themed malspam. RegretLocker arriving.

Press
24x7 Magazine: 81% of Americans Highly Confident Connected Devices Secure Despite Overlooking Basic Security Hygiene

Press
Beta News: Consumers overconfident of their connected device security
Press
Infosecurity Magazine: Americans Confident in IoT Device Security
Press
SC Magazine: New data shows just how badly home users overestimate IoT security
Press
Dot Med: Five minutes in healthcare - featuring Kelvin Coleman

Press
Security Boulevard: U.S. Health Care Under Attack
Press
Healthcare IT Today: Government Agencies Warn of Imminent Cybercrime Threat from Ransomware Targeted at Hospitals

Press
The Cyberwire: Ransomware versus patient medical data. Patching and updating. A new loader in town.

Press
Health Leaders Media: CISA, FBI, HHS WARN HOSPITALS OF 'INCREASED AND IMMINENT' CYBERCRIME THREAT

Press
Health IT Answers: The Future of Connected Devices

Press
Health IT Security: Phishing Campaigns Mimic Microsoft Teams, HHS COVID-19 Vaccine Tracker

Press
Healthcare Info Security: COVID-19 Growing Cybersecurity Risks

Press
Health IT Security: Rapid Threat Evolution Spurs Crucial Healthcare Cybersecurity Needs

Press
Spiceworks: How SMBs Can Stay on Top of the Evolving Threat Landscape

Press
Forbes: Communicate With Confidence Through A Cyber Crisis

Press
Healthcare Info Security: Cybersecurity Advice for the COVID-19 Era

Press
Dark Reading:A 7-Step Cybersecurity Plan for Healthcare Organizations

Press
ABC: Computer security expert shares tips on staying safe amid surge in cybercrime
Press
Tech Republic: 3 ways criminals use artificial intelligence in cybersecurity attacks

Press
TechTarget: Healthcare cybersecurity needs a dose of threat modeling

Press
Infosecurity Magazine: #NCSAM: Is Connected Ever Going to be Protected?
Press
The Cyberwire: Cyber conflict in the Caucasus. Zerologon exploited in the wild. Emotet rising. Silicon Valley’s Gilded Age?

Press
Cybersecurity Awareness Month Around The World | Bangladesh, Canada, And Central/South America | With Kazi Mustafiz, Christine Menard, and Gabriela Montes de Oca Fehr

Press
Nextgov: CISA Leader Puts Health Sector Project on the Level of Election Security Initiative
Press
Washington Post: The Cybersecurity 202: Americans are as insecure as ever on the 17th annual Cybersecurity Awareness month

Press
It Is Cybersecurity Awareness Month | A Chat With NCSA And CISA To Learn What Is New This Year | With Kelvin Coleman, Brandon Wales, And Lisa Plaggemier

Press
Data Breach Today: Incident Response: Taking a More Deliberate Approach

Press
Dark Reading: 7 Summer Travel Security Tips

Press
Security Week: Industry Reactions to Twitter Hack - Feedback Friday
Press
USA Today: 'Tweet-tastrophe'? It could have been. Twitter hack reveals national security threat before election

Press
IT Ops Times: Twitter attack highlights the need for security awareness training

Press
Threat Post: Twitter Confirms it Was Hacked in an Unprecedented Cryptocurrency Scam
Press
Bank Info Security: Several Prominent Twitter Accounts Hijacked in Cryptocurrency Scam

Press
SD Times: Contact tracing apps need to establish trust to be effective
Press
Politico: CISA funding bill, EAC hearing on 2020 primary woes on slate this week

Press
Channel Futures: Tech Startups Hemorrhaging Jobs During Pandemic

Press
Politico: Early Covid-19 tracking apps easy prey for hackers, and it might get worse before it gets better

Press
Tech Republic: Be prepared: Why you need an incident response policy

Press
CNBC: CLEAR is poised to lead the multibillion-dollar biometric screening race for the coronavirus
Press
ABC: Criminals are pretending to be the government, World Health Organization; here's what to watch out for

Press
Health IT Security: COVID-19 Contact Tracing Apps Spotlight Privacy, Security Rights
Press
NCSA Announces Partnership with National White Collar Crime Center
NCSA Announces Partnership with National White Collar Crime Center

Press
Digital Trends: Contact-tracing apps may seem like the coronavirus solution. They’re not

Press
CNBC: Utah has rejected the Apple-Google approach to tracing coronavirus, and is using an app made by a social media start-up instead

Press
Dark Reading: 7 Ways Parents Can Better Protect Their Online-Gamer Offspring

Press
Built In: How Healthcare Cybersecurity Is Affected by the Coronavirus Pandemic
Press
National Cyber Security Alliance Encourages Vigilance Against Coronavirus Scams, Best Cybersecurity Practices for Remote Workers
National Cyber Security Alliance Encourages Vigilance Against Coronavirus Scams, Best Cybersecurity Practices for Remote Workers
Press
National Cyber Security Alliance Supports RSA® Conference Theme “The Human Element” with Expert Panel on Cybersecurity and Changing Human Behavior
National Cyber Security Alliance Supports RSA® Conference Theme “The Human Element” with Expert Panel on Cybersecurity and Changing Human Behavior
Press
On January 28, Data Privacy Day Encourages Consumers to “Own Their Privacy” and Businesses to Improve Their Data Privacy Practices
On January 28, Data Privacy Day Encourages Consumers to “Own Their Privacy” and Businesses to Improve Their Data Privacy Practices
Press
Free and Fun Security Awareness Videos: Brought to you by Adobe, the National Cybersecurity Alliance, and Speechless, Inc.
Free and Fun Security Awareness Videos: Brought to you by Adobe, the National Cybersecurity Alliance, and Speechless, Inc.
Press
National Cyber Security Alliance Hosts Online Safety Workshops for Consumers and Small Businesses in Indianapolis
National Cyber Security Alliance Hosts Online Safety Workshops for Consumers and Small Businesses in Indianapolis
Press
16th Annual National Cybersecurity Awareness Month Begins Today
16th Annual National Cybersecurity Awareness Month Begins Today
Press
Countdown to National Cybersecurity Awareness Month 2019 Begins
Countdown to National Cybersecurity Awareness Month 2019 Begins
Press
The National Cyber Security Alliance and ITSPmagazine Announce Partnership in Support of CyberSecure My Business™
The National Cyber Security Alliance and ITSPmagazine Announce Partnership in Support of CyberSecure My Business™
Press
The National Cyber Security Alliance and the Better Business Bureau Recommend Top Online “Take-Action Tips” to Help Keep You Safe and Secure
The National Cyber Security Alliance and the Better Business Bureau Recommend Top Online “Take-Action Tips” to Help Keep You Safe and Secure
Press
The National Cyber Security Alliance Welcomes Three Prominent Industry Leaders to Board of Directors
The National Cyber Security Alliance Welcomes Three Prominent Industry Leaders to Board of Directors
Press
The National Cyber Security Alliance Welcomes New Board Members
The National Cyber Security Alliance Welcomes New Board Members

Press
National Cyber Security Alliance Reminds Organizations of All Sizes that “Privacy is Good for Business”
National Cyber Security Alliance Reminds Organizations of All Sizes that “Privacy is Good for Business”
Press
Data Privacy Day 2019 Reminds Businesses and Consumers About the Value of Personal Data and the Need to Protect It
Data Privacy Day 2019 Reminds Businesses and Consumers About the Value of Personal Data and the Need to Protect It

Press
Make a Digital New Year’s Resolution: Keep Your Computer Systems and Software Up to Date
Make a Digital New Year’s Resolution: Keep Your Computer Systems and Software Up to Date
Press
National Cyber Security Alliance Responds to Marriott Cybersecurity Incident
National Cyber Security Alliance Responds to Marriott Cybersecurity Incident
Press
The National Cyber Security Alliance Appoints Kelvin Coleman as Executive Director
The National Cyber Security Alliance Appoints Kelvin Coleman as Executive Director

Press
Cheers to Safe Cybershopping!
Cheers to Safe Cybershopping!
Press
Intel and National Cyber Security Alliance Team Up to Remind Cool Cats Nationwide to Protect Their Nine Digital Lives and #UpdateMeow
Intel and National Cyber Security Alliance Team Up to Remind Cool Cats Nationwide to Protect Their Nine Digital Lives and #UpdateMeow
Press
The National Cyber Security Alliance Announces Winners for the First-Ever National Cyber Security Alliance Awards
The National Cyber Security Alliance Announces Winners for the First-Ever National Cyber Security Alliance Awards
Press
Safeguarding the Nation’s Infrastructure Needs to Be “Our Shared Responsibility”
Safeguarding the Nation’s Infrastructure Needs to Be “Our Shared Responsibility”
Press
It’s Everyone’s Job to Ensure Online Safety at Work
It’s Everyone’s Job to Ensure Online Safety at Work
Press
The Severe Shortage of Cybersecurity Professionals is a Key Risk to Our Nation’s Security
The Severe Shortage of Cybersecurity Professionals is a Key Risk to Our Nation’s Security
Press
Make Your Home a Haven for Online Safety
Make Your Home a Haven for Online Safety

Press
Two Weeks and Counting Until National Cybersecurity Awareness Month Kicks Off on Oct. 1
Two Weeks and Counting Until National Cybersecurity Awareness Month Kicks Off on Oct. 1
Press
Higher Ed Joins Forces with Nonprofit and Business to Promote Cyber Safety on Campus
Higher Ed Joins Forces with Nonprofit and Business to Promote Cyber Safety on Campus

Press
All Systems Go: The 15th Annual National Cybersecurity Awareness Month Launches on October 1
All Systems Go: The 15th Annual National Cybersecurity Awareness Month Launches on October 1
Press
Stay #CyberAware on Mobile Devices during Internet Safety Month and All Year Round
Stay #CyberAware on Mobile Devices during Internet Safety Month and All Year Round

Press
National Cyber Security Alliance Executive Director Russ Schrader Addresses Cyber Challenges Facing Small Businesses at Senate Hearing
National Cyber Security Alliance Executive Director Russ Schrader Addresses Cyber Challenges Facing Small Businesses at Senate Hearing

Press
The National Cyber Security Alliance and Better Business Bureau Encourage “Digital Spring Cleaning” for Everyone
The National Cyber Security Alliance and Better Business Bureau Encourage “Digital Spring Cleaning” for Everyone
Press
NCSA and Nasdaq Cybersecurity Summit Examines How to Better Protect the Expanding Cloud Ecosystem From Security Threats
NCSA and Nasdaq Cybersecurity Summit Examines How to Better Protect the Expanding Cloud Ecosystem From Security Threats

Press
National Cyber Security Alliance Supports RSA® Conference’s Mission to Inspire All Digital Citizens to Take Action and Help Secure the World Against Cyber Threats
National Cyber Security Alliance Supports RSA® Conference’s Mission to Inspire All Digital Citizens to Take Action and Help Secure the World Against Cyber Threats
Press
The National Cyber Security Alliance Appoints Russell Schrader as Interim Executive Director
The National Cyber Security Alliance Appoints Russell Schrader as Interim Executive Director
Press
Data Privacy Day Reminds Everyone About the Value of Their Personal Information and How to Manage Online Privacy
Data Privacy Day Reminds Everyone About the Value of Their Personal Information and How to Manage Online Privacy
Press
New Video Showcases How Financial Institutions Work with Government Agencies to Remediate Phishing Cyber Attack
New Video Showcases How Financial Institutions Work with Government Agencies to Remediate Phishing Cyber Attack

Press
National Cyber Security Awareness Month Highlights Strengthening the Cyber Workforce as a Starting Point to a Safer, More Secure Online Future
National Cyber Security Awareness Month Highlights Strengthening the Cyber Workforce as a Starting Point to a Safer, More Secure Online Future
Press
Second Annual National Cyber Security Alliance Survey Reveals Complex Digital Lives of American Teens and Parents, Highlights Gender Divide
Second Annual National Cyber Security Alliance Survey Reveals Complex Digital Lives of American Teens and Parents, Highlights Gender Divide
Press
National Cyber Security Awareness Month Reminds Everyone That Smart Devices Are Fueled By Our Personal Information
National Cyber Security Awareness Month Reminds Everyone That Smart Devices Are Fueled By Our Personal Information

Press
Organization Leaders and Employees Reminded That “Cybersecurity in the Workplace Is Everyone’s Business” This National Cyber Security Awareness Month
Organization Leaders and Employees Reminded That “Cybersecurity in the Workplace Is Everyone’s Business” This National Cyber Security Awareness Month

Press
National Cyber Security Alliance Statement Following Report on Three Billion Accounts Hacked in 2013 Yahoo Breach
National Cyber Security Alliance Statement Following Report on Three Billion Accounts Hacked in 2013 Yahoo Breach
Press
National Cyber Security Awareness Month Launches With a Call to STOP. THINK. CONNECT.™ Online
National Cyber Security Awareness Month Launches With a Call to STOP. THINK. CONNECT.™ Online
Press
On October 1, Digital Citizens Worldwide Will Be Reminded of Our Shared Global Responsibility to Secure the Internet
On October 1, Digital Citizens Worldwide Will Be Reminded of Our Shared Global Responsibility to Secure the Internet

Press
National Cyber Security Alliance Responds to Equifax Breach
National Cyber Security Alliance Responds to Equifax Breach
Press
The Countdown to National Cyber Security Awareness Month Begins!
The Countdown to National Cyber Security Awareness Month Begins!

Press
SC Magazine’s Women in IT Security: Influencers Honors NCSA Director of Special Projects and Government Affairs Kristin Judge
SC Magazine’s Women in IT Security: Influencers Honors NCSA Director of Special Projects and Government Affairs Kristin Judge
Press
National Cyber Security Alliance Statement on International Cyber Attack
National Cyber Security Alliance Statement on International Cyber Attack
Press
NCSA and Nasdaq Cybersecurity Summit Tackles Cyber-Related “People Problems” in the Workplace
NCSA and Nasdaq Cybersecurity Summit Tackles Cyber-Related “People Problems” in the Workplace

Press
The National Cyber Security Alliance and Thatcher & Company Awarded Two Silver Anvils from PRSA
The National Cyber Security Alliance and Thatcher & Company Awarded Two Silver Anvils from PRSA
Press
NCSA Statement on the Ransomware Attack
NCSA Statement on the Ransomware Attack
Press
National Cyber Security Alliance and Better Business Bureau Remind All Internet Users to Do a Digital Spring Cleaning and Clear Out Cyber Clutter
National Cyber Security Alliance and Better Business Bureau Remind All Internet Users to Do a Digital Spring Cleaning and Clear Out Cyber Clutter
Press
The National Cyber Security Alliance and Nasdaq Host Timely, Enterprise-focused Discussion about Cybersecurity Risk Management and Emerging Threats
The National Cyber Security Alliance and Nasdaq Host Timely, Enterprise-focused Discussion about Cybersecurity Risk Management and Emerging Threats
Press
NCSA Tribute to Howard Schmidt
NCSA Tribute to Howard Schmidt

Press
Data Privacy Day Reminds Organizations That Protecting Customers’ Privacy is Critical to Their Business
Data Privacy Day Reminds Organizations That Protecting Customers’ Privacy is Critical to Their Business
Press
The National Cyber Security Alliance Recommends “Five Digital To Do's” for 2017
The National Cyber Security Alliance Recommends “Five Digital To Do's” for 2017
Press
Response Statement: Mark Zuckerberg’s Hacked Pinterest Account
Response Statement: Mark Zuckerberg’s Hacked Pinterest Account
Press
Industry Leaders from NXP Semiconductors and Salesforce Join the National Cyber Security Alliance’s Board of Directors
Industry Leaders from NXP Semiconductors and Salesforce Join the National Cyber Security Alliance’s Board of Directors

Press
As National Cyber Security Awareness Month Comes to a Close, Focus Shifts to Securing Our Nation’s Critical Infrastructure
As National Cyber Security Awareness Month Comes to a Close, Focus Shifts to Securing Our Nation’s Critical Infrastructure
Press
Continued Growth of the “Internet of Me” Has 88 Percent of Consumers Considering the Risks of Using Connected Devices
Continued Growth of the “Internet of Me” Has 88 Percent of Consumers Considering the Risks of Using Connected Devices
Press
Fight Cybercrime During National Cyber Security Awareness Month: It’s Time to Take Action, Safeguard Devices and Protect Personal Information
Fight Cybercrime During National Cyber Security Awareness Month: It’s Time to Take Action, Safeguard Devices and Protect Personal Information
Press
Businesses of All Sizes Urged to Create Culture of Cybersecurity and Protect Assets This National Cyber Security Awareness Month
Businesses of All Sizes Urged to Create Culture of Cybersecurity and Protect Assets This National Cyber Security Awareness Month
Press
White House and the National Cyber Security Alliance Join Forces to Launch
White House and the National Cyber Security Alliance Join Forces to Launch
Press
National Cyber Security Awareness Month Launches with a Call to Action for All Digital Citizens to STOP. THINK. CONNECT.™
National Cyber Security Awareness Month Launches with a Call to Action for All Digital Citizens to STOP. THINK. CONNECT.™
Press
Fast-Approaching National Cyber Security Awareness Month Reminds All Digital Citizens That Cybersecurity is a Shared Responsibility
Fast-Approaching National Cyber Security Awareness Month Reminds All Digital Citizens That Cybersecurity is a Shared Responsibility
Press
Tips for Securing Frequent Flier Miles
Tips for Securing Frequent Flier Miles
Press
National Cyber Security Alliance Statement Following Reported Massive Data Breach at Yahoo! Inc.
National Cyber Security Alliance Statement Following Reported Massive Data Breach at Yahoo! Inc.

Press
National Cyber Security Awareness Month Is Only A Month Away!
National Cyber Security Awareness Month Is Only A Month Away!
Press
Beware of Ransomware
Beware of Ransomware

Press
Statement following report of massive data breach at major email providers
Statement following report of massive data breach at major email providers
Press
National Cyber Security Alliance Survey Reveals the Complex Digital Lives of American Teens and Parents
National Cyber Security Alliance Survey Reveals the Complex Digital Lives of American Teens and Parents

Press
National Cyber Security Alliance and Better Business Bureau Urge Digital Spring Cleaning for All Internet Users
National Cyber Security Alliance and Better Business Bureau Urge Digital Spring Cleaning for All Internet Users

Press
State Legislators Identify Major Opportunities to Address Cybersecurity Gaps
State Legislators Identify Major Opportunities to Address Cybersecurity Gaps
Press
National Cyber Security Alliance Returns to RSA® Conference with a Mission to Educate and Empower Digital Citizens of All Ages about Cybersecurity and Privacy Awareness
National Cyber Security Alliance Returns to RSA® Conference with a Mission to Educate and Empower Digital Citizens of All Ages about Cybersecurity and Privacy Awareness
Press
National Cyber Security Alliance Announces Expansion of Multi-Factor Authentication-Focused Education
National Cyber Security Alliance Announces Expansion of Multi-Factor Authentication-Focused Education
Press
White House Fact Sheet: Cybersecurity National Action Plan
White House Fact Sheet: Cybersecurity National Action Plan
Press
British Internet Users Concerned About Data Privacy Than Losing Their Income
British Internet Users Concerned About Data Privacy Than Losing Their Income
Press
Cisco Joins the National Cyber Security Alliance’s Board of Directors
Cisco Joins the National Cyber Security Alliance’s Board of Directors
Press
Digital New Year’s Resolutions To Keep Everyone Safer And More Secure Online
Digital New Year’s Resolutions To Keep Everyone Safer And More Secure Online

Press
National Cyber Security Awareness Month Seeks #TalentHack Solutions to Overcome the Cybersecurity Skills Gap
National Cyber Security Awareness Month Seeks #TalentHack Solutions to Overcome the Cybersecurity Skills Gap
Press
As the Internet of Things Grows Exponentially, National Cyber Security Awareness Month Focuses on Securing our Connected Devices and Networks
As the Internet of Things Grows Exponentially, National Cyber Security Awareness Month Focuses on Securing our Connected Devices and Networks
Press
Connected Families And Communities In The Spotlight During National Cyber Security Awareness Month
Connected Families And Communities In The Spotlight During National Cyber Security Awareness Month
Press
ESET and National Cyber Security Alliance Study Reveals Almost 80 Percent of American Homes Feel Cyber Secure Despite Unsecured Digital Doors
ESET and National Cyber Security Alliance Study Reveals Almost 80 Percent of American Homes Feel Cyber Secure Despite Unsecured Digital Doors
Press
Small And Midsized Businesses Learn To Protect Their Digital Assets During National Cyber Security Awareness Month
Small And Midsized Businesses Learn To Protect Their Digital Assets During National Cyber Security Awareness Month
Press
NCSA statement following report of data breach at Experian, Exposing T-Mobile Customer Data
NCSA statement following report of data breach at Experian, Exposing T-Mobile Customer Data
Press
National Cyber Security Awareness Month Kicks Off As Growing Global Coalition Urges Internet Users Everywhere To STOP. THINK. CONNECT.
National Cyber Security Awareness Month Kicks Off As Growing Global Coalition Urges Internet Users Everywhere To STOP. THINK. CONNECT.
Press
As National Cyber Security Awareness Month Approaches, Internet Users Are Reminded Why Being Cyber Smart is Critical to Our Lives
As National Cyber Security Awareness Month Approaches, Internet Users Are Reminded Why Being Cyber Smart is Critical to Our Lives
Press
One-Month Countdown to National Cyber Security Awareness Month Begins
One-Month Countdown to National Cyber Security Awareness Month Begins
Press
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy

Press
Council of Anti-Phishing Japan Launches STOP.THINK.CONNECT. Cybersecurity Awareness Campaign with National Public-Private Coalition
Council of Anti-Phishing Japan Launches STOP.THINK.CONNECT. Cybersecurity Awareness Campaign with National Public-Private Coalition

Press
STOP.THINK.CONNECT.™: Broad Government, Industry and Non-Profit Coalition Unveils First-Ever Coordinated Online Safety Message
STOP.THINK.CONNECT.™: Broad Government, Industry and Non-Profit Coalition Unveils First-Ever Coordinated Online Safety Message

Press
National Cybersecurity Alliance Receives 2025 CSO Award from Foundry’s CSO
National Cybersecurity Alliance Receives 2025 CSO Award from Foundry’s CSO

Press
Newsday: LI's Broadridge, Verint testing new Chinese chatbot DeepSeek for automation, efficiency
Newsday: LI's Broadridge, Verint testing new Chinese chatbot DeepSeek for automation, efficiency

Press
Fox Tampa Bay: Tech experts warn of Valentine's Day romance scams as Meta takes steps to protect users
Fox Tampa Bay: Tech experts warn of Valentine's Day romance scams as Meta takes steps to protect users

Press
ABC Philly: FBI issues warning on romance scams ahead of Valentine's Day
ABC Philly: FBI issues warning on romance scams ahead of Valentine's Day

Press
Kiplinger: Hey Valentine, Beware of Catfishing Romance Scams
Kiplinger: Hey Valentine, Beware of Catfishing Romance Scams

Press
PC Mag: Which AI ChatBot Collects the Least of Your Data?
PC Mag: Which AI ChatBot Collects the Least of Your Data?

Press
Gizmodo: The Knives are Coming Out for DeepSeek AI
Gizmodo: The Knives are Coming Out for DeepSeek AI

Press
Data Privacy Week 2025 Press Release
Data Privacy Week 2025 Press Release

Press
Vanity Fair: Is TikTok Really Worth Saving?
Vanity Fair: Is TikTok Really Worth Saving?

Press
Newsweek: PowerSchool Breach Victim Says Hackers Stole All Student Data
Newsweek: PowerSchool Breach Victim Says Hackers Stole All Student Data

Press
The Huffington Post: LA Fire Donation Scams Are Everywhere. Here's How To Spot Them
The Huffington Post: LA Fire Donation Scams Are Everywhere. Here's How To Spot Them

Press
USA Today: Scammers may be taking advantage of the California wildfires - How to protect yourself
USA Today: Scammers may be taking advantage of the California wildfires - How to protect yourself

Press
The Wall Street Journal: Shun This Basic Cybersecurity Tactic and Become a Target for Hackers
The Wall Street Journal: Shun This Basic Cybersecurity Tactic and Become a Target for Hackers

Press
Washington Post: Congress funds removal of Chinese telecom gear as feds probe home router risks
Washington Post: Congress funds removal of Chinese telecom gear as feds probe home router risks

Press
CNN: They were closing on their dream home. Then they fell for a little-known real estate scam
CNN: They were closing on their dream home. Then they fell for a little-known real estate scam

Press
Forbes: Watch For These Black Friday Scams—Especially Ones Created By AI
Forbes: Watch For These Black Friday Scams—Especially Ones Created By AI

Press
Cybernews: How Cyber Hacks Might Change Under Trump's Presidency
Cybernews: How Cyber Hacks Might Change Under Trump's Presidency

Press
Candid Recognition
Candid Recognition

Press
Fortune: How election misinformation thrived online during the 2024 presidential race—and will likely continue in the days to come
Fortune: How election misinformation thrived online during the 2024 presidential race—and will likely continue in the days to come

Press
Forbes: Does Generative AI Suffer from Shiny Object Syndrome?
Forbes: Does Generative AI Suffer from Shiny Object Syndrome?

Press
Forbes: 55% Of Employees Using AI At Work Have No Training On Its Risks
Forbes: 55% Of Employees Using AI At Work Have No Training On Its Risks

Press
STUDY: Less Than Half of AI Users Trained on Security and Privacy Risks
STUDY: Less Than Half of AI Users Trained on Security and Privacy Risks

Press
Huffington Post: Are You Being 'Spoofed'? This Specific Type Of Scam Is Hard To Catch.
Huffington Post: Are You Being 'Spoofed'? This Specific Type Of Scam Is Hard To Catch.

Press
Forbes: Seattle-Tacoma Airport Still Recovering From Weekend Cyberattack
Forbes: Seattle-Tacoma Airport Still Recovering From Weekend Cyberattack

Press
Business Insider: A former real-estate agent and her husband had to dip into retirement savings to buy a house after being scammed out of $63,000
Business Insider: A former real-estate agent and her husband had to dip into retirement savings to buy a house after being scammed out of $63,000

Press
Fox News: Records of nearly 3 billion people stolen in massive data breach lawsuit
Fox News: Records of nearly 3 billion people stolen in massive data breach lawsuit

Press
Huffington Post: Take This 1 Step ASAP If Your Social Security Number Is Part Of National Data Leak
Huffington Post: Take This 1 Step ASAP If Your Social Security Number Is Part Of National Data Leak

Press
CBS News: Hackers may have stolen the Social Security numbers of many Americans. Here's what to know.
CBS News: Hackers may have stolen the Social Security numbers of many Americans. Here's what to know.

Press
CBC: Florida company faces multiple lawsuits after massive data breach
CBC: Florida company faces multiple lawsuits after massive data breach

Press
CNBC: 2.9 billion people may have had Social Security numbers, other financial data compromised. What it means for you
CNBC: 2.9 billion people may have had Social Security numbers, other financial data compromised. What it means for you

Press
Global News: CrowdStrike outage, cyberattacks a ‘wake-up call’ to dangers of big tech reliance
Global News: CrowdStrike outage, cyberattacks a ‘wake-up call’ to dangers of big tech reliance

Press
Politico: White House responding to massive IT outage
Politico: White House responding to massive IT outage

Press
CNN: CDK Global outage has been hamstringing car dealerships for days. Experts say that’s the new normal for cyberattacks
CNN: CDK Global outage has been hamstringing car dealerships for days. Experts say that’s the new normal for cyberattacks

Press
A.P. News: Car dealerships in North America revert to pens and paper after cyberattacks on software provider
A.P. News: Car dealerships in North America revert to pens and paper after cyberattacks on software provider

Press
Reuters: CDK hack upends US auto industry, sending dealers back to paper forms
Reuters: CDK hack upends US auto industry, sending dealers back to paper forms

Press
The New York Times: What the Arrival of A.I. Phones and Computers Means for Our Data
The New York Times: What the Arrival of A.I. Phones and Computers Means for Our Data

Press
National Cybersecurity Alliance receives 2024 CSO Award from Foundry’s CSO
National Cybersecurity Alliance receives 2024 CSO Award from Foundry’s CSO

Press
National Cybersecurity Alliance receives 2024 CSO Award from Foundry's CSO
National Cybersecurity Alliance receives 2024 CSO Award from Foundry's CSO

Press
The Guardian: How Apple plans to usher in ‘new privacy standards’ with its long-awaited AI
The Guardian: How Apple plans to usher in ‘new privacy standards’ with its long-awaited AI

Press
CBS News: 5 Tips for Safe Online Shopping
CBS News: 5 Tips for Safe Online Shopping

Press
ArtNet NewS: ‘The Scams Keep Proliferating’ - Christie’s Historic Outage Reveals the Art World’s Digital Vulnerabilities
ArtNet NewS: ‘The Scams Keep Proliferating’ - Christie’s Historic Outage Reveals the Art World’s Digital Vulnerabilities

Press
National Cybersecurity Alliance Relaunches Cybersecure My Business Program
National Cybersecurity Alliance Relaunches Cybersecure My Business Program

Press
The Sun: RED ALERT How Chinese hackers could HIJACK EVs to crash cars and trap drivers in terrifying sabotage attacks
The Sun: RED ALERT How Chinese hackers could HIJACK EVs to crash cars and trap drivers in terrifying sabotage attacks

Press
New York Post: TikTok vows legal fight after Biden signs ‘unconstitutional’ ban - ‘We aren’t going anywhere’
New York Post: TikTok vows legal fight after Biden signs ‘unconstitutional’ ban - ‘We aren’t going anywhere’

Press
ExtremeTech: Meta Will Begin Labeling AI-Generated Content. Is It Enough to Combat Misinformation?
ExtremeTech: Meta Will Begin Labeling AI-Generated Content. Is It Enough to Combat Misinformation?

Press
NBC10 Boston: Don't forget your digital devices during your spring cleaning
NBC10 Boston: Don't forget your digital devices during your spring cleaning

Press
Fox Business: The most common tax season scams - and how to protect yourself
Fox Business: The most common tax season scams - and how to protect yourself

Press
The Verge: Will the Apple antitrust case lawsuit affect your phone’s security?
The Verge: Will the Apple antitrust case lawsuit affect your phone’s security?

Press
IT Brew: Why NCA Exec Director Lisa Plaggemier assumes no one cares
IT Brew: Why NCA Exec Director Lisa Plaggemier assumes no one cares

Press
Forbes: The TikTok Ban Is Truly An Issue Of National Security
Forbes: The TikTok Ban Is Truly An Issue Of National Security

Press
Reuters: Healthcare providers hit by frozen payments in ransomware outage
Reuters: Healthcare providers hit by frozen payments in ransomware outage

Press
Washington Post: How a health-care cyberattack may affect your prescription drug access
Washington Post: How a health-care cyberattack may affect your prescription drug access

Press
The New York Times: A Cyberattack on a UnitedHealth Unit Disrupts Prescription Drug Orders
The New York Times: A Cyberattack on a UnitedHealth Unit Disrupts Prescription Drug Orders

Press
The Street: How the company that traced fake Biden robocall identifies a synthetic voice
The Street: How the company that traced fake Biden robocall identifies a synthetic voice

Press
InformationWeek: NCA’s Plaggemier on Finding a Path to Data Privacy Compliance
InformationWeek: NCA’s Plaggemier on Finding a Path to Data Privacy Compliance

Press
NextGov: NCA celebrates National Data Privacy Week while CISA eyes new cybersecurity guidelines
NextGov: NCA celebrates National Data Privacy Week while CISA eyes new cybersecurity guidelines

Press
Security Boulevard: News alert - NCA’s Data Privacy Week webinars highlight data protection for consumers, businesses
Security Boulevard: News alert - NCA’s Data Privacy Week webinars highlight data protection for consumers, businesses

Press
Business Insider: An Innocent-looking Instagram Trend could be a gift to hackers, according to a cyber-security expert
Business Insider: An Innocent-looking Instagram Trend could be a gift to hackers, according to a cyber-security expert

Press
C&G Newspapers: Experts urge consumers to watch out for scams this holiday season
C&G Newspapers: Experts urge consumers to watch out for scams this holiday season

Press
Gizmodo: How To Spot Misinformation & Scams On TikTok
Gizmodo: How To Spot Misinformation & Scams On TikTok

Press
KIRO7: Medina Police Department warns of imposter pretending to be member of local agencIE
KIRO7: Medina Police Department warns of imposter pretending to be member of local agencIE

Press
CBS News: How to turn off iPhone's new NameDrop feature, the iOS 17 function authorities are warning about
CBS News: How to turn off iPhone's new NameDrop feature, the iOS 17 function authorities are warning about

Press
Bloomberg Markets: Cybersecurity Concerns amid Global Conflicts
Bloomberg Markets: Cybersecurity Concerns amid Global Conflicts

Press
Michigan Department of the Attorney General: Attorney General Warns Gen Z May Be More Likely Scam Victims
Michigan Department of the Attorney General: Attorney General Warns Gen Z May Be More Likely Scam Victims

Press
IT Brew: How to get young people (and everybody else) to care about cybersecurity
IT Brew: How to get young people (and everybody else) to care about cybersecurity

Press
Smart Industry: Cybersecurity stakeholders praise AI executive order—but say it’s just a start
Smart Industry: Cybersecurity stakeholders praise AI executive order—but say it’s just a start

Press
WhioTV7: Why scammers target teenagers, parents of young children
WhioTV7: Why scammers target teenagers, parents of young children

Press
Nasdaq: The Potential Cyber Threats of Visual and Audio AI Incorporation
Nasdaq: The Potential Cyber Threats of Visual and Audio AI Incorporation

Press
Signal: New AI Regulation to Create New Standards for Developers
Signal: New AI Regulation to Create New Standards for Developers

Press
Axios: New cyberattack disclosure rules make companies anxious
Axios: New cyberattack disclosure rules make companies anxious

Press
Engadget: The Best Password Managers for 2023
Engadget: The Best Password Managers for 2023

Press
Wharton on Sirius XM: Lisa Plaggemier on Wharton Business Daily
Wharton on Sirius XM: Lisa Plaggemier on Wharton Business Daily

Press
Dark Reading: From Snooze to Enthuse: Making Security Awareness Training 'Sticky'
Dark Reading: From Snooze to Enthuse: Making Security Awareness Training 'Sticky'

Press
National Cybersecurity Alliance Launches Kubikle, A New Video Web Series Demystifying Cybercrime
National Cybersecurity Alliance Launches Kubikle, A New Video Web Series Demystifying Cybercrime

Press
Help Net Security: Incentivizing secure online behavior across generations
Help Net Security: Incentivizing secure online behavior across generations

Press
DPO Download Podcast: Episode 11 - National Cybersecurity Alliance
DPO Download Podcast: Episode 11 - National Cybersecurity Alliance

Press
National Cybersecurity Alliance Kicks Off 20th Annual Cybersecurity Awareness Month
National Cybersecurity Alliance Kicks Off 20th Annual Cybersecurity Awareness Month

Press
Beta News: Gen Z twice as likely to think cybersecurity isn't worth the effort
Beta News: Gen Z twice as likely to think cybersecurity isn't worth the effort

Press
Cyberwire: CyberWire Daily Episode 1919
Cyberwire: CyberWire Daily Episode 1919

Press
Fortune: Nearly half of Americans have had personal data exposed by cyber criminals. The director of the National Cybersecurity Alliance says 4 behaviors can help reduce the threat
Fortune: Nearly half of Americans have had personal data exposed by cyber criminals. The director of the National Cybersecurity Alliance says 4 behaviors can help reduce the threat

Press
STUDY: 37% Intimidated, 39% Frustrated with Online Security Highlighting Digital Anxiety
STUDY: 37% Intimidated, 39% Frustrated with Online Security Highlighting Digital Anxiety

Press
USA Today: What Is This Charge On My Credit Card?
USA Today: What Is This Charge On My Credit Card?

Press
The Blast: Cybersecurity Expert Shares Information About Cyberattacks Like MGM's
The Blast: Cybersecurity Expert Shares Information About Cyberattacks Like MGM's

Press
SC Magazine: MGM Resorts ransomware recovery efforts nearly complete
SC Magazine: MGM Resorts ransomware recovery efforts nearly complete

Press
AP News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks
AP News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks

Press
Casino.org: MGM v. Caesars - Cybersecurity Expert Rates Hacking Responses
Casino.org: MGM v. Caesars - Cybersecurity Expert Rates Hacking Responses

Press
Las Vegas Sun: Cybersecurity demands that businesses constantly evolve Las Vegas Sun
Las Vegas Sun: Cybersecurity demands that businesses constantly evolve Las Vegas Sun

Press
Silicon Angle: Services at MGM Resorts restored following ransomware attack
Silicon Angle: Services at MGM Resorts restored following ransomware attack

Press
Technical.ly: DC Money Moves - Following its SPAC merger and subsequent lawsuit, IronNet is looking at bankruptcy
Technical.ly: DC Money Moves - Following its SPAC merger and subsequent lawsuit, IronNet is looking at bankruptcy

Press
ABC News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks
ABC News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks

Press
NBC Las Vegas: Several systems and functions remain down as MGM says casinos, hotels 'operating normally'
NBC Las Vegas: Several systems and functions remain down as MGM says casinos, hotels 'operating normally'

Press
Thrillist: What to Do if a Data Breach Exposes Your Personal Info While Traveling
Thrillist: What to Do if a Data Breach Exposes Your Personal Info While Traveling

Press
Hospitality Technology: MGM Data Breach Linked to Vishing
Hospitality Technology: MGM Data Breach Linked to Vishing

Press
The Record Media: Craigslist founder donates $200,000 to HBCU cybersecurity initiative
The Record Media: Craigslist founder donates $200,000 to HBCU cybersecurity initiative

Press
Dark Reading: National Cybersecurity Alliance Receives 200K Grant From Craig Newmark Philanthropies for HBCU Cybersecurity Program
Dark Reading: National Cybersecurity Alliance Receives 200K Grant From Craig Newmark Philanthropies for HBCU Cybersecurity Program

Press
National Cybersecurity Alliance Receives Generous 200K Grant from Craig Newmark Philanthropies for HBCU Cybersecurity Program
National Cybersecurity Alliance Receives Generous 200K Grant from Craig Newmark Philanthropies for HBCU Cybersecurity Program

Press
Government Technology: 2023 Cybersecurity Awareness Month Appeal - Make Online Security Easier
Government Technology: 2023 Cybersecurity Awareness Month Appeal - Make Online Security Easier

Press
Indianapolis Recorder: White House launches an education initiative to diversify the cyber industry
Indianapolis Recorder: White House launches an education initiative to diversify the cyber industry

Press
Global News: Have an old Gmail account? Google says inactive ones could be deleted
Global News: Have an old Gmail account? Google says inactive ones could be deleted

Press
National Cybersecurity Alliance Kicks-Off 2nd Year of “See Yourself In Cyber” HBCU Career Program
National Cybersecurity Alliance Kicks-Off 2nd Year of “See Yourself In Cyber” HBCU Career Program

Press
Tampa Bay Times: Florida Patients Among Victims of Spate of Data Hacking
Tampa Bay Times: Florida Patients Among Victims of Spate of Data Hacking

Press
Raconteur: Why Gen Z's Lack of Literacy is a Serious Business Risk
Raconteur: Why Gen Z's Lack of Literacy is a Serious Business Risk

Press
BizTech: Elevate Your Ransomware Defenses with a Post Incident Review
BizTech: Elevate Your Ransomware Defenses with a Post Incident Review

Press
Insurance Journal: The Industry Shouldn't Compete on Cybersecurity
Insurance Journal: The Industry Shouldn't Compete on Cybersecurity

Press
BizTech: What Is Active Directory Monitoring and Why Is AD a Target for Hackers?
BizTech: What Is Active Directory Monitoring and Why Is AD a Target for Hackers?

Press
Erie News Now: Keeping the LGBT+ Community Safe Online
Erie News Now: Keeping the LGBT+ Community Safe Online

Press
Engadget: The best password managers for 2023
Engadget: The best password managers for 2023

Press
Dark Reading: Volt Typhoon' Breaks Fresh Ground for China-Backed Cyber Campaigns
Dark Reading: Volt Typhoon' Breaks Fresh Ground for China-Backed Cyber Campaigns

Press
IT Brew: Asked and answered: 'What is the best defense against polymorphic malware?'
IT Brew: Asked and answered: 'What is the best defense against polymorphic malware?'

Press
National Geographic: Practical tips for protecting your data while traveling
National Geographic: Practical tips for protecting your data while traveling

Press
BizTech: How to Measure Your Team’s Email Security Savviness
BizTech: How to Measure Your Team’s Email Security Savviness

Press
The VIP Home Podcast: Top Internet Safety Tips to Keep Your Info Secure at Home
The VIP Home Podcast: Top Internet Safety Tips to Keep Your Info Secure at Home

Press
Infosecurity Magazine: Characterless Security Training Fails to Change User Behavior
Infosecurity Magazine: Characterless Security Training Fails to Change User Behavior

Press
National Cybersecurity Alliance launches HBCU Scholarship Program
National Cybersecurity Alliance launches HBCU Scholarship Program

Press
Technical.ly: Two nonprofits teamed up to offer HBCU tech students $20K in scholarships
Technical.ly: Two nonprofits teamed up to offer HBCU tech students $20K in scholarships

Press
National Cybersecurity Alliance Partners with One In Tech Foundation to Launch HBCU Scholarship Program
National Cybersecurity Alliance Partners with One In Tech Foundation to Launch HBCU Scholarship Program

Press
Cybersecurity Dive: Women in cybersecurity still fight for inclusion despite the talent shortage
Cybersecurity Dive: Women in cybersecurity still fight for inclusion despite the talent shortage

Press
CPO Magazine: Notorious Genesis Dark Web Market Taken Offline by Law Enforcement
CPO Magazine: Notorious Genesis Dark Web Market Taken Offline by Law Enforcement

Press
Washington Post: Watch out for online scams and vulnerabilities this tax season
Washington Post: Watch out for online scams and vulnerabilities this tax season

Press
National Cybersecurity Alliance Joins RSA Conference with a Discussion on Engagement through Entertainment
National Cybersecurity Alliance Joins RSA Conference with a Discussion on Engagement through Entertainment

Press
MAKE USE OF: 5 Kinds of Spyware You Need to Know About
MAKE USE OF: 5 Kinds of Spyware You Need to Know About

Press
Boston Globe: New details on LastPass breach mean it’s time for a new password manager
Boston Globe: New details on LastPass breach mean it’s time for a new password manager

Press
Sahan Journal: Minneapolis Public Schools acknowledges ‘threat actors’ could have accessed district data. Here’s what you need to know to protect yourself
Sahan Journal: Minneapolis Public Schools acknowledges ‘threat actors’ could have accessed district data. Here’s what you need to know to protect yourself

Press
The White House Readout: Office of National Cyber Director Hosts Roundtable on “The State of Cybersecurity in the Black Community”
The White House Readout: Office of National Cyber Director Hosts Roundtable on “The State of Cybersecurity in the Black Community”

Press
To the Point Podcast: So Many Cyber Scams - with Names Like Pig Butchering?! With Jennifer Cook
To the Point Podcast: So Many Cyber Scams - with Names Like Pig Butchering?! With Jennifer Cook

Press
VentureBeat: NCA executive director shares top cybersecurity risks in 2023
VentureBeat: NCA executive director shares top cybersecurity risks in 2023

Press
Help Net Security: Helping users and organizations build an instinctive data privacy habit
Help Net Security: Helping users and organizations build an instinctive data privacy habit

Press
PCMag: Why Tech Companies Are Looking to HBCUs to Expand the Cybersecurity Workforce
PCMag: Why Tech Companies Are Looking to HBCUs to Expand the Cybersecurity Workforce

Press
Tom's Guide: Don’t get burned this Valentine’s Day — these are the scams to look out forTom's Guide:
Tom's Guide: Don’t get burned this Valentine’s Day — these are the scams to look out forTom's Guide:

Press
Washington Post: Romance scammers could cause unhappy Valentine’s Day
Washington Post: Romance scammers could cause unhappy Valentine’s Day

Press
Washington Post: The State of the Union was light on cybersecurity
Washington Post: The State of the Union was light on cybersecurity

Press
IT Brew: Three ways to sell a privacy program to an exec who’s not listening
IT Brew: Three ways to sell a privacy program to an exec who’s not listening

Press
CNBC: How to protect yourself from tax fraud and scams, according to cybersecurity experts
CNBC: How to protect yourself from tax fraud and scams, according to cybersecurity experts

Press
CBS17: Are you a T-Mobile customer? Here’s how to protect yourself against data breaches
CBS17: Are you a T-Mobile customer? Here’s how to protect yourself against data breaches

Press
CyberWire: DragonSpark hits East Asia. ProxyNotShell in the wild. Privacy investment. IoT supply chain threat.
CyberWire: DragonSpark hits East Asia. ProxyNotShell in the wild. Privacy investment. IoT supply chain threat.

Press
TechRepublic: Data Privacy Week 2023 - Virtual events and webinars to attend
TechRepublic: Data Privacy Week 2023 - Virtual events and webinars to attend

Press
Channel Futures: 2023 Cybersecurity Outlook - Newer Targets, Tighter Budgets
Channel Futures: 2023 Cybersecurity Outlook - Newer Targets, Tighter Budgets

Press
VentureBeat: T-Mobile data breach shows API security can’t be ignored
VentureBeat: T-Mobile data breach shows API security can’t be ignored

Press
National Cybersecurity Alliance Announces Program for 2023 Data Privacy Week Campaign
National Cybersecurity Alliance Announces Program for 2023 Data Privacy Week Campaign

Press
T-Mobile January 2023 Data Breach Announcement: What You Should Do
T-Mobile January 2023 Data Breach Announcement: What You Should Do

Press
Reflections on Winter 2023 Convene
Reflections on Winter 2023 Convene

Press
IT Brew: Despite hacks, password managers are still an important SaaS security measure
IT Brew: Despite hacks, password managers are still an important SaaS security measure

Press
SDxCentral: TACKLING TECH’S TALENT SHORTAGE IN 2022
SDxCentral: TACKLING TECH’S TALENT SHORTAGE IN 2022

Press
PCMag: 2023 Could Be a Security Nightmare. Here’s Why
PCMag: 2023 Could Be a Security Nightmare. Here’s Why

Press
Security Intelligence: How to Embed Gen Z in Your Organization’s Security Culture
Security Intelligence: How to Embed Gen Z in Your Organization’s Security Culture

Press
Cyberwire: Updates on the cyber phases of a hybrid war
Cyberwire: Updates on the cyber phases of a hybrid war

Press
Cybernews: How to avoid hacking hangover at the airport this holiday season
Cybernews: How to avoid hacking hangover at the airport this holiday season

Press
AARP: 4 Tips for Talking to Your Kids and Grandkids about Fraud
AARP: 4 Tips for Talking to Your Kids and Grandkids about Fraud

Press
GitHub repojacking attack: 10 lessons for software teams
GitHub repojacking attack: 10 lessons for software teams

Press
Law360: Small Firms Need Cyber Protection As Much As Large Ones
Law360: Small Firms Need Cyber Protection As Much As Large Ones

Press
SpiceWorks: A Defense Playbook for Diffusing CCTV Cybersecurity Threats
SpiceWorks: A Defense Playbook for Diffusing CCTV Cybersecurity Threats

Press
Cyberwire: CISA releases voluntary CPGs. Trojans and scanners. Cyber venture investing, and some insights into corporate culture. "Opportunistic" cyberops in a hybrid war.
Cyberwire: CISA releases voluntary CPGs. Trojans and scanners. Cyber venture investing, and some insights into corporate culture. "Opportunistic" cyberops in a hybrid war.

Press
AiThority: Predictions Series 2022 - Interview with Lisa Plaggemier, Executive Director at National Cybersecurity Alliance
AiThority: Predictions Series 2022 - Interview with Lisa Plaggemier, Executive Director at National Cybersecurity Alliance

Press
Plex breach exposes usernames, emails, and encrypted passwords
Plex breach exposes usernames, emails, and encrypted passwords

Press
Cheddar: U.S. Cable Wake Up with Cheddar
Cheddar: U.S. Cable Wake Up with Cheddar

Press
CNBC: U.S. Cable Squawk on the street
CNBC: U.S. Cable Squawk on the street

Press
The Verge: How to rescue your hacked account: Facebook, Instagram, Snapchat, and more
The Verge: How to rescue your hacked account: Facebook, Instagram, Snapchat, and more

Press
BizTech: How Nonprofits Can Protect Their Donor Data in the Cloud
BizTech: How Nonprofits Can Protect Their Donor Data in the Cloud

Press
Channel Features: Pro-Russian Hacktivist Groups Take Down Numerous U.S. Airport Websites
Channel Features: Pro-Russian Hacktivist Groups Take Down Numerous U.S. Airport Websites

Press
National Cybersecurity Alliance Kicks Off 19th Annual Cybersecurity Awareness Month
National Cybersecurity Alliance Kicks Off 19th Annual Cybersecurity Awareness Month

Press
Beta News: A third of people fall victim to cyberattacks despite training
Beta News: A third of people fall victim to cyberattacks despite training

Press
STUDY: More than One-Third of Tech Users Fell Victim to Phishing Despite Access to Training Geared Towards Identifying Attacks
STUDY: More than One-Third of Tech Users Fell Victim to Phishing Despite Access to Training Geared Towards Identifying Attacks

Press
CRN: Experts At Amazon, Google, Dell - Cybersecurity Begins At Home
CRN: Experts At Amazon, Google, Dell - Cybersecurity Begins At Home

Press
SecureWorld: Cybersecurity Awareness Month Focuses on People
SecureWorld: Cybersecurity Awareness Month Focuses on People

Press
Infosecurity Magazine: Initiative Aims to Encourage Diverse Talent into Cyber
Infosecurity Magazine: Initiative Aims to Encourage Diverse Talent into Cyber

Press
SDX Central: Daily Roundup - Ericsson Releases Power-Efficient 5G Radio
SDX Central: Daily Roundup - Ericsson Releases Power-Efficient 5G Radio

Press
SDX Central: National Cybersecurity Alliance Launches Outreach, Mentorship Program
SDX Central: National Cybersecurity Alliance Launches Outreach, Mentorship Program

Press
The Record: CISA, Dell and more partner for HBCU cybersecurity program
The Record: CISA, Dell and more partner for HBCU cybersecurity program

Press
SC Magazine: National Cybersecurity Alliance launches HBCU career training program
SC Magazine: National Cybersecurity Alliance launches HBCU career training program

Press
National Cybersecurity Alliance Launches HBCU Career Program
National Cybersecurity Alliance Launches HBCU Career Program

Press
Channel Futures: Data Breach Hits Media Streaming Platform
Channel Futures: Data Breach Hits Media Streaming Platform

Press
Washington Post: Twitter has issues keeping your data secure. Here’s what you can do.
Washington Post: Twitter has issues keeping your data secure. Here’s what you can do.

Press
NCA Partners with Amazon on PSA Campaign to Educate Consumers about Online Cyber Threats and Best Practices to Protect Themselves
NCA Partners with Amazon on PSA Campaign to Educate Consumers about Online Cyber Threats and Best Practices to Protect Themselves

Press
AP Archive: Apple issues security warning for iPhones, devices
AP Archive: Apple issues security warning for iPhones, devices

Press
Dark Reading: Patch Now - 2 Apple Zero-Days Exploited in Wild
Dark Reading: Patch Now - 2 Apple Zero-Days Exploited in Wild

Press
Washington Post: Mandatory password updates are passe
Washington Post: Mandatory password updates are passe

Press
Forbes: Coalition Of Cybersecurity Leaders Launch Open Cybersecurity Schema Framework (OCSF)
Forbes: Coalition Of Cybersecurity Leaders Launch Open Cybersecurity Schema Framework (OCSF)

Press
IT Brew: Lazarus attackers mimic job recruiters
IT Brew: Lazarus attackers mimic job recruiters

Press
Morning Brew: Five remote-onboarding tips for IT pros
Morning Brew: Five remote-onboarding tips for IT pros

Press
USA Today: Helping small businesses and rural communities thwart cyberattacks
USA Today: Helping small businesses and rural communities thwart cyberattacks

Press
CPO Magazine: Game Publisher Bandai Namco Confirms a Suspected BlackCat Ransomware Attack
CPO Magazine: Game Publisher Bandai Namco Confirms a Suspected BlackCat Ransomware Attack

Press
Washington Post: Howard University cancels online, hybrid classes as it investigates alleged ransomware attack
Washington Post: Howard University cancels online, hybrid classes as it investigates alleged ransomware attack

Press
CyberWire: New hack de-anonymizes website users
CyberWire: New hack de-anonymizes website users

Press
Silicon Angle: Japanese video game publisher Bandai Namco targeted in ransomware attack
Silicon Angle: Japanese video game publisher Bandai Namco targeted in ransomware attack

Press
Street Fight Magazine: Retailers Prepare for Increased Cyber Attacks During Prime Day
Street Fight Magazine: Retailers Prepare for Increased Cyber Attacks During Prime Day

Press
The National Cybersecurity Alliance Named to CSO50
The National Cybersecurity Alliance Named to CSO50

Press
National Cybersecurity Alliance Named to CSO50
National Cybersecurity Alliance Named to CSO50

Press
Medscape: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks
Medscape: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks

Press
Get Involved In Identity Management Day
Get Involved In Identity Management Day

Press
Reader's Digest: How to Spot a Fake QR Code and Avoid Getting Scammed
Reader's Digest: How to Spot a Fake QR Code and Avoid Getting Scammed
Press
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy

Press
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity

Press
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity

Press
The Register: Biden signs cybercrime tracking bill into law
The Register: Biden signs cybercrime tracking bill into law

Press
National Cyber Security Alliance Statement Regarding Incorrect Small Business Statistic
National Cyber Security Alliance Statement Regarding Incorrect Small Business Statistic

Press
Forbes: Biden Signs Bill To Create Cybercrime Reporting System
Forbes: Biden Signs Bill To Create Cybercrime Reporting System

Press
News Radio 1120 KMOX: Stop writing down passwords
News Radio 1120 KMOX: Stop writing down passwords

Press
CSO: Meta, Apple emergency data request scam holds lessons for CISOs
CSO: Meta, Apple emergency data request scam holds lessons for CISOs

Press
Technical.ly: 5 reasons to consider a cybersecurity career in 2022
Technical.ly: 5 reasons to consider a cybersecurity career in 2022

Press
CSO: U.S. State Department unveils new Bureau of Cyberspace and Digital Policy
CSO: U.S. State Department unveils new Bureau of Cyberspace and Digital Policy

Press
Channel Futures: The Gately Report - Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022
Channel Futures: The Gately Report - Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022

Press
Channel Futures: Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022
Channel Futures: Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022

Press
Channel Futures: FCC Says Kaspersky Software Poses National Security Threat
Channel Futures: FCC Says Kaspersky Software Poses National Security Threat

Press
The Cyberwire: Russia's hybrid war with Ukraine: strategy, norms, and alliances
The Cyberwire: Russia's hybrid war with Ukraine: strategy, norms, and alliances

Press
Washington Post: Want to avoid a cyberattack? Stop ignoring those pesky software updates.
Washington Post: Want to avoid a cyberattack? Stop ignoring those pesky software updates.

Press
MarketWatch: The prospect of more Russian cyberattacks seems increasingly likely. What can you do to protect yourself? Quite a lot, it turns out.
MarketWatch: The prospect of more Russian cyberattacks seems increasingly likely. What can you do to protect yourself? Quite a lot, it turns out.

Press
CSO: NIST seeks information on updating its Cybersecurity Framework
CSO: NIST seeks information on updating its Cybersecurity Framework

Press
Washington Post: The Online Security Reset Guide: Keeping you safe from scammers, hackers and digital threats
Washington Post: The Online Security Reset Guide: Keeping you safe from scammers, hackers and digital threats

Press
Gov Info Security: Ukrainian Government Prepared to Wipe Servers
Gov Info Security: Ukrainian Government Prepared to Wipe Servers

Press
American Banker: Ransomware attacks are rising, payment security consortium warns
American Banker: Ransomware attacks are rising, payment security consortium warns

Press
Techspective: Lisa Plaggemier Discusses Cybersecurity at the Winter Olympics
Techspective: Lisa Plaggemier Discusses Cybersecurity at the Winter Olympics

Press
Well+Good: How To Spot a Scammer and Protect Yourself From Them, According to a Relationship Therapist and Cyber Security Expert
Well+Good: How To Spot a Scammer and Protect Yourself From Them, According to a Relationship Therapist and Cyber Security Expert

Press
AdWeek: How QR Codes Made Waves at the 2022 Super Bowl
AdWeek: How QR Codes Made Waves at the 2022 Super Bowl

Press
Media Post: 83.4 Million U.S. Smartphone Users Will Scan QR Codes This Year
Media Post: 83.4 Million U.S. Smartphone Users Will Scan QR Codes This Year

Press
PC Magazine: Coinbase's Mystery QR Code Super Bowl Ad Is a Security Nightmare
PC Magazine: Coinbase's Mystery QR Code Super Bowl Ad Is a Security Nightmare

Press
Gov Info Security: US SEC Proposes 48-Hour Incident Reporting Requirement
Gov Info Security: US SEC Proposes 48-Hour Incident Reporting Requirement

Press
Axios: Watch A conversation on internet safety in the modern digital era
Axios: Watch A conversation on internet safety in the modern digital era

Press
Broad and Breakfast: Companies Should Mandate Two-Factor Authentication, Says Head of National Cybersecurity Alliance
Broad and Breakfast: Companies Should Mandate Two-Factor Authentication, Says Head of National Cybersecurity Alliance

Press
Digital Anarchist: Data Privacy Week – Lisa Plaggemier, National Cyber Security Alliance
Digital Anarchist: Data Privacy Week – Lisa Plaggemier, National Cyber Security Alliance

Press
Inside the Games: Lisa Plaggemier - After Pyeongchang 2018 cyberattack, will Beijing 2022 be safe and secure?
Inside the Games: Lisa Plaggemier - After Pyeongchang 2018 cyberattack, will Beijing 2022 be safe and secure?

Press
Database Trends: Data Privacy Day 2022 - Industry Leaders Reflect on the Current State of Data Security
Database Trends: Data Privacy Day 2022 - Industry Leaders Reflect on the Current State of Data Security

Press
SD Times: The NCSA expands annual Data Privacy Day into Data Privacy Week
SD Times: The NCSA expands annual Data Privacy Day into Data Privacy Week

Press
Tech and Science Daily Podcast: Samsung's new Galaxy S22 - What to expect
Tech and Science Daily Podcast: Samsung's new Galaxy S22 - What to expect

Press
Auto Remarketing: KAR licenses privacy & security training program to NAAA-member auctions
Auto Remarketing: KAR licenses privacy & security training program to NAAA-member auctions

Press
Fox News: It's Data Privacy Week—here are some tips on staying safe while online
Fox News: It's Data Privacy Week—here are some tips on staying safe while online

Press
KMOX: Expert - Protecting your data can make a 'massive dent' in cybercrime
KMOX: Expert - Protecting your data can make a 'massive dent' in cybercrime

Press
Washington Post: Cyber fears mount amid prospect of Russian invasion of Ukraine
Washington Post: Cyber fears mount amid prospect of Russian invasion of Ukraine

Press
FOX NEWS: Online security and privacy is easy, not complicated
FOX NEWS: Online security and privacy is easy, not complicated
Press
National Cybersecurity Alliance Announces Program for Data Privacy Week
National Cybersecurity Alliance Announces Program for Data Privacy Week

Press
SECURITY BOULEVARD: FCC Proposes Stricter Regulations for Data Breach Disclosure
SECURITY BOULEVARD: FCC Proposes Stricter Regulations for Data Breach Disclosure

Press
SECURITY BOULEVARD: Why 2022 Should be a Year of Cybersecurity Optimism
SECURITY BOULEVARD: Why 2022 Should be a Year of Cybersecurity Optimism

Press
Why 2022 Is the Year of the Password Manager
Why 2022 Is the Year of the Password Manager

Press
CHANNEL FUTURES: 2022 Cybersecurity Predictions: Even More Reasonware, But Reason for Optimism
CHANNEL FUTURES: 2022 Cybersecurity Predictions: Even More Reasonware, But Reason for Optimism

Press
CSO: Security leaders on how to cope with stress of Log4j
CSO: Security leaders on how to cope with stress of Log4j

Press
Dark Reading: Meta Files Federal Lawsuit Against Phishing Operators
Dark Reading: Meta Files Federal Lawsuit Against Phishing Operators

Press
Channel Futures: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks
Channel Futures: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks

Press
Gov Info Security: US, Allies to Tighten Export Controls on Cyber Tools
Gov Info Security: US, Allies to Tighten Export Controls on Cyber Tools

Press
Politico: Washington’s cybersecurity wish list for 2022
Politico: Washington’s cybersecurity wish list for 2022

Press
Spiceworks: Tackling the Cybersecurity Talent Gap: 4 Tips for Employers
Spiceworks: Tackling the Cybersecurity Talent Gap: 4 Tips for Employers

Press
The Stevie® Awards: Honoring Excellence in Business Worldwide
The Stevie® Awards: Honoring Excellence in Business Worldwide

Press
KKTV: Don’t let grinches steal Christmas! How to stay safe when holiday shopping
KKTV: Don’t let grinches steal Christmas! How to stay safe when holiday shopping

Press
Security Boulevard: US, EU Join Paris Call for Cybersecurity
Security Boulevard: US, EU Join Paris Call for Cybersecurity

Press
Bank Info Security: VP Kamala Harris: US Will Join 80-Nation Cybersecurity Pact
Bank Info Security: VP Kamala Harris: US Will Join 80-Nation Cybersecurity Pact

Press
USA Today: After 7 million impacted in Robinhood data breach, experts offer some tips for amateur investors
USA Today: After 7 million impacted in Robinhood data breach, experts offer some tips for amateur investors

Press
Fast Company Robinhood data breach - Here’s what stock traders who use the platform need to know
Fast Company Robinhood data breach - Here’s what stock traders who use the platform need to know

Press
Gov Info Security: Infrastructure Bill Features $1.9 Billion in Cyber Funding
Gov Info Security: Infrastructure Bill Features $1.9 Billion in Cyber Funding

Press
Ping: How to Be Cyber Smart this Cybersecurity Awareness Month
Ping: How to Be Cyber Smart this Cybersecurity Awareness Month

Press
NBC: How to Keep Children Safe From Online Scams, Identity Theft
NBC: How to Keep Children Safe From Online Scams, Identity Theft

Press
State Scoop: It’s October. Are you aware of cybersecurity yet?
State Scoop: It’s October. Are you aware of cybersecurity yet?

Press
RBR: The InFOCUS Podcast - National Cybersecurity Alliance
RBR: The InFOCUS Podcast - National Cybersecurity Alliance

Press
EdTech: Next-Generation Firewall and IPSs Offer Proactive Protection for Higher Ed Networks
EdTech: Next-Generation Firewall and IPSs Offer Proactive Protection for Higher Ed Networks

Press
Light Reading: Sinclair hit by ransomware attack
Light Reading: Sinclair hit by ransomware attack

Press
NBC: Authorities See Rise in Ransomware Attacks, Urge Businesses to Prioritize Cybersecurity
NBC: Authorities See Rise in Ransomware Attacks, Urge Businesses to Prioritize Cybersecurity

Press
Bank Info Security: US Agencies to Water Facilities - You May Be Next Target
Bank Info Security: US Agencies to Water Facilities - You May Be Next Target

Press
Best Practices for People and Enterprise to #StaySafeOnline
Best Practices for People and Enterprise to #StaySafeOnline

Press
Gov Info Security: CISA to Access Agencies' Endpoints, Help Enhance Security
Gov Info Security: CISA to Access Agencies' Endpoints, Help Enhance Security

Press
NBC: Top 5 Things You Should Be Doing to Keep Your Information Safe Online
NBC: Top 5 Things You Should Be Doing to Keep Your Information Safe Online

Press
Security Boulevard: Public’s Knowledge of Cybersecurity Best Practices Sorely Lacking
Security Boulevard: Public’s Knowledge of Cybersecurity Best Practices Sorely Lacking

Press
Beta News: Highlighting the cybersecurity generation gap
Beta News: Highlighting the cybersecurity generation gap

Press
NBC: #BeCyberSmart - The Rise of Online Scams
NBC: #BeCyberSmart - The Rise of Online Scams

Press
Venture Beat: Cyberattacks are getting worse, but most people aren’t taking basic security steps
Venture Beat: Cyberattacks are getting worse, but most people aren’t taking basic security steps

Press
Venture Beat: It’s Cybersecurity Awareness Month. Does your business have a viable plan yet?
Venture Beat: It’s Cybersecurity Awareness Month. Does your business have a viable plan yet?

Press
STUDY: Millennials and Gen Z Say They are Bigger Victims of Cybercrime
STUDY: Millennials and Gen Z Say They are Bigger Victims of Cybercrime

Press
National Cyber Security Alliance Kicks Off 18th Annual Cybersecurity Awareness Month
National Cyber Security Alliance Kicks Off 18th Annual Cybersecurity Awareness Month

Press
Forensics: CYBERSECURITY AWARENESS MONTH 2021 - AN EXPERT’S ADVOCACY GUIDE
Forensics: CYBERSECURITY AWARENESS MONTH 2021 - AN EXPERT’S ADVOCACY GUIDE

Press
CBS: Apple says its security flaw was fixed. Cyber analysts warn zero-click threats will persist.
CBS: Apple says its security flaw was fixed. Cyber analysts warn zero-click threats will persist.

Press
The Learning Counsel: How To Safeguard Schools Against Cyber Attacks this School Year
The Learning Counsel: How To Safeguard Schools Against Cyber Attacks this School Year

Press
Venture Beat: Why cyber scare tactics have missed the mark
Venture Beat: Why cyber scare tactics have missed the mark

Press
Healthcare IT News: FBI, CISA warn: Hackers won't take a vacation
Healthcare IT News: FBI, CISA warn: Hackers won't take a vacation

Press
The Cyberwire: WhatsApp patches bug. Twitter updates its features to promote “social privacy.” Labor Day threats to data privacy.
The Cyberwire: WhatsApp patches bug. Twitter updates its features to promote “social privacy.” Labor Day threats to data privacy.

Press
Channel Futures: Hackers Again Setting Sights on Microsoft Exchange Vulnerabilities
Channel Futures: Hackers Again Setting Sights on Microsoft Exchange Vulnerabilities

Press
TDWI: How Organizations Can Stay Protected Online
TDWI: How Organizations Can Stay Protected Online

Press
Bank Info Security: World Bank Launches Global Cybersecurity Fund
Bank Info Security: World Bank Launches Global Cybersecurity Fund

Press
Techinal.ly: Resource Roundup: Level up in cyber, IT and entrepreneurship with these 4 DC-area programs
Techinal.ly: Resource Roundup: Level up in cyber, IT and entrepreneurship with these 4 DC-area programs

Press
Cyber Magazine: National Cyber Security Alliance to launch new resource bank
Cyber Magazine: National Cyber Security Alliance to launch new resource bank

Press
Washington Post: The Cybersecurity 202: There was another massive data breach. People will probably forget it in a week.
Washington Post: The Cybersecurity 202: There was another massive data breach. People will probably forget it in a week.

Press
SC Magazine: NCSA creates cyber career resource library to educate our future infosec workforce
SC Magazine: NCSA creates cyber career resource library to educate our future infosec workforce

Press
Security Magazine: National Cyber Security Alliance launches new cyber initiative
Security Magazine: National Cyber Security Alliance launches new cyber initiative

Press
National Cyber Security Alliance Unveils Cybersecurity Education and Career Resource Library
National Cyber Security Alliance Unveils Cybersecurity Education and Career Resource Library

Press
Cybersecurity Dive: How the $1.2 trillion infrastructure bill invests in cyber
Cybersecurity Dive: How the $1.2 trillion infrastructure bill invests in cyber

Press
Gov Info Security: OMB Spells Out Agencies' Cybersecurity Timelines
Gov Info Security: OMB Spells Out Agencies' Cybersecurity Timelines

Press
CIO Dive: Preparedness, checklists, leadership buy-in - How to build a rapid IT response
CIO Dive: Preparedness, checklists, leadership buy-in - How to build a rapid IT response

Press
Gov Info Security: Patching Woes: Most Frequently Exploited CVEs Listed
Gov Info Security: Patching Woes: Most Frequently Exploited CVEs Listed

Press
What the Dev? Cybersecurity and the Tokyo Olympics - Episode 113
What the Dev? Cybersecurity and the Tokyo Olympics - Episode 113

Press
Fox: Tokyo Olympics could be threatened by cyberattack, FBI warns
Fox: Tokyo Olympics could be threatened by cyberattack, FBI warns

Press
Channel Futures: Tokyo Olympics Contending with Cyber Threats, FBI Warns of More Coming
Channel Futures: Tokyo Olympics Contending with Cyber Threats, FBI Warns of More Coming

Press
Threat Post: Indictments, Attribution Unlikely to Deter Chinese Hacking, Researchers Say
Threat Post: Indictments, Attribution Unlikely to Deter Chinese Hacking, Researchers Say

Press
Auto Remarketing: National Cyber Security Alliance on trends in automotive
Auto Remarketing: National Cyber Security Alliance on trends in automotive
Press
National Cyber Security Alliance Announces Leadership Transition
National Cyber Security Alliance Announces Leadership Transition

Press
Law 360: Kaseya Ransomware Hit Casts Wide Net Of Potential Liability
Law 360: Kaseya Ransomware Hit Casts Wide Net Of Potential Liability

Press
Bloomberg: Kaseya Software Hack Highlights Small Business Security Squeeze
Bloomberg: Kaseya Software Hack Highlights Small Business Security Squeeze

Press
Washington Post: The Cybersecurity 202: The Kaseya attack is a revolution in sophistication for ransomware hackers
Washington Post: The Cybersecurity 202: The Kaseya attack is a revolution in sophistication for ransomware hackers

Press
Auto News: Ransomware attacks could crimp industry’s recovery from pandemic, report says
Auto News: Ransomware attacks could crimp industry’s recovery from pandemic, report says

Press
Healthcare Info Security: Battling Ongoing COVID-19-Themed Attacks and Scams
Healthcare Info Security: Battling Ongoing COVID-19-Themed Attacks and Scams

Press
Digital Anarchist: Cybersecurity Safety Review Board – Kelvin Coleman, NCSA
Digital Anarchist: Cybersecurity Safety Review Board – Kelvin Coleman, NCSA

Press
WSJ: Hackers Stole $650,000 From Nonprofit and Got Away, Showing Limits to Law Enforcement’s Reach
WSJ: Hackers Stole $650,000 From Nonprofit and Got Away, Showing Limits to Law Enforcement’s Reach

Press
NBC: Who's in charge here? Colonial Pipeline hack exposes huge holes in U.S. cyber defenses, say experts
NBC: Who's in charge here? Colonial Pipeline hack exposes huge holes in U.S. cyber defenses, say experts

Press
Channel Futures: Significant Ramifications
Channel Futures: Significant Ramifications

Press
Ed Tech: To Improve Higher Ed Data Security, Address These Risks in Research Projects
Ed Tech: To Improve Higher Ed Data Security, Address These Risks in Research Projects

Press
Endpoint: Why We Still Need World Password Day
Endpoint: Why We Still Need World Password Day

Press
Health IT Security: Google Sued, Lawsuit Claims COVID-19 Contact Tracing Tool Exposes Data
Health IT Security: Google Sued, Lawsuit Claims COVID-19 Contact Tracing Tool Exposes Data

Press
Associations Now: Spring Clean Your Digital Files
Associations Now: Spring Clean Your Digital Files

Press
Hacked.com: Why Every Business Should Train Employees to Spot Phishing Emails
Hacked.com: Why Every Business Should Train Employees to Spot Phishing Emails

Press
TechTarget: SolarWinds puts national cybersecurity strategy on display
TechTarget: SolarWinds puts national cybersecurity strategy on display

Press
Hacked.com: The Top 5 Reasons Hackers Might Target Your Small Business
Hacked.com: The Top 5 Reasons Hackers Might Target Your Small Business

Press
Martech Series: Beyond Identity Integration With Auth0 Enables Completely Passwordless Authentication
Martech Series: Beyond Identity Integration With Auth0 Enables Completely Passwordless Authentication

Press
SC Magazine: On first-ever Identity Management Day, experts detail steps to a better IAM program
SC Magazine: On first-ever Identity Management Day, experts detail steps to a better IAM program

Press
Dark Reading: Biden Nominates Former NSA Officials for Top Cybersecurity Roles
Dark Reading: Biden Nominates Former NSA Officials for Top Cybersecurity Roles

Press
WSJ: Biden Administration Announces National Cyber, CISA Director Nominations
WSJ: Biden Administration Announces National Cyber, CISA Director Nominations

Press
Accounting Today: IRS and COVID vaccine email scams proliferating this tax season
Accounting Today: IRS and COVID vaccine email scams proliferating this tax season

Press
Healthcare IT News: How cybercriminals exploit COVID-19, and how to protect against them
Healthcare IT News: How cybercriminals exploit COVID-19, and how to protect against them

Press
Security Magazine: 5 minutes with Kelvin Coleman - Remote learning and data privacy issues
Security Magazine: 5 minutes with Kelvin Coleman - Remote learning and data privacy issues

Press
Gov Info Security: Exchange Hacks: How Will the Biden Administration Respond?
Gov Info Security: Exchange Hacks: How Will the Biden Administration Respond?

Press
Above the Law: Keeping Your Data Safe In The Remote Work Era
Above the Law: Keeping Your Data Safe In The Remote Work Era

Press
The Cyberwire: Patching, with special attention to Hafnium and the rest. Responding to the SolarWinds incident. Hactivists don’t like cameras. Dragnet in the Low Countries.
The Cyberwire: Patching, with special attention to Hafnium and the rest. Responding to the SolarWinds incident. Hactivists don’t like cameras. Dragnet in the Low Countries.

Press
Health Leaders Media: NCSA ON CYBERSECURITY: 'UPDATE, UPDATE, UPDATE'
Health Leaders Media: NCSA ON CYBERSECURITY: 'UPDATE, UPDATE, UPDATE'

Press
MedCity News: When it comes to healthcare cybersecurity, the best defense is also the most simple
MedCity News: When it comes to healthcare cybersecurity, the best defense is also the most simple

Press
Washington Post: The Cybersecurity 202: Scammers are already targeting the next round of coronavirus relief checks
Washington Post: The Cybersecurity 202: Scammers are already targeting the next round of coronavirus relief checks

Press
Healthcare Info Security: Fraudsters Devise More COVID-19 Vaccine Schemes
Healthcare Info Security: Fraudsters Devise More COVID-19 Vaccine Schemes

Press
CIO Dive: Legacy tech, privacy and security issues bog down healthcare innovation
CIO Dive: Legacy tech, privacy and security issues bog down healthcare innovation

Press
Identity Defined Security Alliance Partners with National Cyber Security Alliance to Launch First-Ever ‘Identity Management Day’ April 13, 2021
Identity Defined Security Alliance Partners with National Cyber Security Alliance to Launch First-Ever ‘Identity Management Day’ April 13, 2021

Press
CNET: Apple AirTags: How to Protect Yourself From Being Tracked
CNET: Apple AirTags: How to Protect Yourself From Being Tracked

Press
FedTech Magazine: The Importance of Supply Chain Risk Management in Government
FedTech Magazine: The Importance of Supply Chain Risk Management in Government

Press
NBC: Fraud Investigations Holding Up Unemployment Payments
NBC: Fraud Investigations Holding Up Unemployment Payments

Press
WSJ: U.S. Water Supply Has Few Protections Against Hacking
WSJ: U.S. Water Supply Has Few Protections Against Hacking

Press
Digital Anarchist: Kelvin Coleman – TechStrong TV
Digital Anarchist: Kelvin Coleman – TechStrong TV

Press
HealthTech Magazine: How to Keep Telehealth Secure
HealthTech Magazine: How to Keep Telehealth Secure

Press
SDX Central: Is Biden’s $10B Enough to Make US Cybersecurity Great Again?
SDX Central: Is Biden’s $10B Enough to Make US Cybersecurity Great Again?

Press
Datanami: Data Privacy in the Crosshairs
Datanami: Data Privacy in the Crosshairs

Press
SC Magazine: Speed of White House cyber appointments should make CISOs ‘a bit more confident’
SC Magazine: Speed of White House cyber appointments should make CISOs ‘a bit more confident’

Press
National Cyber Security Alliance Kicks off Data Privacy Day This Week to Raise Awareness for Responsible Data Privacy Practices
National Cyber Security Alliance Kicks off Data Privacy Day This Week to Raise Awareness for Responsible Data Privacy Practices

Press
Protocol: Why an ‘internet blackout’ probably isn’t coming on inauguration day
Protocol: Why an ‘internet blackout’ probably isn’t coming on inauguration day

Press
SC Magazine: Free cyber career training coursework emerges as a perk in tough times
SC Magazine: Free cyber career training coursework emerges as a perk in tough times

Press
Digital Anarchist: TechStrong TV – January 14, 2021
Digital Anarchist: TechStrong TV – January 14, 2021

Press
Security Boulevard: Data Privacy Day - Understanding COVID-19’s Impact
Security Boulevard: Data Privacy Day - Understanding COVID-19’s Impact

Press
GCN: IT cleanup at U.S. Capitol presents massive challenge
GCN: IT cleanup at U.S. Capitol presents massive challenge

Press
Security Week: Experts Weigh In on Cybersecurity Risks of Capitol-Like Attacks
Security Week: Experts Weigh In on Cybersecurity Risks of Capitol-Like Attacks

Press
TidBITS: Cybersecurity Ramifications of the 2021 Storming of the United States Capitol
TidBITS: Cybersecurity Ramifications of the 2021 Storming of the United States Capitol

Press
Wired: Post-Riot, the Capitol Hill IT Staff Faces a Security Mess
Wired: Post-Riot, the Capitol Hill IT Staff Faces a Security Mess

Press
Channel Futures: US Capitol Rioters Pose Cybersecurity Threat Due to Device Access, Theft
Channel Futures: US Capitol Rioters Pose Cybersecurity Threat Due to Device Access, Theft

Press
Data Center Knowledge: What Data Center IT Security Pros Must Know About the SolarWinds Vulnerability
Data Center Knowledge: What Data Center IT Security Pros Must Know About the SolarWinds Vulnerability

Press
In wake of SolarWinds hack, here are the critical responses required of all businesses
In wake of SolarWinds hack, here are the critical responses required of all businesses

Press
Tech Targets: Cybersecurity employee training: How to build a solid plan
Tech Targets: Cybersecurity employee training: How to build a solid plan

Press
The Hill: Scammers step up efforts to target older Americans during pandemic
The Hill: Scammers step up efforts to target older Americans during pandemic

Press
Digital Trends: The digital switch that blocks all websites from selling your personal data
Digital Trends: The digital switch that blocks all websites from selling your personal data

Press
Faith, Health & Home Podcast: How to Keep Your Family Safe Online | Kelvin Coleman, Exec. Director, Nat'l Cyber Security Alliance
Faith, Health & Home Podcast: How to Keep Your Family Safe Online | Kelvin Coleman, Exec. Director, Nat'l Cyber Security Alliance

Press
Bank Info Security: APT Groups Target Firms Working on COVID-19 Vaccines
Bank Info Security: APT Groups Target Firms Working on COVID-19 Vaccines

Press
Forbes: 6 Cybersecurity Tips When You Work From Home
Forbes: 6 Cybersecurity Tips When You Work From Home

Press
Barracuda: Age plays a role in end-user security training
Barracuda: Age plays a role in end-user security training

Press
Dark Reading: 7 Online Shopping Tips for the Holidays
Dark Reading: 7 Online Shopping Tips for the Holidays

Press
The Daily Swig: Europol campaign urges e-commerce retailers to #SellSafe this Black Friday
The Daily Swig: Europol campaign urges e-commerce retailers to #SellSafe this Black Friday

Press
Healthcare IT News: Hospitals said to tighten email security in response to CEO spear phishing attempts
Healthcare IT News: Hospitals said to tighten email security in response to CEO spear phishing attempts

Press
Dark Reading: Online Users Feel Safe, But Risky Behavior Abounds
Dark Reading: Online Users Feel Safe, But Risky Behavior Abounds

Press
Healthcare IT News: NCSA Confidence in security of connected devices often misplaced
Healthcare IT News: NCSA Confidence in security of connected devices often misplaced

Press
The Cyberwire: CISA says no evidence of successful foreign election hacks. QBot’s voting-themed malspam. RegretLocker arriving.
The Cyberwire: CISA says no evidence of successful foreign election hacks. QBot’s voting-themed malspam. RegretLocker arriving.

Press
24x7 Magazine: 81% of Americans Highly Confident Connected Devices Secure Despite Overlooking Basic Security Hygiene
24x7 Magazine: 81% of Americans Highly Confident Connected Devices Secure Despite Overlooking Basic Security Hygiene

Press
Beta News: Consumers overconfident of their connected device security
Beta News: Consumers overconfident of their connected device security

Press
Infosecurity Magazine: Americans Confident in IoT Device Security
Infosecurity Magazine: Americans Confident in IoT Device Security

Press
SC Magazine: New data shows just how badly home users overestimate IoT security
SC Magazine: New data shows just how badly home users overestimate IoT security

Press
Dot Med: Five minutes in healthcare - featuring Kelvin Coleman
Dot Med: Five minutes in healthcare - featuring Kelvin Coleman

Press
Security Boulevard: U.S. Health Care Under Attack
Security Boulevard: U.S. Health Care Under Attack

Press
Healthcare IT Today: Government Agencies Warn of Imminent Cybercrime Threat from Ransomware Targeted at Hospitals
Healthcare IT Today: Government Agencies Warn of Imminent Cybercrime Threat from Ransomware Targeted at Hospitals

Press
The Cyberwire: Ransomware versus patient medical data. Patching and updating. A new loader in town.
The Cyberwire: Ransomware versus patient medical data. Patching and updating. A new loader in town.

Press
Health Leaders Media: CISA, FBI, HHS WARN HOSPITALS OF 'INCREASED AND IMMINENT' CYBERCRIME THREAT
Health Leaders Media: CISA, FBI, HHS WARN HOSPITALS OF 'INCREASED AND IMMINENT' CYBERCRIME THREAT

Press
Health IT Answers: The Future of Connected Devices
Health IT Answers: The Future of Connected Devices

Press
Health IT Security: Phishing Campaigns Mimic Microsoft Teams, HHS COVID-19 Vaccine Tracker
Health IT Security: Phishing Campaigns Mimic Microsoft Teams, HHS COVID-19 Vaccine Tracker

Press
Healthcare Info Security: COVID-19 Growing Cybersecurity Risks
Healthcare Info Security: COVID-19 Growing Cybersecurity Risks

Press
Health IT Security: Rapid Threat Evolution Spurs Crucial Healthcare Cybersecurity Needs
Health IT Security: Rapid Threat Evolution Spurs Crucial Healthcare Cybersecurity Needs

Press
Spiceworks: How SMBs Can Stay on Top of the Evolving Threat Landscape
Spiceworks: How SMBs Can Stay on Top of the Evolving Threat Landscape

Press
Forbes: Communicate With Confidence Through A Cyber Crisis
Forbes: Communicate With Confidence Through A Cyber Crisis

Press
Healthcare Info Security: Cybersecurity Advice for the COVID-19 Era
Healthcare Info Security: Cybersecurity Advice for the COVID-19 Era

Press
Dark Reading:A 7-Step Cybersecurity Plan for Healthcare Organizations
Dark Reading:A 7-Step Cybersecurity Plan for Healthcare Organizations

Press
ABC: Computer security expert shares tips on staying safe amid surge in cybercrime
ABC: Computer security expert shares tips on staying safe amid surge in cybercrime

Press
Tech Republic: 3 ways criminals use artificial intelligence in cybersecurity attacks
Tech Republic: 3 ways criminals use artificial intelligence in cybersecurity attacks

Press
TechTarget: Healthcare cybersecurity needs a dose of threat modeling
TechTarget: Healthcare cybersecurity needs a dose of threat modeling

Press
Infosecurity Magazine: #NCSAM: Is Connected Ever Going to be Protected?
Infosecurity Magazine: #NCSAM: Is Connected Ever Going to be Protected?

Press
The Cyberwire: Cyber conflict in the Caucasus. Zerologon exploited in the wild. Emotet rising. Silicon Valley’s Gilded Age?
The Cyberwire: Cyber conflict in the Caucasus. Zerologon exploited in the wild. Emotet rising. Silicon Valley’s Gilded Age?

Press
Cybersecurity Awareness Month Around The World | Bangladesh, Canada, And Central/South America | With Kazi Mustafiz, Christine Menard, and Gabriela Montes de Oca Fehr
Cybersecurity Awareness Month Around The World | Bangladesh, Canada, And Central/South America | With Kazi Mustafiz, Christine Menard, and Gabriela Montes de Oca Fehr

Press
Nextgov: CISA Leader Puts Health Sector Project on the Level of Election Security Initiative
Nextgov: CISA Leader Puts Health Sector Project on the Level of Election Security Initiative
Press
Washington Post: The Cybersecurity 202: Americans are as insecure as ever on the 17th annual Cybersecurity Awareness month
Washington Post: The Cybersecurity 202: Americans are as insecure as ever on the 17th annual Cybersecurity Awareness month

Press
It Is Cybersecurity Awareness Month | A Chat With NCSA And CISA To Learn What Is New This Year | With Kelvin Coleman, Brandon Wales, And Lisa Plaggemier
It Is Cybersecurity Awareness Month | A Chat With NCSA And CISA To Learn What Is New This Year | With Kelvin Coleman, Brandon Wales, And Lisa Plaggemier

Press
Data Breach Today: Incident Response: Taking a More Deliberate Approach
Data Breach Today: Incident Response: Taking a More Deliberate Approach

Press
Dark Reading: 7 Summer Travel Security Tips
Dark Reading: 7 Summer Travel Security Tips

Press
Security Week: Industry Reactions to Twitter Hack - Feedback Friday
Security Week: Industry Reactions to Twitter Hack - Feedback Friday

Press
USA Today: 'Tweet-tastrophe'? It could have been. Twitter hack reveals national security threat before election
USA Today: 'Tweet-tastrophe'? It could have been. Twitter hack reveals national security threat before election

Press
IT Ops Times: Twitter attack highlights the need for security awareness training
IT Ops Times: Twitter attack highlights the need for security awareness training

Press
Threat Post: Twitter Confirms it Was Hacked in an Unprecedented Cryptocurrency Scam
Threat Post: Twitter Confirms it Was Hacked in an Unprecedented Cryptocurrency Scam

Press
Bank Info Security: Several Prominent Twitter Accounts Hijacked in Cryptocurrency Scam
Bank Info Security: Several Prominent Twitter Accounts Hijacked in Cryptocurrency Scam

Press
SD Times: Contact tracing apps need to establish trust to be effective
SD Times: Contact tracing apps need to establish trust to be effective

Press
Politico: CISA funding bill, EAC hearing on 2020 primary woes on slate this week
Politico: CISA funding bill, EAC hearing on 2020 primary woes on slate this week

Press
Channel Futures: Tech Startups Hemorrhaging Jobs During Pandemic
Channel Futures: Tech Startups Hemorrhaging Jobs During Pandemic

Press
Politico: Early Covid-19 tracking apps easy prey for hackers, and it might get worse before it gets better
Politico: Early Covid-19 tracking apps easy prey for hackers, and it might get worse before it gets better

Press
Tech Republic: Be prepared: Why you need an incident response policy
Tech Republic: Be prepared: Why you need an incident response policy

Press
CNBC: CLEAR is poised to lead the multibillion-dollar biometric screening race for the coronavirus
CNBC: CLEAR is poised to lead the multibillion-dollar biometric screening race for the coronavirus

Press
ABC: Criminals are pretending to be the government, World Health Organization; here's what to watch out for
ABC: Criminals are pretending to be the government, World Health Organization; here's what to watch out for

Press
Health IT Security: COVID-19 Contact Tracing Apps Spotlight Privacy, Security Rights
Health IT Security: COVID-19 Contact Tracing Apps Spotlight Privacy, Security Rights

Press
NCSA Announces Partnership with National White Collar Crime Center
NCSA Announces Partnership with National White Collar Crime Center

Press
Digital Trends: Contact-tracing apps may seem like the coronavirus solution. They’re not
Digital Trends: Contact-tracing apps may seem like the coronavirus solution. They’re not

Press
CNBC: Utah has rejected the Apple-Google approach to tracing coronavirus, and is using an app made by a social media start-up instead
CNBC: Utah has rejected the Apple-Google approach to tracing coronavirus, and is using an app made by a social media start-up instead

Press
Dark Reading: 7 Ways Parents Can Better Protect Their Online-Gamer Offspring
Dark Reading: 7 Ways Parents Can Better Protect Their Online-Gamer Offspring

Press
Built In: How Healthcare Cybersecurity Is Affected by the Coronavirus Pandemic
Built In: How Healthcare Cybersecurity Is Affected by the Coronavirus Pandemic

Press
National Cyber Security Alliance Encourages Vigilance Against Coronavirus Scams, Best Cybersecurity Practices for Remote Workers
National Cyber Security Alliance Encourages Vigilance Against Coronavirus Scams, Best Cybersecurity Practices for Remote Workers

Press
National Cyber Security Alliance Supports RSA® Conference Theme “The Human Element” with Expert Panel on Cybersecurity and Changing Human Behavior
National Cyber Security Alliance Supports RSA® Conference Theme “The Human Element” with Expert Panel on Cybersecurity and Changing Human Behavior

Press
On January 28, Data Privacy Day Encourages Consumers to “Own Their Privacy” and Businesses to Improve Their Data Privacy Practices
On January 28, Data Privacy Day Encourages Consumers to “Own Their Privacy” and Businesses to Improve Their Data Privacy Practices

Press
Free and Fun Security Awareness Videos: Brought to you by Adobe, the National Cybersecurity Alliance, and Speechless, Inc.
Free and Fun Security Awareness Videos: Brought to you by Adobe, the National Cybersecurity Alliance, and Speechless, Inc.

Press
National Cyber Security Alliance Hosts Online Safety Workshops for Consumers and Small Businesses in Indianapolis
National Cyber Security Alliance Hosts Online Safety Workshops for Consumers and Small Businesses in Indianapolis

Press
16th Annual National Cybersecurity Awareness Month Begins Today
16th Annual National Cybersecurity Awareness Month Begins Today

Press
Countdown to National Cybersecurity Awareness Month 2019 Begins
Countdown to National Cybersecurity Awareness Month 2019 Begins

Press
The National Cyber Security Alliance and ITSPmagazine Announce Partnership in Support of CyberSecure My Business™
The National Cyber Security Alliance and ITSPmagazine Announce Partnership in Support of CyberSecure My Business™

Press
The National Cyber Security Alliance and the Better Business Bureau Recommend Top Online “Take-Action Tips” to Help Keep You Safe and Secure
The National Cyber Security Alliance and the Better Business Bureau Recommend Top Online “Take-Action Tips” to Help Keep You Safe and Secure

Press
The National Cyber Security Alliance Welcomes Three Prominent Industry Leaders to Board of Directors
The National Cyber Security Alliance Welcomes Three Prominent Industry Leaders to Board of Directors

Press
The National Cyber Security Alliance Welcomes New Board Members
The National Cyber Security Alliance Welcomes New Board Members

Press
National Cyber Security Alliance Reminds Organizations of All Sizes that “Privacy is Good for Business”
National Cyber Security Alliance Reminds Organizations of All Sizes that “Privacy is Good for Business”

Press
Data Privacy Day 2019 Reminds Businesses and Consumers About the Value of Personal Data and the Need to Protect It
Data Privacy Day 2019 Reminds Businesses and Consumers About the Value of Personal Data and the Need to Protect It

Press
Make a Digital New Year’s Resolution: Keep Your Computer Systems and Software Up to Date
Make a Digital New Year’s Resolution: Keep Your Computer Systems and Software Up to Date

Press
National Cyber Security Alliance Responds to Marriott Cybersecurity Incident
National Cyber Security Alliance Responds to Marriott Cybersecurity Incident

Press
The National Cyber Security Alliance Appoints Kelvin Coleman as Executive Director
The National Cyber Security Alliance Appoints Kelvin Coleman as Executive Director

Press
Cheers to Safe Cybershopping!
Cheers to Safe Cybershopping!

Press
Intel and National Cyber Security Alliance Team Up to Remind Cool Cats Nationwide to Protect Their Nine Digital Lives and #UpdateMeow
Intel and National Cyber Security Alliance Team Up to Remind Cool Cats Nationwide to Protect Their Nine Digital Lives and #UpdateMeow

Press
The National Cyber Security Alliance Announces Winners for the First-Ever National Cyber Security Alliance Awards
The National Cyber Security Alliance Announces Winners for the First-Ever National Cyber Security Alliance Awards

Press
Safeguarding the Nation’s Infrastructure Needs to Be “Our Shared Responsibility”
Safeguarding the Nation’s Infrastructure Needs to Be “Our Shared Responsibility”

Press
It’s Everyone’s Job to Ensure Online Safety at Work
It’s Everyone’s Job to Ensure Online Safety at Work

Press
The Severe Shortage of Cybersecurity Professionals is a Key Risk to Our Nation’s Security
The Severe Shortage of Cybersecurity Professionals is a Key Risk to Our Nation’s Security

Press
Make Your Home a Haven for Online Safety
Make Your Home a Haven for Online Safety

Press
Two Weeks and Counting Until National Cybersecurity Awareness Month Kicks Off on Oct. 1
Two Weeks and Counting Until National Cybersecurity Awareness Month Kicks Off on Oct. 1

Press
Higher Ed Joins Forces with Nonprofit and Business to Promote Cyber Safety on Campus
Higher Ed Joins Forces with Nonprofit and Business to Promote Cyber Safety on Campus

Press
All Systems Go: The 15th Annual National Cybersecurity Awareness Month Launches on October 1
All Systems Go: The 15th Annual National Cybersecurity Awareness Month Launches on October 1

Press
Stay #CyberAware on Mobile Devices during Internet Safety Month and All Year Round
Stay #CyberAware on Mobile Devices during Internet Safety Month and All Year Round

Press
National Cyber Security Alliance Executive Director Russ Schrader Addresses Cyber Challenges Facing Small Businesses at Senate Hearing
National Cyber Security Alliance Executive Director Russ Schrader Addresses Cyber Challenges Facing Small Businesses at Senate Hearing

Press
The National Cyber Security Alliance and Better Business Bureau Encourage “Digital Spring Cleaning” for Everyone
The National Cyber Security Alliance and Better Business Bureau Encourage “Digital Spring Cleaning” for Everyone

Press
NCSA and Nasdaq Cybersecurity Summit Examines How to Better Protect the Expanding Cloud Ecosystem From Security Threats
NCSA and Nasdaq Cybersecurity Summit Examines How to Better Protect the Expanding Cloud Ecosystem From Security Threats

Press
National Cyber Security Alliance Supports RSA® Conference’s Mission to Inspire All Digital Citizens to Take Action and Help Secure the World Against Cyber Threats
National Cyber Security Alliance Supports RSA® Conference’s Mission to Inspire All Digital Citizens to Take Action and Help Secure the World Against Cyber Threats

Press
The National Cyber Security Alliance Appoints Russell Schrader as Interim Executive Director
The National Cyber Security Alliance Appoints Russell Schrader as Interim Executive Director

Press
Data Privacy Day Reminds Everyone About the Value of Their Personal Information and How to Manage Online Privacy
Data Privacy Day Reminds Everyone About the Value of Their Personal Information and How to Manage Online Privacy

Press
New Video Showcases How Financial Institutions Work with Government Agencies to Remediate Phishing Cyber Attack
New Video Showcases How Financial Institutions Work with Government Agencies to Remediate Phishing Cyber Attack

Press
National Cyber Security Awareness Month Highlights Strengthening the Cyber Workforce as a Starting Point to a Safer, More Secure Online Future
National Cyber Security Awareness Month Highlights Strengthening the Cyber Workforce as a Starting Point to a Safer, More Secure Online Future

Press
Second Annual National Cyber Security Alliance Survey Reveals Complex Digital Lives of American Teens and Parents, Highlights Gender Divide
Second Annual National Cyber Security Alliance Survey Reveals Complex Digital Lives of American Teens and Parents, Highlights Gender Divide

Press
National Cyber Security Awareness Month Reminds Everyone That Smart Devices Are Fueled By Our Personal Information
National Cyber Security Awareness Month Reminds Everyone That Smart Devices Are Fueled By Our Personal Information

Press
Organization Leaders and Employees Reminded That “Cybersecurity in the Workplace Is Everyone’s Business” This National Cyber Security Awareness Month
Organization Leaders and Employees Reminded That “Cybersecurity in the Workplace Is Everyone’s Business” This National Cyber Security Awareness Month

Press
National Cyber Security Alliance Statement Following Report on Three Billion Accounts Hacked in 2013 Yahoo Breach
National Cyber Security Alliance Statement Following Report on Three Billion Accounts Hacked in 2013 Yahoo Breach

Press
National Cyber Security Awareness Month Launches With a Call to STOP. THINK. CONNECT.™ Online
National Cyber Security Awareness Month Launches With a Call to STOP. THINK. CONNECT.™ Online

Press
On October 1, Digital Citizens Worldwide Will Be Reminded of Our Shared Global Responsibility to Secure the Internet
On October 1, Digital Citizens Worldwide Will Be Reminded of Our Shared Global Responsibility to Secure the Internet

Press
National Cyber Security Alliance Responds to Equifax Breach
National Cyber Security Alliance Responds to Equifax Breach

Press
The Countdown to National Cyber Security Awareness Month Begins!
The Countdown to National Cyber Security Awareness Month Begins!

Press
SC Magazine’s Women in IT Security: Influencers Honors NCSA Director of Special Projects and Government Affairs Kristin Judge
SC Magazine’s Women in IT Security: Influencers Honors NCSA Director of Special Projects and Government Affairs Kristin Judge

Press
National Cyber Security Alliance Statement on International Cyber Attack
National Cyber Security Alliance Statement on International Cyber Attack

Press
NCSA and Nasdaq Cybersecurity Summit Tackles Cyber-Related “People Problems” in the Workplace
NCSA and Nasdaq Cybersecurity Summit Tackles Cyber-Related “People Problems” in the Workplace

Press
The National Cyber Security Alliance and Thatcher & Company Awarded Two Silver Anvils from PRSA
The National Cyber Security Alliance and Thatcher & Company Awarded Two Silver Anvils from PRSA

Press
NCSA Statement on the Ransomware Attack
NCSA Statement on the Ransomware Attack

Press
National Cyber Security Alliance and Better Business Bureau Remind All Internet Users to Do a Digital Spring Cleaning and Clear Out Cyber Clutter
National Cyber Security Alliance and Better Business Bureau Remind All Internet Users to Do a Digital Spring Cleaning and Clear Out Cyber Clutter

Press
The National Cyber Security Alliance and Nasdaq Host Timely, Enterprise-focused Discussion about Cybersecurity Risk Management and Emerging Threats
The National Cyber Security Alliance and Nasdaq Host Timely, Enterprise-focused Discussion about Cybersecurity Risk Management and Emerging Threats

Press
NCSA Tribute to Howard Schmidt
NCSA Tribute to Howard Schmidt

Press
Data Privacy Day Reminds Organizations That Protecting Customers’ Privacy is Critical to Their Business
Data Privacy Day Reminds Organizations That Protecting Customers’ Privacy is Critical to Their Business

Press
The National Cyber Security Alliance Recommends “Five Digital To Do's” for 2017
The National Cyber Security Alliance Recommends “Five Digital To Do's” for 2017

Press
Response Statement: Mark Zuckerberg’s Hacked Pinterest Account
Response Statement: Mark Zuckerberg’s Hacked Pinterest Account

Press
Industry Leaders from NXP Semiconductors and Salesforce Join the National Cyber Security Alliance’s Board of Directors
Industry Leaders from NXP Semiconductors and Salesforce Join the National Cyber Security Alliance’s Board of Directors

Press
As National Cyber Security Awareness Month Comes to a Close, Focus Shifts to Securing Our Nation’s Critical Infrastructure
As National Cyber Security Awareness Month Comes to a Close, Focus Shifts to Securing Our Nation’s Critical Infrastructure

Press
Continued Growth of the “Internet of Me” Has 88 Percent of Consumers Considering the Risks of Using Connected Devices
Continued Growth of the “Internet of Me” Has 88 Percent of Consumers Considering the Risks of Using Connected Devices

Press
Fight Cybercrime During National Cyber Security Awareness Month: It’s Time to Take Action, Safeguard Devices and Protect Personal Information
Fight Cybercrime During National Cyber Security Awareness Month: It’s Time to Take Action, Safeguard Devices and Protect Personal Information

Press
Businesses of All Sizes Urged to Create Culture of Cybersecurity and Protect Assets This National Cyber Security Awareness Month
Businesses of All Sizes Urged to Create Culture of Cybersecurity and Protect Assets This National Cyber Security Awareness Month

Press
White House and the National Cyber Security Alliance Join Forces to Launch
White House and the National Cyber Security Alliance Join Forces to Launch

Press
National Cyber Security Awareness Month Launches with a Call to Action for All Digital Citizens to STOP. THINK. CONNECT.™
National Cyber Security Awareness Month Launches with a Call to Action for All Digital Citizens to STOP. THINK. CONNECT.™

Press
Fast-Approaching National Cyber Security Awareness Month Reminds All Digital Citizens That Cybersecurity is a Shared Responsibility
Fast-Approaching National Cyber Security Awareness Month Reminds All Digital Citizens That Cybersecurity is a Shared Responsibility

Press
Tips for Securing Frequent Flier Miles
Tips for Securing Frequent Flier Miles
Press
National Cyber Security Alliance Statement Following Reported Massive Data Breach at Yahoo! Inc.
National Cyber Security Alliance Statement Following Reported Massive Data Breach at Yahoo! Inc.

Press
National Cyber Security Awareness Month Is Only A Month Away!
National Cyber Security Awareness Month Is Only A Month Away!

Press
Beware of Ransomware
Beware of Ransomware

Press
Statement following report of massive data breach at major email providers
Statement following report of massive data breach at major email providers

Press
National Cyber Security Alliance Survey Reveals the Complex Digital Lives of American Teens and Parents
National Cyber Security Alliance Survey Reveals the Complex Digital Lives of American Teens and Parents

Press
National Cyber Security Alliance and Better Business Bureau Urge Digital Spring Cleaning for All Internet Users
National Cyber Security Alliance and Better Business Bureau Urge Digital Spring Cleaning for All Internet Users

Press
State Legislators Identify Major Opportunities to Address Cybersecurity Gaps
State Legislators Identify Major Opportunities to Address Cybersecurity Gaps

Press
National Cyber Security Alliance Returns to RSA® Conference with a Mission to Educate and Empower Digital Citizens of All Ages about Cybersecurity and Privacy Awareness
National Cyber Security Alliance Returns to RSA® Conference with a Mission to Educate and Empower Digital Citizens of All Ages about Cybersecurity and Privacy Awareness

Press
National Cyber Security Alliance Announces Expansion of Multi-Factor Authentication-Focused Education
National Cyber Security Alliance Announces Expansion of Multi-Factor Authentication-Focused Education

Press
White House Fact Sheet: Cybersecurity National Action Plan
White House Fact Sheet: Cybersecurity National Action Plan

Press
British Internet Users Concerned About Data Privacy Than Losing Their Income
British Internet Users Concerned About Data Privacy Than Losing Their Income

Press
Cisco Joins the National Cyber Security Alliance’s Board of Directors
Cisco Joins the National Cyber Security Alliance’s Board of Directors

Press
Digital New Year’s Resolutions To Keep Everyone Safer And More Secure Online
Digital New Year’s Resolutions To Keep Everyone Safer And More Secure Online

Press
National Cyber Security Awareness Month Seeks #TalentHack Solutions to Overcome the Cybersecurity Skills Gap
National Cyber Security Awareness Month Seeks #TalentHack Solutions to Overcome the Cybersecurity Skills Gap

Press
As the Internet of Things Grows Exponentially, National Cyber Security Awareness Month Focuses on Securing our Connected Devices and Networks
As the Internet of Things Grows Exponentially, National Cyber Security Awareness Month Focuses on Securing our Connected Devices and Networks

Press
Connected Families And Communities In The Spotlight During National Cyber Security Awareness Month
Connected Families And Communities In The Spotlight During National Cyber Security Awareness Month

Press
ESET and National Cyber Security Alliance Study Reveals Almost 80 Percent of American Homes Feel Cyber Secure Despite Unsecured Digital Doors
ESET and National Cyber Security Alliance Study Reveals Almost 80 Percent of American Homes Feel Cyber Secure Despite Unsecured Digital Doors

Press
Small And Midsized Businesses Learn To Protect Their Digital Assets During National Cyber Security Awareness Month
Small And Midsized Businesses Learn To Protect Their Digital Assets During National Cyber Security Awareness Month

Press
NCSA statement following report of data breach at Experian, Exposing T-Mobile Customer Data
NCSA statement following report of data breach at Experian, Exposing T-Mobile Customer Data

Press
National Cyber Security Awareness Month Kicks Off As Growing Global Coalition Urges Internet Users Everywhere To STOP. THINK. CONNECT.
National Cyber Security Awareness Month Kicks Off As Growing Global Coalition Urges Internet Users Everywhere To STOP. THINK. CONNECT.

Press
As National Cyber Security Awareness Month Approaches, Internet Users Are Reminded Why Being Cyber Smart is Critical to Our Lives
As National Cyber Security Awareness Month Approaches, Internet Users Are Reminded Why Being Cyber Smart is Critical to Our Lives

Press
One-Month Countdown to National Cyber Security Awareness Month Begins
One-Month Countdown to National Cyber Security Awareness Month Begins

Press
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy

Press
Council of Anti-Phishing Japan Launches STOP.THINK.CONNECT. Cybersecurity Awareness Campaign with National Public-Private Coalition
Council of Anti-Phishing Japan Launches STOP.THINK.CONNECT. Cybersecurity Awareness Campaign with National Public-Private Coalition

Press
STOP.THINK.CONNECT.™: Broad Government, Industry and Non-Profit Coalition Unveils First-Ever Coordinated Online Safety Message
STOP.THINK.CONNECT.™: Broad Government, Industry and Non-Profit Coalition Unveils First-Ever Coordinated Online Safety Message

Press
National Cybersecurity Alliance Receives 2025 CSO Award from Foundry’s CSO
National Cybersecurity Alliance Receives 2025 CSO Award from Foundry’s CSO

Press
Newsday: LI's Broadridge, Verint testing new Chinese chatbot DeepSeek for automation, efficiency
Newsday: LI's Broadridge, Verint testing new Chinese chatbot DeepSeek for automation, efficiency

Press
Fox Tampa Bay: Tech experts warn of Valentine's Day romance scams as Meta takes steps to protect users
Fox Tampa Bay: Tech experts warn of Valentine's Day romance scams as Meta takes steps to protect users

Press
ABC Philly: FBI issues warning on romance scams ahead of Valentine's Day
ABC Philly: FBI issues warning on romance scams ahead of Valentine's Day

Press
Kiplinger: Hey Valentine, Beware of Catfishing Romance Scams
Kiplinger: Hey Valentine, Beware of Catfishing Romance Scams

Press
PC Mag: Which AI ChatBot Collects the Least of Your Data?
PC Mag: Which AI ChatBot Collects the Least of Your Data?

Press
Gizmodo: The Knives are Coming Out for DeepSeek AI
Gizmodo: The Knives are Coming Out for DeepSeek AI

Press
Data Privacy Week 2025 Press Release
Data Privacy Week 2025 Press Release

Press
Vanity Fair: Is TikTok Really Worth Saving?
Vanity Fair: Is TikTok Really Worth Saving?

Press
Newsweek: PowerSchool Breach Victim Says Hackers Stole All Student Data
Newsweek: PowerSchool Breach Victim Says Hackers Stole All Student Data

Press
The Huffington Post: LA Fire Donation Scams Are Everywhere. Here's How To Spot Them
The Huffington Post: LA Fire Donation Scams Are Everywhere. Here's How To Spot Them

Press
USA Today: Scammers may be taking advantage of the California wildfires - How to protect yourself
USA Today: Scammers may be taking advantage of the California wildfires - How to protect yourself

Press
The Wall Street Journal: Shun This Basic Cybersecurity Tactic and Become a Target for Hackers
The Wall Street Journal: Shun This Basic Cybersecurity Tactic and Become a Target for Hackers

Press
Washington Post: Congress funds removal of Chinese telecom gear as feds probe home router risks
Washington Post: Congress funds removal of Chinese telecom gear as feds probe home router risks

Press
CNN: They were closing on their dream home. Then they fell for a little-known real estate scam
CNN: They were closing on their dream home. Then they fell for a little-known real estate scam

Press
Forbes: Watch For These Black Friday Scams—Especially Ones Created By AI
Forbes: Watch For These Black Friday Scams—Especially Ones Created By AI

Press
Cybernews: How Cyber Hacks Might Change Under Trump's Presidency
Cybernews: How Cyber Hacks Might Change Under Trump's Presidency

Press
Candid Recognition
Candid Recognition

Press
Fortune: How election misinformation thrived online during the 2024 presidential race—and will likely continue in the days to come
Fortune: How election misinformation thrived online during the 2024 presidential race—and will likely continue in the days to come

Press
Forbes: Does Generative AI Suffer from Shiny Object Syndrome?
Forbes: Does Generative AI Suffer from Shiny Object Syndrome?

Press
Forbes: 55% Of Employees Using AI At Work Have No Training On Its Risks
Forbes: 55% Of Employees Using AI At Work Have No Training On Its Risks

Press
STUDY: Less Than Half of AI Users Trained on Security and Privacy Risks
STUDY: Less Than Half of AI Users Trained on Security and Privacy Risks

Press
Huffington Post: Are You Being 'Spoofed'? This Specific Type Of Scam Is Hard To Catch.
Huffington Post: Are You Being 'Spoofed'? This Specific Type Of Scam Is Hard To Catch.

Press
Forbes: Seattle-Tacoma Airport Still Recovering From Weekend Cyberattack
Forbes: Seattle-Tacoma Airport Still Recovering From Weekend Cyberattack

Press
Business Insider: A former real-estate agent and her husband had to dip into retirement savings to buy a house after being scammed out of $63,000
Business Insider: A former real-estate agent and her husband had to dip into retirement savings to buy a house after being scammed out of $63,000

Press
Fox News: Records of nearly 3 billion people stolen in massive data breach lawsuit
Fox News: Records of nearly 3 billion people stolen in massive data breach lawsuit

Press
Huffington Post: Take This 1 Step ASAP If Your Social Security Number Is Part Of National Data Leak
Huffington Post: Take This 1 Step ASAP If Your Social Security Number Is Part Of National Data Leak

Press
CBS News: Hackers may have stolen the Social Security numbers of many Americans. Here's what to know.
CBS News: Hackers may have stolen the Social Security numbers of many Americans. Here's what to know.

Press
CBC: Florida company faces multiple lawsuits after massive data breach
CBC: Florida company faces multiple lawsuits after massive data breach

Press
CNBC: 2.9 billion people may have had Social Security numbers, other financial data compromised. What it means for you
CNBC: 2.9 billion people may have had Social Security numbers, other financial data compromised. What it means for you

Press
Global News: CrowdStrike outage, cyberattacks a ‘wake-up call’ to dangers of big tech reliance
Global News: CrowdStrike outage, cyberattacks a ‘wake-up call’ to dangers of big tech reliance

Press
Politico: White House responding to massive IT outage
Politico: White House responding to massive IT outage

Press
CNN: CDK Global outage has been hamstringing car dealerships for days. Experts say that’s the new normal for cyberattacks
CNN: CDK Global outage has been hamstringing car dealerships for days. Experts say that’s the new normal for cyberattacks

Press
A.P. News: Car dealerships in North America revert to pens and paper after cyberattacks on software provider
A.P. News: Car dealerships in North America revert to pens and paper after cyberattacks on software provider

Press
Reuters: CDK hack upends US auto industry, sending dealers back to paper forms
Reuters: CDK hack upends US auto industry, sending dealers back to paper forms

Press
The New York Times: What the Arrival of A.I. Phones and Computers Means for Our Data
The New York Times: What the Arrival of A.I. Phones and Computers Means for Our Data

Press
National Cybersecurity Alliance receives 2024 CSO Award from Foundry’s CSO
National Cybersecurity Alliance receives 2024 CSO Award from Foundry’s CSO

Press
National Cybersecurity Alliance receives 2024 CSO Award from Foundry's CSO
National Cybersecurity Alliance receives 2024 CSO Award from Foundry's CSO

Press
The Guardian: How Apple plans to usher in ‘new privacy standards’ with its long-awaited AI
The Guardian: How Apple plans to usher in ‘new privacy standards’ with its long-awaited AI

Press
CBS News: 5 Tips for Safe Online Shopping
CBS News: 5 Tips for Safe Online Shopping

Press
ArtNet NewS: ‘The Scams Keep Proliferating’ - Christie’s Historic Outage Reveals the Art World’s Digital Vulnerabilities
ArtNet NewS: ‘The Scams Keep Proliferating’ - Christie’s Historic Outage Reveals the Art World’s Digital Vulnerabilities

Press
National Cybersecurity Alliance Relaunches Cybersecure My Business Program
National Cybersecurity Alliance Relaunches Cybersecure My Business Program

Press
The Sun: RED ALERT How Chinese hackers could HIJACK EVs to crash cars and trap drivers in terrifying sabotage attacks
The Sun: RED ALERT How Chinese hackers could HIJACK EVs to crash cars and trap drivers in terrifying sabotage attacks

Press
New York Post: TikTok vows legal fight after Biden signs ‘unconstitutional’ ban - ‘We aren’t going anywhere’
New York Post: TikTok vows legal fight after Biden signs ‘unconstitutional’ ban - ‘We aren’t going anywhere’

Press
ExtremeTech: Meta Will Begin Labeling AI-Generated Content. Is It Enough to Combat Misinformation?
ExtremeTech: Meta Will Begin Labeling AI-Generated Content. Is It Enough to Combat Misinformation?

Press
NBC10 Boston: Don't forget your digital devices during your spring cleaning
NBC10 Boston: Don't forget your digital devices during your spring cleaning

Press
Fox Business: The most common tax season scams - and how to protect yourself
Fox Business: The most common tax season scams - and how to protect yourself

Press
The Verge: Will the Apple antitrust case lawsuit affect your phone’s security?
The Verge: Will the Apple antitrust case lawsuit affect your phone’s security?

Press
IT Brew: Why NCA Exec Director Lisa Plaggemier assumes no one cares
IT Brew: Why NCA Exec Director Lisa Plaggemier assumes no one cares

Press
Forbes: The TikTok Ban Is Truly An Issue Of National Security
Forbes: The TikTok Ban Is Truly An Issue Of National Security

Press
Reuters: Healthcare providers hit by frozen payments in ransomware outage
Reuters: Healthcare providers hit by frozen payments in ransomware outage

Press
Washington Post: How a health-care cyberattack may affect your prescription drug access
Washington Post: How a health-care cyberattack may affect your prescription drug access

Press
The New York Times: A Cyberattack on a UnitedHealth Unit Disrupts Prescription Drug Orders
The New York Times: A Cyberattack on a UnitedHealth Unit Disrupts Prescription Drug Orders

Press
The Street: How the company that traced fake Biden robocall identifies a synthetic voice
The Street: How the company that traced fake Biden robocall identifies a synthetic voice

Press
InformationWeek: NCA’s Plaggemier on Finding a Path to Data Privacy Compliance
InformationWeek: NCA’s Plaggemier on Finding a Path to Data Privacy Compliance

Press
NextGov: NCA celebrates National Data Privacy Week while CISA eyes new cybersecurity guidelines
NextGov: NCA celebrates National Data Privacy Week while CISA eyes new cybersecurity guidelines

Press
Security Boulevard: News alert - NCA’s Data Privacy Week webinars highlight data protection for consumers, businesses
Security Boulevard: News alert - NCA’s Data Privacy Week webinars highlight data protection for consumers, businesses

Press
Business Insider: An Innocent-looking Instagram Trend could be a gift to hackers, according to a cyber-security expert
Business Insider: An Innocent-looking Instagram Trend could be a gift to hackers, according to a cyber-security expert

Press
C&G Newspapers: Experts urge consumers to watch out for scams this holiday season
C&G Newspapers: Experts urge consumers to watch out for scams this holiday season

Press
Gizmodo: How To Spot Misinformation & Scams On TikTok
Gizmodo: How To Spot Misinformation & Scams On TikTok

Press
KIRO7: Medina Police Department warns of imposter pretending to be member of local agencIE
KIRO7: Medina Police Department warns of imposter pretending to be member of local agencIE

Press
CBS News: How to turn off iPhone's new NameDrop feature, the iOS 17 function authorities are warning about
CBS News: How to turn off iPhone's new NameDrop feature, the iOS 17 function authorities are warning about

Press
Bloomberg Markets: Cybersecurity Concerns amid Global Conflicts
Bloomberg Markets: Cybersecurity Concerns amid Global Conflicts

Press
Michigan Department of the Attorney General: Attorney General Warns Gen Z May Be More Likely Scam Victims
Michigan Department of the Attorney General: Attorney General Warns Gen Z May Be More Likely Scam Victims

Press
IT Brew: How to get young people (and everybody else) to care about cybersecurity
IT Brew: How to get young people (and everybody else) to care about cybersecurity

Press
Smart Industry: Cybersecurity stakeholders praise AI executive order—but say it’s just a start
Smart Industry: Cybersecurity stakeholders praise AI executive order—but say it’s just a start

Press
WhioTV7: Why scammers target teenagers, parents of young children
WhioTV7: Why scammers target teenagers, parents of young children

Press
Nasdaq: The Potential Cyber Threats of Visual and Audio AI Incorporation
Nasdaq: The Potential Cyber Threats of Visual and Audio AI Incorporation

Press
Signal: New AI Regulation to Create New Standards for Developers
Signal: New AI Regulation to Create New Standards for Developers

Press
Axios: New cyberattack disclosure rules make companies anxious
Axios: New cyberattack disclosure rules make companies anxious

Press
Engadget: The Best Password Managers for 2023
Engadget: The Best Password Managers for 2023

Press
Wharton on Sirius XM: Lisa Plaggemier on Wharton Business Daily
Wharton on Sirius XM: Lisa Plaggemier on Wharton Business Daily

Press
Dark Reading: From Snooze to Enthuse: Making Security Awareness Training 'Sticky'
Dark Reading: From Snooze to Enthuse: Making Security Awareness Training 'Sticky'

Press
National Cybersecurity Alliance Launches Kubikle, A New Video Web Series Demystifying Cybercrime
National Cybersecurity Alliance Launches Kubikle, A New Video Web Series Demystifying Cybercrime

Press
Help Net Security: Incentivizing secure online behavior across generations
Help Net Security: Incentivizing secure online behavior across generations

Press
DPO Download Podcast: Episode 11 - National Cybersecurity Alliance
DPO Download Podcast: Episode 11 - National Cybersecurity Alliance

Press
National Cybersecurity Alliance Kicks Off 20th Annual Cybersecurity Awareness Month
National Cybersecurity Alliance Kicks Off 20th Annual Cybersecurity Awareness Month

Press
Beta News: Gen Z twice as likely to think cybersecurity isn't worth the effort
Beta News: Gen Z twice as likely to think cybersecurity isn't worth the effort

Press
Cyberwire: CyberWire Daily Episode 1919
Cyberwire: CyberWire Daily Episode 1919

Press
Fortune: Nearly half of Americans have had personal data exposed by cyber criminals. The director of the National Cybersecurity Alliance says 4 behaviors can help reduce the threat
Fortune: Nearly half of Americans have had personal data exposed by cyber criminals. The director of the National Cybersecurity Alliance says 4 behaviors can help reduce the threat

Press
STUDY: 37% Intimidated, 39% Frustrated with Online Security Highlighting Digital Anxiety
STUDY: 37% Intimidated, 39% Frustrated with Online Security Highlighting Digital Anxiety

Press
USA Today: What Is This Charge On My Credit Card?
USA Today: What Is This Charge On My Credit Card?

Press
The Blast: Cybersecurity Expert Shares Information About Cyberattacks Like MGM's
The Blast: Cybersecurity Expert Shares Information About Cyberattacks Like MGM's

Press
SC Magazine: MGM Resorts ransomware recovery efforts nearly complete
SC Magazine: MGM Resorts ransomware recovery efforts nearly complete

Press
AP News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks
AP News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks

Press
Casino.org: MGM v. Caesars - Cybersecurity Expert Rates Hacking Responses
Casino.org: MGM v. Caesars - Cybersecurity Expert Rates Hacking Responses

Press
Las Vegas Sun: Cybersecurity demands that businesses constantly evolve Las Vegas Sun
Las Vegas Sun: Cybersecurity demands that businesses constantly evolve Las Vegas Sun

Press
Silicon Angle: Services at MGM Resorts restored following ransomware attack
Silicon Angle: Services at MGM Resorts restored following ransomware attack

Press
Technical.ly: DC Money Moves - Following its SPAC merger and subsequent lawsuit, IronNet is looking at bankruptcy
Technical.ly: DC Money Moves - Following its SPAC merger and subsequent lawsuit, IronNet is looking at bankruptcy

Press
ABC News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks
ABC News: MGM Resorts computers back up after 10 days as analysts eye effects of casino cyberattacks

Press
NBC Las Vegas: Several systems and functions remain down as MGM says casinos, hotels 'operating normally'
NBC Las Vegas: Several systems and functions remain down as MGM says casinos, hotels 'operating normally'

Press
Thrillist: What to Do if a Data Breach Exposes Your Personal Info While Traveling
Thrillist: What to Do if a Data Breach Exposes Your Personal Info While Traveling

Press
Hospitality Technology: MGM Data Breach Linked to Vishing
Hospitality Technology: MGM Data Breach Linked to Vishing

Press
The Record Media: Craigslist founder donates $200,000 to HBCU cybersecurity initiative
The Record Media: Craigslist founder donates $200,000 to HBCU cybersecurity initiative

Press
Dark Reading: National Cybersecurity Alliance Receives 200K Grant From Craig Newmark Philanthropies for HBCU Cybersecurity Program
Dark Reading: National Cybersecurity Alliance Receives 200K Grant From Craig Newmark Philanthropies for HBCU Cybersecurity Program

Press
National Cybersecurity Alliance Receives Generous 200K Grant from Craig Newmark Philanthropies for HBCU Cybersecurity Program
National Cybersecurity Alliance Receives Generous 200K Grant from Craig Newmark Philanthropies for HBCU Cybersecurity Program

Press
Government Technology: 2023 Cybersecurity Awareness Month Appeal - Make Online Security Easier
Government Technology: 2023 Cybersecurity Awareness Month Appeal - Make Online Security Easier

Press
Indianapolis Recorder: White House launches an education initiative to diversify the cyber industry
Indianapolis Recorder: White House launches an education initiative to diversify the cyber industry

Press
Global News: Have an old Gmail account? Google says inactive ones could be deleted
Global News: Have an old Gmail account? Google says inactive ones could be deleted

Press
National Cybersecurity Alliance Kicks-Off 2nd Year of “See Yourself In Cyber” HBCU Career Program
National Cybersecurity Alliance Kicks-Off 2nd Year of “See Yourself In Cyber” HBCU Career Program

Press
Tampa Bay Times: Florida Patients Among Victims of Spate of Data Hacking
Tampa Bay Times: Florida Patients Among Victims of Spate of Data Hacking

Press
Raconteur: Why Gen Z's Lack of Literacy is a Serious Business Risk
Raconteur: Why Gen Z's Lack of Literacy is a Serious Business Risk

Press
BizTech: Elevate Your Ransomware Defenses with a Post Incident Review
BizTech: Elevate Your Ransomware Defenses with a Post Incident Review

Press
Insurance Journal: The Industry Shouldn't Compete on Cybersecurity
Insurance Journal: The Industry Shouldn't Compete on Cybersecurity

Press
BizTech: What Is Active Directory Monitoring and Why Is AD a Target for Hackers?
BizTech: What Is Active Directory Monitoring and Why Is AD a Target for Hackers?

Press
Erie News Now: Keeping the LGBT+ Community Safe Online
Erie News Now: Keeping the LGBT+ Community Safe Online

Press
Engadget: The best password managers for 2023
Engadget: The best password managers for 2023

Press
Dark Reading: Volt Typhoon' Breaks Fresh Ground for China-Backed Cyber Campaigns
Dark Reading: Volt Typhoon' Breaks Fresh Ground for China-Backed Cyber Campaigns

Press
IT Brew: Asked and answered: 'What is the best defense against polymorphic malware?'
IT Brew: Asked and answered: 'What is the best defense against polymorphic malware?'

Press
National Geographic: Practical tips for protecting your data while traveling
National Geographic: Practical tips for protecting your data while traveling

Press
BizTech: How to Measure Your Team’s Email Security Savviness
BizTech: How to Measure Your Team’s Email Security Savviness

Press
The VIP Home Podcast: Top Internet Safety Tips to Keep Your Info Secure at Home
The VIP Home Podcast: Top Internet Safety Tips to Keep Your Info Secure at Home

Press
Infosecurity Magazine: Characterless Security Training Fails to Change User Behavior
Infosecurity Magazine: Characterless Security Training Fails to Change User Behavior

Press
National Cybersecurity Alliance launches HBCU Scholarship Program
National Cybersecurity Alliance launches HBCU Scholarship Program

Press
Technical.ly: Two nonprofits teamed up to offer HBCU tech students $20K in scholarships
Technical.ly: Two nonprofits teamed up to offer HBCU tech students $20K in scholarships

Press
National Cybersecurity Alliance Partners with One In Tech Foundation to Launch HBCU Scholarship Program
National Cybersecurity Alliance Partners with One In Tech Foundation to Launch HBCU Scholarship Program

Press
Cybersecurity Dive: Women in cybersecurity still fight for inclusion despite the talent shortage
Cybersecurity Dive: Women in cybersecurity still fight for inclusion despite the talent shortage

Press
CPO Magazine: Notorious Genesis Dark Web Market Taken Offline by Law Enforcement
CPO Magazine: Notorious Genesis Dark Web Market Taken Offline by Law Enforcement

Press
Washington Post: Watch out for online scams and vulnerabilities this tax season
Washington Post: Watch out for online scams and vulnerabilities this tax season

Press
National Cybersecurity Alliance Joins RSA Conference with a Discussion on Engagement through Entertainment
National Cybersecurity Alliance Joins RSA Conference with a Discussion on Engagement through Entertainment

Press
MAKE USE OF: 5 Kinds of Spyware You Need to Know About
MAKE USE OF: 5 Kinds of Spyware You Need to Know About

Press
Boston Globe: New details on LastPass breach mean it’s time for a new password manager
Boston Globe: New details on LastPass breach mean it’s time for a new password manager

Press
Sahan Journal: Minneapolis Public Schools acknowledges ‘threat actors’ could have accessed district data. Here’s what you need to know to protect yourself
Sahan Journal: Minneapolis Public Schools acknowledges ‘threat actors’ could have accessed district data. Here’s what you need to know to protect yourself

Press
The White House Readout: Office of National Cyber Director Hosts Roundtable on “The State of Cybersecurity in the Black Community”
The White House Readout: Office of National Cyber Director Hosts Roundtable on “The State of Cybersecurity in the Black Community”

Press
To the Point Podcast: So Many Cyber Scams - with Names Like Pig Butchering?! With Jennifer Cook
To the Point Podcast: So Many Cyber Scams - with Names Like Pig Butchering?! With Jennifer Cook

Press
VentureBeat: NCA executive director shares top cybersecurity risks in 2023
VentureBeat: NCA executive director shares top cybersecurity risks in 2023

Press
Help Net Security: Helping users and organizations build an instinctive data privacy habit
Help Net Security: Helping users and organizations build an instinctive data privacy habit

Press
PCMag: Why Tech Companies Are Looking to HBCUs to Expand the Cybersecurity Workforce
PCMag: Why Tech Companies Are Looking to HBCUs to Expand the Cybersecurity Workforce

Press
Tom's Guide: Don’t get burned this Valentine’s Day — these are the scams to look out forTom's Guide:
Tom's Guide: Don’t get burned this Valentine’s Day — these are the scams to look out forTom's Guide:

Press
Washington Post: Romance scammers could cause unhappy Valentine’s Day
Washington Post: Romance scammers could cause unhappy Valentine’s Day

Press
Washington Post: The State of the Union was light on cybersecurity
Washington Post: The State of the Union was light on cybersecurity

Press
IT Brew: Three ways to sell a privacy program to an exec who’s not listening
IT Brew: Three ways to sell a privacy program to an exec who’s not listening

Press
CNBC: How to protect yourself from tax fraud and scams, according to cybersecurity experts
CNBC: How to protect yourself from tax fraud and scams, according to cybersecurity experts

Press
CBS17: Are you a T-Mobile customer? Here’s how to protect yourself against data breaches
CBS17: Are you a T-Mobile customer? Here’s how to protect yourself against data breaches

Press
CyberWire: DragonSpark hits East Asia. ProxyNotShell in the wild. Privacy investment. IoT supply chain threat.
CyberWire: DragonSpark hits East Asia. ProxyNotShell in the wild. Privacy investment. IoT supply chain threat.

Press
TechRepublic: Data Privacy Week 2023 - Virtual events and webinars to attend
TechRepublic: Data Privacy Week 2023 - Virtual events and webinars to attend

Press
Channel Futures: 2023 Cybersecurity Outlook - Newer Targets, Tighter Budgets
Channel Futures: 2023 Cybersecurity Outlook - Newer Targets, Tighter Budgets

Press
VentureBeat: T-Mobile data breach shows API security can’t be ignored
VentureBeat: T-Mobile data breach shows API security can’t be ignored

Press
National Cybersecurity Alliance Announces Program for 2023 Data Privacy Week Campaign
National Cybersecurity Alliance Announces Program for 2023 Data Privacy Week Campaign

Press
T-Mobile January 2023 Data Breach Announcement: What You Should Do
T-Mobile January 2023 Data Breach Announcement: What You Should Do

Press
Reflections on Winter 2023 Convene
Reflections on Winter 2023 Convene

Press
IT Brew: Despite hacks, password managers are still an important SaaS security measure
IT Brew: Despite hacks, password managers are still an important SaaS security measure

Press
SDxCentral: TACKLING TECH’S TALENT SHORTAGE IN 2022
SDxCentral: TACKLING TECH’S TALENT SHORTAGE IN 2022

Press
PCMag: 2023 Could Be a Security Nightmare. Here’s Why
PCMag: 2023 Could Be a Security Nightmare. Here’s Why

Press
Security Intelligence: How to Embed Gen Z in Your Organization’s Security Culture
Security Intelligence: How to Embed Gen Z in Your Organization’s Security Culture

Press
Cyberwire: Updates on the cyber phases of a hybrid war
Cyberwire: Updates on the cyber phases of a hybrid war

Press
Cybernews: How to avoid hacking hangover at the airport this holiday season
Cybernews: How to avoid hacking hangover at the airport this holiday season

Press
AARP: 4 Tips for Talking to Your Kids and Grandkids about Fraud
AARP: 4 Tips for Talking to Your Kids and Grandkids about Fraud

Press
GitHub repojacking attack: 10 lessons for software teams
GitHub repojacking attack: 10 lessons for software teams

Press
Law360: Small Firms Need Cyber Protection As Much As Large Ones
Law360: Small Firms Need Cyber Protection As Much As Large Ones

Press
SpiceWorks: A Defense Playbook for Diffusing CCTV Cybersecurity Threats
SpiceWorks: A Defense Playbook for Diffusing CCTV Cybersecurity Threats

Press
Cyberwire: CISA releases voluntary CPGs. Trojans and scanners. Cyber venture investing, and some insights into corporate culture. "Opportunistic" cyberops in a hybrid war.
Cyberwire: CISA releases voluntary CPGs. Trojans and scanners. Cyber venture investing, and some insights into corporate culture. "Opportunistic" cyberops in a hybrid war.

Press
AiThority: Predictions Series 2022 - Interview with Lisa Plaggemier, Executive Director at National Cybersecurity Alliance
AiThority: Predictions Series 2022 - Interview with Lisa Plaggemier, Executive Director at National Cybersecurity Alliance

Press
Plex breach exposes usernames, emails, and encrypted passwords
Plex breach exposes usernames, emails, and encrypted passwords

Press
Cheddar: U.S. Cable Wake Up with Cheddar
Cheddar: U.S. Cable Wake Up with Cheddar

Press
CNBC: U.S. Cable Squawk on the street
CNBC: U.S. Cable Squawk on the street

Press
The Verge: How to rescue your hacked account: Facebook, Instagram, Snapchat, and more
The Verge: How to rescue your hacked account: Facebook, Instagram, Snapchat, and more

Press
BizTech: How Nonprofits Can Protect Their Donor Data in the Cloud
BizTech: How Nonprofits Can Protect Their Donor Data in the Cloud

Press
Channel Features: Pro-Russian Hacktivist Groups Take Down Numerous U.S. Airport Websites
Channel Features: Pro-Russian Hacktivist Groups Take Down Numerous U.S. Airport Websites

Press
National Cybersecurity Alliance Kicks Off 19th Annual Cybersecurity Awareness Month
National Cybersecurity Alliance Kicks Off 19th Annual Cybersecurity Awareness Month

Press
Beta News: A third of people fall victim to cyberattacks despite training
Beta News: A third of people fall victim to cyberattacks despite training

Press
STUDY: More than One-Third of Tech Users Fell Victim to Phishing Despite Access to Training Geared Towards Identifying Attacks
STUDY: More than One-Third of Tech Users Fell Victim to Phishing Despite Access to Training Geared Towards Identifying Attacks

Press
CRN: Experts At Amazon, Google, Dell - Cybersecurity Begins At Home
CRN: Experts At Amazon, Google, Dell - Cybersecurity Begins At Home

Press
SecureWorld: Cybersecurity Awareness Month Focuses on People
SecureWorld: Cybersecurity Awareness Month Focuses on People

Press
Infosecurity Magazine: Initiative Aims to Encourage Diverse Talent into Cyber
Infosecurity Magazine: Initiative Aims to Encourage Diverse Talent into Cyber

Press
SDX Central: Daily Roundup - Ericsson Releases Power-Efficient 5G Radio
SDX Central: Daily Roundup - Ericsson Releases Power-Efficient 5G Radio

Press
SDX Central: National Cybersecurity Alliance Launches Outreach, Mentorship Program
SDX Central: National Cybersecurity Alliance Launches Outreach, Mentorship Program

Press
The Record: CISA, Dell and more partner for HBCU cybersecurity program
The Record: CISA, Dell and more partner for HBCU cybersecurity program

Press
SC Magazine: National Cybersecurity Alliance launches HBCU career training program
SC Magazine: National Cybersecurity Alliance launches HBCU career training program

Press
National Cybersecurity Alliance Launches HBCU Career Program
National Cybersecurity Alliance Launches HBCU Career Program

Press
Channel Futures: Data Breach Hits Media Streaming Platform
Channel Futures: Data Breach Hits Media Streaming Platform

Press
Washington Post: Twitter has issues keeping your data secure. Here’s what you can do.
Washington Post: Twitter has issues keeping your data secure. Here’s what you can do.

Press
NCA Partners with Amazon on PSA Campaign to Educate Consumers about Online Cyber Threats and Best Practices to Protect Themselves
NCA Partners with Amazon on PSA Campaign to Educate Consumers about Online Cyber Threats and Best Practices to Protect Themselves

Press
AP Archive: Apple issues security warning for iPhones, devices
AP Archive: Apple issues security warning for iPhones, devices

Press
Dark Reading: Patch Now - 2 Apple Zero-Days Exploited in Wild
Dark Reading: Patch Now - 2 Apple Zero-Days Exploited in Wild

Press
Washington Post: Mandatory password updates are passe
Washington Post: Mandatory password updates are passe

Press
Forbes: Coalition Of Cybersecurity Leaders Launch Open Cybersecurity Schema Framework (OCSF)
Forbes: Coalition Of Cybersecurity Leaders Launch Open Cybersecurity Schema Framework (OCSF)

Press
IT Brew: Lazarus attackers mimic job recruiters
IT Brew: Lazarus attackers mimic job recruiters

Press
Morning Brew: Five remote-onboarding tips for IT pros
Morning Brew: Five remote-onboarding tips for IT pros

Press
USA Today: Helping small businesses and rural communities thwart cyberattacks
USA Today: Helping small businesses and rural communities thwart cyberattacks

Press
CPO Magazine: Game Publisher Bandai Namco Confirms a Suspected BlackCat Ransomware Attack
CPO Magazine: Game Publisher Bandai Namco Confirms a Suspected BlackCat Ransomware Attack

Press
Washington Post: Howard University cancels online, hybrid classes as it investigates alleged ransomware attack
Washington Post: Howard University cancels online, hybrid classes as it investigates alleged ransomware attack

Press
CyberWire: New hack de-anonymizes website users
CyberWire: New hack de-anonymizes website users

Press
Silicon Angle: Japanese video game publisher Bandai Namco targeted in ransomware attack
Silicon Angle: Japanese video game publisher Bandai Namco targeted in ransomware attack

Press
Street Fight Magazine: Retailers Prepare for Increased Cyber Attacks During Prime Day
Street Fight Magazine: Retailers Prepare for Increased Cyber Attacks During Prime Day

Press
The National Cybersecurity Alliance Named to CSO50
The National Cybersecurity Alliance Named to CSO50

Press
National Cybersecurity Alliance Named to CSO50
National Cybersecurity Alliance Named to CSO50

Press
Medscape: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks
Medscape: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks

Press
Get Involved In Identity Management Day
Get Involved In Identity Management Day

Press
Reader's Digest: How to Spot a Fake QR Code and Avoid Getting Scammed
Reader's Digest: How to Spot a Fake QR Code and Avoid Getting Scammed
Press
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy

Press
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity

Press
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity
National Cybersecurity Alliance Joins RSA Conference with a Discussion on A Whole Lotta BS (Behavioral Science) About Cybersecurity

Press
The Register: Biden signs cybercrime tracking bill into law
The Register: Biden signs cybercrime tracking bill into law

Press
National Cyber Security Alliance Statement Regarding Incorrect Small Business Statistic
National Cyber Security Alliance Statement Regarding Incorrect Small Business Statistic

Press
Forbes: Biden Signs Bill To Create Cybercrime Reporting System
Forbes: Biden Signs Bill To Create Cybercrime Reporting System

Press
News Radio 1120 KMOX: Stop writing down passwords
News Radio 1120 KMOX: Stop writing down passwords

Press
CSO: Meta, Apple emergency data request scam holds lessons for CISOs
CSO: Meta, Apple emergency data request scam holds lessons for CISOs

Press
Technical.ly: 5 reasons to consider a cybersecurity career in 2022
Technical.ly: 5 reasons to consider a cybersecurity career in 2022

Press
CSO: U.S. State Department unveils new Bureau of Cyberspace and Digital Policy
CSO: U.S. State Department unveils new Bureau of Cyberspace and Digital Policy

Press
Channel Futures: The Gately Report - Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022
Channel Futures: The Gately Report - Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022

Press
Channel Futures: Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022
Channel Futures: Malwarebytes Plans ‘Explosive’ Partner Community Growth in 2022

Press
Channel Futures: FCC Says Kaspersky Software Poses National Security Threat
Channel Futures: FCC Says Kaspersky Software Poses National Security Threat

Press
The Cyberwire: Russia's hybrid war with Ukraine: strategy, norms, and alliances
The Cyberwire: Russia's hybrid war with Ukraine: strategy, norms, and alliances

Press
Washington Post: Want to avoid a cyberattack? Stop ignoring those pesky software updates.
Washington Post: Want to avoid a cyberattack? Stop ignoring those pesky software updates.

Press
MarketWatch: The prospect of more Russian cyberattacks seems increasingly likely. What can you do to protect yourself? Quite a lot, it turns out.
MarketWatch: The prospect of more Russian cyberattacks seems increasingly likely. What can you do to protect yourself? Quite a lot, it turns out.

Press
CSO: NIST seeks information on updating its Cybersecurity Framework
CSO: NIST seeks information on updating its Cybersecurity Framework

Press
Washington Post: The Online Security Reset Guide: Keeping you safe from scammers, hackers and digital threats
Washington Post: The Online Security Reset Guide: Keeping you safe from scammers, hackers and digital threats

Press
Gov Info Security: Ukrainian Government Prepared to Wipe Servers
Gov Info Security: Ukrainian Government Prepared to Wipe Servers

Press
American Banker: Ransomware attacks are rising, payment security consortium warns
American Banker: Ransomware attacks are rising, payment security consortium warns

Press
Techspective: Lisa Plaggemier Discusses Cybersecurity at the Winter Olympics
Techspective: Lisa Plaggemier Discusses Cybersecurity at the Winter Olympics

Press
Well+Good: How To Spot a Scammer and Protect Yourself From Them, According to a Relationship Therapist and Cyber Security Expert
Well+Good: How To Spot a Scammer and Protect Yourself From Them, According to a Relationship Therapist and Cyber Security Expert

Press
AdWeek: How QR Codes Made Waves at the 2022 Super Bowl
AdWeek: How QR Codes Made Waves at the 2022 Super Bowl

Press
Media Post: 83.4 Million U.S. Smartphone Users Will Scan QR Codes This Year
Media Post: 83.4 Million U.S. Smartphone Users Will Scan QR Codes This Year

Press
PC Magazine: Coinbase's Mystery QR Code Super Bowl Ad Is a Security Nightmare
PC Magazine: Coinbase's Mystery QR Code Super Bowl Ad Is a Security Nightmare

Press
Gov Info Security: US SEC Proposes 48-Hour Incident Reporting Requirement
Gov Info Security: US SEC Proposes 48-Hour Incident Reporting Requirement

Press
Axios: Watch A conversation on internet safety in the modern digital era
Axios: Watch A conversation on internet safety in the modern digital era

Press
Broad and Breakfast: Companies Should Mandate Two-Factor Authentication, Says Head of National Cybersecurity Alliance
Broad and Breakfast: Companies Should Mandate Two-Factor Authentication, Says Head of National Cybersecurity Alliance

Press
Digital Anarchist: Data Privacy Week – Lisa Plaggemier, National Cyber Security Alliance
Digital Anarchist: Data Privacy Week – Lisa Plaggemier, National Cyber Security Alliance

Press
Inside the Games: Lisa Plaggemier - After Pyeongchang 2018 cyberattack, will Beijing 2022 be safe and secure?
Inside the Games: Lisa Plaggemier - After Pyeongchang 2018 cyberattack, will Beijing 2022 be safe and secure?

Press
Database Trends: Data Privacy Day 2022 - Industry Leaders Reflect on the Current State of Data Security
Database Trends: Data Privacy Day 2022 - Industry Leaders Reflect on the Current State of Data Security

Press
SD Times: The NCSA expands annual Data Privacy Day into Data Privacy Week
SD Times: The NCSA expands annual Data Privacy Day into Data Privacy Week

Press
Tech and Science Daily Podcast: Samsung's new Galaxy S22 - What to expect
Tech and Science Daily Podcast: Samsung's new Galaxy S22 - What to expect

Press
Auto Remarketing: KAR licenses privacy & security training program to NAAA-member auctions
Auto Remarketing: KAR licenses privacy & security training program to NAAA-member auctions

Press
Fox News: It's Data Privacy Week—here are some tips on staying safe while online
Fox News: It's Data Privacy Week—here are some tips on staying safe while online

Press
KMOX: Expert - Protecting your data can make a 'massive dent' in cybercrime
KMOX: Expert - Protecting your data can make a 'massive dent' in cybercrime

Press
Washington Post: Cyber fears mount amid prospect of Russian invasion of Ukraine
Washington Post: Cyber fears mount amid prospect of Russian invasion of Ukraine

Press
FOX NEWS: Online security and privacy is easy, not complicated
FOX NEWS: Online security and privacy is easy, not complicated
Press
National Cybersecurity Alliance Announces Program for Data Privacy Week
National Cybersecurity Alliance Announces Program for Data Privacy Week

Press
SECURITY BOULEVARD: FCC Proposes Stricter Regulations for Data Breach Disclosure
SECURITY BOULEVARD: FCC Proposes Stricter Regulations for Data Breach Disclosure

Press
SECURITY BOULEVARD: Why 2022 Should be a Year of Cybersecurity Optimism
SECURITY BOULEVARD: Why 2022 Should be a Year of Cybersecurity Optimism

Press
Why 2022 Is the Year of the Password Manager
Why 2022 Is the Year of the Password Manager

Press
CHANNEL FUTURES: 2022 Cybersecurity Predictions: Even More Reasonware, But Reason for Optimism
CHANNEL FUTURES: 2022 Cybersecurity Predictions: Even More Reasonware, But Reason for Optimism

Press
CSO: Security leaders on how to cope with stress of Log4j
CSO: Security leaders on how to cope with stress of Log4j

Press
Dark Reading: Meta Files Federal Lawsuit Against Phishing Operators
Dark Reading: Meta Files Federal Lawsuit Against Phishing Operators

Press
Channel Futures: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks
Channel Futures: Global Unrest, Pandemic Challenges Spurring Healthcare Cyberattacks

Press
Gov Info Security: US, Allies to Tighten Export Controls on Cyber Tools
Gov Info Security: US, Allies to Tighten Export Controls on Cyber Tools

Press
Politico: Washington’s cybersecurity wish list for 2022
Politico: Washington’s cybersecurity wish list for 2022

Press
Spiceworks: Tackling the Cybersecurity Talent Gap: 4 Tips for Employers
Spiceworks: Tackling the Cybersecurity Talent Gap: 4 Tips for Employers

Press
The Stevie® Awards: Honoring Excellence in Business Worldwide
The Stevie® Awards: Honoring Excellence in Business Worldwide

Press
KKTV: Don’t let grinches steal Christmas! How to stay safe when holiday shopping
KKTV: Don’t let grinches steal Christmas! How to stay safe when holiday shopping

Press
Security Boulevard: US, EU Join Paris Call for Cybersecurity
Security Boulevard: US, EU Join Paris Call for Cybersecurity

Press
Bank Info Security: VP Kamala Harris: US Will Join 80-Nation Cybersecurity Pact
Bank Info Security: VP Kamala Harris: US Will Join 80-Nation Cybersecurity Pact

Press
USA Today: After 7 million impacted in Robinhood data breach, experts offer some tips for amateur investors
USA Today: After 7 million impacted in Robinhood data breach, experts offer some tips for amateur investors

Press
Fast Company Robinhood data breach - Here’s what stock traders who use the platform need to know
Fast Company Robinhood data breach - Here’s what stock traders who use the platform need to know

Press
Gov Info Security: Infrastructure Bill Features $1.9 Billion in Cyber Funding
Gov Info Security: Infrastructure Bill Features $1.9 Billion in Cyber Funding

Press
Ping: How to Be Cyber Smart this Cybersecurity Awareness Month
Ping: How to Be Cyber Smart this Cybersecurity Awareness Month

Press
NBC: How to Keep Children Safe From Online Scams, Identity Theft
NBC: How to Keep Children Safe From Online Scams, Identity Theft

Press
State Scoop: It’s October. Are you aware of cybersecurity yet?
State Scoop: It’s October. Are you aware of cybersecurity yet?

Press
RBR: The InFOCUS Podcast - National Cybersecurity Alliance
RBR: The InFOCUS Podcast - National Cybersecurity Alliance

Press
EdTech: Next-Generation Firewall and IPSs Offer Proactive Protection for Higher Ed Networks
EdTech: Next-Generation Firewall and IPSs Offer Proactive Protection for Higher Ed Networks

Press
Light Reading: Sinclair hit by ransomware attack
Light Reading: Sinclair hit by ransomware attack

Press
NBC: Authorities See Rise in Ransomware Attacks, Urge Businesses to Prioritize Cybersecurity
NBC: Authorities See Rise in Ransomware Attacks, Urge Businesses to Prioritize Cybersecurity

Press
Bank Info Security: US Agencies to Water Facilities - You May Be Next Target
Bank Info Security: US Agencies to Water Facilities - You May Be Next Target

Press
Best Practices for People and Enterprise to #StaySafeOnline
Best Practices for People and Enterprise to #StaySafeOnline

Press
Gov Info Security: CISA to Access Agencies' Endpoints, Help Enhance Security
Gov Info Security: CISA to Access Agencies' Endpoints, Help Enhance Security

Press
NBC: Top 5 Things You Should Be Doing to Keep Your Information Safe Online
NBC: Top 5 Things You Should Be Doing to Keep Your Information Safe Online

Press
Security Boulevard: Public’s Knowledge of Cybersecurity Best Practices Sorely Lacking
Security Boulevard: Public’s Knowledge of Cybersecurity Best Practices Sorely Lacking

Press
Beta News: Highlighting the cybersecurity generation gap
Beta News: Highlighting the cybersecurity generation gap

Press
NBC: #BeCyberSmart - The Rise of Online Scams
NBC: #BeCyberSmart - The Rise of Online Scams

Press
Venture Beat: Cyberattacks are getting worse, but most people aren’t taking basic security steps
Venture Beat: Cyberattacks are getting worse, but most people aren’t taking basic security steps

Press
Venture Beat: It’s Cybersecurity Awareness Month. Does your business have a viable plan yet?
Venture Beat: It’s Cybersecurity Awareness Month. Does your business have a viable plan yet?

Press
STUDY: Millennials and Gen Z Say They are Bigger Victims of Cybercrime
STUDY: Millennials and Gen Z Say They are Bigger Victims of Cybercrime

Press
National Cyber Security Alliance Kicks Off 18th Annual Cybersecurity Awareness Month
National Cyber Security Alliance Kicks Off 18th Annual Cybersecurity Awareness Month

Press
Forensics: CYBERSECURITY AWARENESS MONTH 2021 - AN EXPERT’S ADVOCACY GUIDE
Forensics: CYBERSECURITY AWARENESS MONTH 2021 - AN EXPERT’S ADVOCACY GUIDE

Press
CBS: Apple says its security flaw was fixed. Cyber analysts warn zero-click threats will persist.
CBS: Apple says its security flaw was fixed. Cyber analysts warn zero-click threats will persist.

Press
The Learning Counsel: How To Safeguard Schools Against Cyber Attacks this School Year
The Learning Counsel: How To Safeguard Schools Against Cyber Attacks this School Year

Press
Venture Beat: Why cyber scare tactics have missed the mark
Venture Beat: Why cyber scare tactics have missed the mark

Press
Healthcare IT News: FBI, CISA warn: Hackers won't take a vacation
Healthcare IT News: FBI, CISA warn: Hackers won't take a vacation

Press
The Cyberwire: WhatsApp patches bug. Twitter updates its features to promote “social privacy.” Labor Day threats to data privacy.
The Cyberwire: WhatsApp patches bug. Twitter updates its features to promote “social privacy.” Labor Day threats to data privacy.

Press
Channel Futures: Hackers Again Setting Sights on Microsoft Exchange Vulnerabilities
Channel Futures: Hackers Again Setting Sights on Microsoft Exchange Vulnerabilities

Press
TDWI: How Organizations Can Stay Protected Online
TDWI: How Organizations Can Stay Protected Online

Press
Bank Info Security: World Bank Launches Global Cybersecurity Fund
Bank Info Security: World Bank Launches Global Cybersecurity Fund

Press
Techinal.ly: Resource Roundup: Level up in cyber, IT and entrepreneurship with these 4 DC-area programs
Techinal.ly: Resource Roundup: Level up in cyber, IT and entrepreneurship with these 4 DC-area programs

Press
Cyber Magazine: National Cyber Security Alliance to launch new resource bank
Cyber Magazine: National Cyber Security Alliance to launch new resource bank

Press
Washington Post: The Cybersecurity 202: There was another massive data breach. People will probably forget it in a week.
Washington Post: The Cybersecurity 202: There was another massive data breach. People will probably forget it in a week.

Press
SC Magazine: NCSA creates cyber career resource library to educate our future infosec workforce
SC Magazine: NCSA creates cyber career resource library to educate our future infosec workforce

Press
Security Magazine: National Cyber Security Alliance launches new cyber initiative
Security Magazine: National Cyber Security Alliance launches new cyber initiative

Press
National Cyber Security Alliance Unveils Cybersecurity Education and Career Resource Library
National Cyber Security Alliance Unveils Cybersecurity Education and Career Resource Library

Press
Cybersecurity Dive: How the $1.2 trillion infrastructure bill invests in cyber
Cybersecurity Dive: How the $1.2 trillion infrastructure bill invests in cyber

Press
Gov Info Security: OMB Spells Out Agencies' Cybersecurity Timelines
Gov Info Security: OMB Spells Out Agencies' Cybersecurity Timelines

Press
CIO Dive: Preparedness, checklists, leadership buy-in - How to build a rapid IT response
CIO Dive: Preparedness, checklists, leadership buy-in - How to build a rapid IT response

Press
Gov Info Security: Patching Woes: Most Frequently Exploited CVEs Listed
Gov Info Security: Patching Woes: Most Frequently Exploited CVEs Listed

Press
What the Dev? Cybersecurity and the Tokyo Olympics - Episode 113
What the Dev? Cybersecurity and the Tokyo Olympics - Episode 113

Press
Fox: Tokyo Olympics could be threatened by cyberattack, FBI warns
Fox: Tokyo Olympics could be threatened by cyberattack, FBI warns

Press
Channel Futures: Tokyo Olympics Contending with Cyber Threats, FBI Warns of More Coming
Channel Futures: Tokyo Olympics Contending with Cyber Threats, FBI Warns of More Coming

Press
Threat Post: Indictments, Attribution Unlikely to Deter Chinese Hacking, Researchers Say
Threat Post: Indictments, Attribution Unlikely to Deter Chinese Hacking, Researchers Say

Press
Auto Remarketing: National Cyber Security Alliance on trends in automotive
Auto Remarketing: National Cyber Security Alliance on trends in automotive
Press
National Cyber Security Alliance Announces Leadership Transition
National Cyber Security Alliance Announces Leadership Transition

Press
Law 360: Kaseya Ransomware Hit Casts Wide Net Of Potential Liability
Law 360: Kaseya Ransomware Hit Casts Wide Net Of Potential Liability

Press
Bloomberg: Kaseya Software Hack Highlights Small Business Security Squeeze
Bloomberg: Kaseya Software Hack Highlights Small Business Security Squeeze

Press
Washington Post: The Cybersecurity 202: The Kaseya attack is a revolution in sophistication for ransomware hackers
Washington Post: The Cybersecurity 202: The Kaseya attack is a revolution in sophistication for ransomware hackers

Press
Auto News: Ransomware attacks could crimp industry’s recovery from pandemic, report says
Auto News: Ransomware attacks could crimp industry’s recovery from pandemic, report says

Press
Healthcare Info Security: Battling Ongoing COVID-19-Themed Attacks and Scams
Healthcare Info Security: Battling Ongoing COVID-19-Themed Attacks and Scams

Press
Digital Anarchist: Cybersecurity Safety Review Board – Kelvin Coleman, NCSA
Digital Anarchist: Cybersecurity Safety Review Board – Kelvin Coleman, NCSA

Press
WSJ: Hackers Stole $650,000 From Nonprofit and Got Away, Showing Limits to Law Enforcement’s Reach
WSJ: Hackers Stole $650,000 From Nonprofit and Got Away, Showing Limits to Law Enforcement’s Reach

Press
NBC: Who's in charge here? Colonial Pipeline hack exposes huge holes in U.S. cyber defenses, say experts
NBC: Who's in charge here? Colonial Pipeline hack exposes huge holes in U.S. cyber defenses, say experts

Press
Channel Futures: Significant Ramifications
Channel Futures: Significant Ramifications

Press
Ed Tech: To Improve Higher Ed Data Security, Address These Risks in Research Projects
Ed Tech: To Improve Higher Ed Data Security, Address These Risks in Research Projects

Press
Endpoint: Why We Still Need World Password Day
Endpoint: Why We Still Need World Password Day

Press
Health IT Security: Google Sued, Lawsuit Claims COVID-19 Contact Tracing Tool Exposes Data
Health IT Security: Google Sued, Lawsuit Claims COVID-19 Contact Tracing Tool Exposes Data

Press
Associations Now: Spring Clean Your Digital Files
Associations Now: Spring Clean Your Digital Files

Press
Hacked.com: Why Every Business Should Train Employees to Spot Phishing Emails
Hacked.com: Why Every Business Should Train Employees to Spot Phishing Emails

Press
TechTarget: SolarWinds puts national cybersecurity strategy on display
TechTarget: SolarWinds puts national cybersecurity strategy on display

Press
Hacked.com: The Top 5 Reasons Hackers Might Target Your Small Business
Hacked.com: The Top 5 Reasons Hackers Might Target Your Small Business

Press
Martech Series: Beyond Identity Integration With Auth0 Enables Completely Passwordless Authentication
Martech Series: Beyond Identity Integration With Auth0 Enables Completely Passwordless Authentication

Press
SC Magazine: On first-ever Identity Management Day, experts detail steps to a better IAM program
SC Magazine: On first-ever Identity Management Day, experts detail steps to a better IAM program

Press
Dark Reading: Biden Nominates Former NSA Officials for Top Cybersecurity Roles
Dark Reading: Biden Nominates Former NSA Officials for Top Cybersecurity Roles

Press
WSJ: Biden Administration Announces National Cyber, CISA Director Nominations
WSJ: Biden Administration Announces National Cyber, CISA Director Nominations

Press
Accounting Today: IRS and COVID vaccine email scams proliferating this tax season
Accounting Today: IRS and COVID vaccine email scams proliferating this tax season

Press
Healthcare IT News: How cybercriminals exploit COVID-19, and how to protect against them
Healthcare IT News: How cybercriminals exploit COVID-19, and how to protect against them

Press
Security Magazine: 5 minutes with Kelvin Coleman - Remote learning and data privacy issues
Security Magazine: 5 minutes with Kelvin Coleman - Remote learning and data privacy issues

Press
Gov Info Security: Exchange Hacks: How Will the Biden Administration Respond?
Gov Info Security: Exchange Hacks: How Will the Biden Administration Respond?

Press
Above the Law: Keeping Your Data Safe In The Remote Work Era
Above the Law: Keeping Your Data Safe In The Remote Work Era

Press
The Cyberwire: Patching, with special attention to Hafnium and the rest. Responding to the SolarWinds incident. Hactivists don’t like cameras. Dragnet in the Low Countries.
The Cyberwire: Patching, with special attention to Hafnium and the rest. Responding to the SolarWinds incident. Hactivists don’t like cameras. Dragnet in the Low Countries.

Press
Health Leaders Media: NCSA ON CYBERSECURITY: 'UPDATE, UPDATE, UPDATE'
Health Leaders Media: NCSA ON CYBERSECURITY: 'UPDATE, UPDATE, UPDATE'

Press
MedCity News: When it comes to healthcare cybersecurity, the best defense is also the most simple
MedCity News: When it comes to healthcare cybersecurity, the best defense is also the most simple

Press
Washington Post: The Cybersecurity 202: Scammers are already targeting the next round of coronavirus relief checks
Washington Post: The Cybersecurity 202: Scammers are already targeting the next round of coronavirus relief checks

Press
Healthcare Info Security: Fraudsters Devise More COVID-19 Vaccine Schemes
Healthcare Info Security: Fraudsters Devise More COVID-19 Vaccine Schemes

Press
CIO Dive: Legacy tech, privacy and security issues bog down healthcare innovation
CIO Dive: Legacy tech, privacy and security issues bog down healthcare innovation

Press
Identity Defined Security Alliance Partners with National Cyber Security Alliance to Launch First-Ever ‘Identity Management Day’ April 13, 2021
Identity Defined Security Alliance Partners with National Cyber Security Alliance to Launch First-Ever ‘Identity Management Day’ April 13, 2021

Press
CNET: Apple AirTags: How to Protect Yourself From Being Tracked
CNET: Apple AirTags: How to Protect Yourself From Being Tracked

Press
FedTech Magazine: The Importance of Supply Chain Risk Management in Government
FedTech Magazine: The Importance of Supply Chain Risk Management in Government

Press
NBC: Fraud Investigations Holding Up Unemployment Payments
NBC: Fraud Investigations Holding Up Unemployment Payments

Press
WSJ: U.S. Water Supply Has Few Protections Against Hacking
WSJ: U.S. Water Supply Has Few Protections Against Hacking

Press
Digital Anarchist: Kelvin Coleman – TechStrong TV
Digital Anarchist: Kelvin Coleman – TechStrong TV

Press
HealthTech Magazine: How to Keep Telehealth Secure
HealthTech Magazine: How to Keep Telehealth Secure

Press
SDX Central: Is Biden’s $10B Enough to Make US Cybersecurity Great Again?
SDX Central: Is Biden’s $10B Enough to Make US Cybersecurity Great Again?

Press
Datanami: Data Privacy in the Crosshairs
Datanami: Data Privacy in the Crosshairs

Press
SC Magazine: Speed of White House cyber appointments should make CISOs ‘a bit more confident’
SC Magazine: Speed of White House cyber appointments should make CISOs ‘a bit more confident’

Press
National Cyber Security Alliance Kicks off Data Privacy Day This Week to Raise Awareness for Responsible Data Privacy Practices
National Cyber Security Alliance Kicks off Data Privacy Day This Week to Raise Awareness for Responsible Data Privacy Practices

Press
Protocol: Why an ‘internet blackout’ probably isn’t coming on inauguration day
Protocol: Why an ‘internet blackout’ probably isn’t coming on inauguration day

Press
SC Magazine: Free cyber career training coursework emerges as a perk in tough times
SC Magazine: Free cyber career training coursework emerges as a perk in tough times

Press
Digital Anarchist: TechStrong TV – January 14, 2021
Digital Anarchist: TechStrong TV – January 14, 2021

Press
Security Boulevard: Data Privacy Day - Understanding COVID-19’s Impact
Security Boulevard: Data Privacy Day - Understanding COVID-19’s Impact

Press
GCN: IT cleanup at U.S. Capitol presents massive challenge
GCN: IT cleanup at U.S. Capitol presents massive challenge

Press
Security Week: Experts Weigh In on Cybersecurity Risks of Capitol-Like Attacks
Security Week: Experts Weigh In on Cybersecurity Risks of Capitol-Like Attacks

Press
TidBITS: Cybersecurity Ramifications of the 2021 Storming of the United States Capitol
TidBITS: Cybersecurity Ramifications of the 2021 Storming of the United States Capitol

Press
Wired: Post-Riot, the Capitol Hill IT Staff Faces a Security Mess
Wired: Post-Riot, the Capitol Hill IT Staff Faces a Security Mess

Press
Channel Futures: US Capitol Rioters Pose Cybersecurity Threat Due to Device Access, Theft
Channel Futures: US Capitol Rioters Pose Cybersecurity Threat Due to Device Access, Theft

Press
Data Center Knowledge: What Data Center IT Security Pros Must Know About the SolarWinds Vulnerability
Data Center Knowledge: What Data Center IT Security Pros Must Know About the SolarWinds Vulnerability

Press
In wake of SolarWinds hack, here are the critical responses required of all businesses
In wake of SolarWinds hack, here are the critical responses required of all businesses

Press
Tech Targets: Cybersecurity employee training: How to build a solid plan
Tech Targets: Cybersecurity employee training: How to build a solid plan

Press
The Hill: Scammers step up efforts to target older Americans during pandemic
The Hill: Scammers step up efforts to target older Americans during pandemic

Press
Digital Trends: The digital switch that blocks all websites from selling your personal data
Digital Trends: The digital switch that blocks all websites from selling your personal data

Press
Faith, Health & Home Podcast: How to Keep Your Family Safe Online | Kelvin Coleman, Exec. Director, Nat'l Cyber Security Alliance
Faith, Health & Home Podcast: How to Keep Your Family Safe Online | Kelvin Coleman, Exec. Director, Nat'l Cyber Security Alliance

Press
Bank Info Security: APT Groups Target Firms Working on COVID-19 Vaccines
Bank Info Security: APT Groups Target Firms Working on COVID-19 Vaccines

Press
Forbes: 6 Cybersecurity Tips When You Work From Home
Forbes: 6 Cybersecurity Tips When You Work From Home

Press
Barracuda: Age plays a role in end-user security training
Barracuda: Age plays a role in end-user security training

Press
Dark Reading: 7 Online Shopping Tips for the Holidays
Dark Reading: 7 Online Shopping Tips for the Holidays

Press
The Daily Swig: Europol campaign urges e-commerce retailers to #SellSafe this Black Friday
The Daily Swig: Europol campaign urges e-commerce retailers to #SellSafe this Black Friday

Press
Healthcare IT News: Hospitals said to tighten email security in response to CEO spear phishing attempts
Healthcare IT News: Hospitals said to tighten email security in response to CEO spear phishing attempts

Press
Dark Reading: Online Users Feel Safe, But Risky Behavior Abounds
Dark Reading: Online Users Feel Safe, But Risky Behavior Abounds

Press
Healthcare IT News: NCSA Confidence in security of connected devices often misplaced
Healthcare IT News: NCSA Confidence in security of connected devices often misplaced

Press
The Cyberwire: CISA says no evidence of successful foreign election hacks. QBot’s voting-themed malspam. RegretLocker arriving.
The Cyberwire: CISA says no evidence of successful foreign election hacks. QBot’s voting-themed malspam. RegretLocker arriving.

Press
24x7 Magazine: 81% of Americans Highly Confident Connected Devices Secure Despite Overlooking Basic Security Hygiene
24x7 Magazine: 81% of Americans Highly Confident Connected Devices Secure Despite Overlooking Basic Security Hygiene

Press
Beta News: Consumers overconfident of their connected device security
Beta News: Consumers overconfident of their connected device security

Press
Infosecurity Magazine: Americans Confident in IoT Device Security
Infosecurity Magazine: Americans Confident in IoT Device Security

Press
SC Magazine: New data shows just how badly home users overestimate IoT security
SC Magazine: New data shows just how badly home users overestimate IoT security

Press
Dot Med: Five minutes in healthcare - featuring Kelvin Coleman
Dot Med: Five minutes in healthcare - featuring Kelvin Coleman

Press
Security Boulevard: U.S. Health Care Under Attack
Security Boulevard: U.S. Health Care Under Attack

Press
Healthcare IT Today: Government Agencies Warn of Imminent Cybercrime Threat from Ransomware Targeted at Hospitals
Healthcare IT Today: Government Agencies Warn of Imminent Cybercrime Threat from Ransomware Targeted at Hospitals

Press
The Cyberwire: Ransomware versus patient medical data. Patching and updating. A new loader in town.
The Cyberwire: Ransomware versus patient medical data. Patching and updating. A new loader in town.

Press
Health Leaders Media: CISA, FBI, HHS WARN HOSPITALS OF 'INCREASED AND IMMINENT' CYBERCRIME THREAT
Health Leaders Media: CISA, FBI, HHS WARN HOSPITALS OF 'INCREASED AND IMMINENT' CYBERCRIME THREAT

Press
Health IT Answers: The Future of Connected Devices
Health IT Answers: The Future of Connected Devices

Press
Health IT Security: Phishing Campaigns Mimic Microsoft Teams, HHS COVID-19 Vaccine Tracker
Health IT Security: Phishing Campaigns Mimic Microsoft Teams, HHS COVID-19 Vaccine Tracker

Press
Healthcare Info Security: COVID-19 Growing Cybersecurity Risks
Healthcare Info Security: COVID-19 Growing Cybersecurity Risks

Press
Health IT Security: Rapid Threat Evolution Spurs Crucial Healthcare Cybersecurity Needs
Health IT Security: Rapid Threat Evolution Spurs Crucial Healthcare Cybersecurity Needs

Press
Spiceworks: How SMBs Can Stay on Top of the Evolving Threat Landscape
Spiceworks: How SMBs Can Stay on Top of the Evolving Threat Landscape

Press
Forbes: Communicate With Confidence Through A Cyber Crisis
Forbes: Communicate With Confidence Through A Cyber Crisis

Press
Healthcare Info Security: Cybersecurity Advice for the COVID-19 Era
Healthcare Info Security: Cybersecurity Advice for the COVID-19 Era

Press
Dark Reading:A 7-Step Cybersecurity Plan for Healthcare Organizations
Dark Reading:A 7-Step Cybersecurity Plan for Healthcare Organizations

Press
ABC: Computer security expert shares tips on staying safe amid surge in cybercrime
ABC: Computer security expert shares tips on staying safe amid surge in cybercrime

Press
Tech Republic: 3 ways criminals use artificial intelligence in cybersecurity attacks
Tech Republic: 3 ways criminals use artificial intelligence in cybersecurity attacks

Press
TechTarget: Healthcare cybersecurity needs a dose of threat modeling
TechTarget: Healthcare cybersecurity needs a dose of threat modeling

Press
Infosecurity Magazine: #NCSAM: Is Connected Ever Going to be Protected?
Infosecurity Magazine: #NCSAM: Is Connected Ever Going to be Protected?

Press
The Cyberwire: Cyber conflict in the Caucasus. Zerologon exploited in the wild. Emotet rising. Silicon Valley’s Gilded Age?
The Cyberwire: Cyber conflict in the Caucasus. Zerologon exploited in the wild. Emotet rising. Silicon Valley’s Gilded Age?

Press
Cybersecurity Awareness Month Around The World | Bangladesh, Canada, And Central/South America | With Kazi Mustafiz, Christine Menard, and Gabriela Montes de Oca Fehr
Cybersecurity Awareness Month Around The World | Bangladesh, Canada, And Central/South America | With Kazi Mustafiz, Christine Menard, and Gabriela Montes de Oca Fehr

Press
Nextgov: CISA Leader Puts Health Sector Project on the Level of Election Security Initiative
Nextgov: CISA Leader Puts Health Sector Project on the Level of Election Security Initiative
Press
Washington Post: The Cybersecurity 202: Americans are as insecure as ever on the 17th annual Cybersecurity Awareness month
Washington Post: The Cybersecurity 202: Americans are as insecure as ever on the 17th annual Cybersecurity Awareness month

Press
It Is Cybersecurity Awareness Month | A Chat With NCSA And CISA To Learn What Is New This Year | With Kelvin Coleman, Brandon Wales, And Lisa Plaggemier
It Is Cybersecurity Awareness Month | A Chat With NCSA And CISA To Learn What Is New This Year | With Kelvin Coleman, Brandon Wales, And Lisa Plaggemier

Press
Data Breach Today: Incident Response: Taking a More Deliberate Approach
Data Breach Today: Incident Response: Taking a More Deliberate Approach

Press
Dark Reading: 7 Summer Travel Security Tips
Dark Reading: 7 Summer Travel Security Tips

Press
Security Week: Industry Reactions to Twitter Hack - Feedback Friday
Security Week: Industry Reactions to Twitter Hack - Feedback Friday

Press
USA Today: 'Tweet-tastrophe'? It could have been. Twitter hack reveals national security threat before election
USA Today: 'Tweet-tastrophe'? It could have been. Twitter hack reveals national security threat before election

Press
IT Ops Times: Twitter attack highlights the need for security awareness training
IT Ops Times: Twitter attack highlights the need for security awareness training

Press
Threat Post: Twitter Confirms it Was Hacked in an Unprecedented Cryptocurrency Scam
Threat Post: Twitter Confirms it Was Hacked in an Unprecedented Cryptocurrency Scam

Press
Bank Info Security: Several Prominent Twitter Accounts Hijacked in Cryptocurrency Scam
Bank Info Security: Several Prominent Twitter Accounts Hijacked in Cryptocurrency Scam

Press
SD Times: Contact tracing apps need to establish trust to be effective
SD Times: Contact tracing apps need to establish trust to be effective

Press
Politico: CISA funding bill, EAC hearing on 2020 primary woes on slate this week
Politico: CISA funding bill, EAC hearing on 2020 primary woes on slate this week

Press
Channel Futures: Tech Startups Hemorrhaging Jobs During Pandemic
Channel Futures: Tech Startups Hemorrhaging Jobs During Pandemic

Press
Politico: Early Covid-19 tracking apps easy prey for hackers, and it might get worse before it gets better
Politico: Early Covid-19 tracking apps easy prey for hackers, and it might get worse before it gets better

Press
Tech Republic: Be prepared: Why you need an incident response policy
Tech Republic: Be prepared: Why you need an incident response policy

Press
CNBC: CLEAR is poised to lead the multibillion-dollar biometric screening race for the coronavirus
CNBC: CLEAR is poised to lead the multibillion-dollar biometric screening race for the coronavirus

Press
ABC: Criminals are pretending to be the government, World Health Organization; here's what to watch out for
ABC: Criminals are pretending to be the government, World Health Organization; here's what to watch out for

Press
Health IT Security: COVID-19 Contact Tracing Apps Spotlight Privacy, Security Rights
Health IT Security: COVID-19 Contact Tracing Apps Spotlight Privacy, Security Rights

Press
NCSA Announces Partnership with National White Collar Crime Center
NCSA Announces Partnership with National White Collar Crime Center

Press
Digital Trends: Contact-tracing apps may seem like the coronavirus solution. They’re not
Digital Trends: Contact-tracing apps may seem like the coronavirus solution. They’re not

Press
CNBC: Utah has rejected the Apple-Google approach to tracing coronavirus, and is using an app made by a social media start-up instead
CNBC: Utah has rejected the Apple-Google approach to tracing coronavirus, and is using an app made by a social media start-up instead

Press
Dark Reading: 7 Ways Parents Can Better Protect Their Online-Gamer Offspring
Dark Reading: 7 Ways Parents Can Better Protect Their Online-Gamer Offspring

Press
Built In: How Healthcare Cybersecurity Is Affected by the Coronavirus Pandemic
Built In: How Healthcare Cybersecurity Is Affected by the Coronavirus Pandemic

Press
National Cyber Security Alliance Encourages Vigilance Against Coronavirus Scams, Best Cybersecurity Practices for Remote Workers
National Cyber Security Alliance Encourages Vigilance Against Coronavirus Scams, Best Cybersecurity Practices for Remote Workers

Press
National Cyber Security Alliance Supports RSA® Conference Theme “The Human Element” with Expert Panel on Cybersecurity and Changing Human Behavior
National Cyber Security Alliance Supports RSA® Conference Theme “The Human Element” with Expert Panel on Cybersecurity and Changing Human Behavior

Press
On January 28, Data Privacy Day Encourages Consumers to “Own Their Privacy” and Businesses to Improve Their Data Privacy Practices
On January 28, Data Privacy Day Encourages Consumers to “Own Their Privacy” and Businesses to Improve Their Data Privacy Practices

Press
Free and Fun Security Awareness Videos: Brought to you by Adobe, the National Cybersecurity Alliance, and Speechless, Inc.
Free and Fun Security Awareness Videos: Brought to you by Adobe, the National Cybersecurity Alliance, and Speechless, Inc.

Press
National Cyber Security Alliance Hosts Online Safety Workshops for Consumers and Small Businesses in Indianapolis
National Cyber Security Alliance Hosts Online Safety Workshops for Consumers and Small Businesses in Indianapolis

Press
16th Annual National Cybersecurity Awareness Month Begins Today
16th Annual National Cybersecurity Awareness Month Begins Today

Press
Countdown to National Cybersecurity Awareness Month 2019 Begins
Countdown to National Cybersecurity Awareness Month 2019 Begins

Press
The National Cyber Security Alliance and ITSPmagazine Announce Partnership in Support of CyberSecure My Business™
The National Cyber Security Alliance and ITSPmagazine Announce Partnership in Support of CyberSecure My Business™

Press
The National Cyber Security Alliance and the Better Business Bureau Recommend Top Online “Take-Action Tips” to Help Keep You Safe and Secure
The National Cyber Security Alliance and the Better Business Bureau Recommend Top Online “Take-Action Tips” to Help Keep You Safe and Secure

Press
The National Cyber Security Alliance Welcomes Three Prominent Industry Leaders to Board of Directors
The National Cyber Security Alliance Welcomes Three Prominent Industry Leaders to Board of Directors

Press
The National Cyber Security Alliance Welcomes New Board Members
The National Cyber Security Alliance Welcomes New Board Members

Press
National Cyber Security Alliance Reminds Organizations of All Sizes that “Privacy is Good for Business”
National Cyber Security Alliance Reminds Organizations of All Sizes that “Privacy is Good for Business”

Press
Data Privacy Day 2019 Reminds Businesses and Consumers About the Value of Personal Data and the Need to Protect It
Data Privacy Day 2019 Reminds Businesses and Consumers About the Value of Personal Data and the Need to Protect It

Press
Make a Digital New Year’s Resolution: Keep Your Computer Systems and Software Up to Date
Make a Digital New Year’s Resolution: Keep Your Computer Systems and Software Up to Date

Press
National Cyber Security Alliance Responds to Marriott Cybersecurity Incident
National Cyber Security Alliance Responds to Marriott Cybersecurity Incident

Press
The National Cyber Security Alliance Appoints Kelvin Coleman as Executive Director
The National Cyber Security Alliance Appoints Kelvin Coleman as Executive Director

Press
Cheers to Safe Cybershopping!
Cheers to Safe Cybershopping!

Press
Intel and National Cyber Security Alliance Team Up to Remind Cool Cats Nationwide to Protect Their Nine Digital Lives and #UpdateMeow
Intel and National Cyber Security Alliance Team Up to Remind Cool Cats Nationwide to Protect Their Nine Digital Lives and #UpdateMeow

Press
The National Cyber Security Alliance Announces Winners for the First-Ever National Cyber Security Alliance Awards
The National Cyber Security Alliance Announces Winners for the First-Ever National Cyber Security Alliance Awards

Press
Safeguarding the Nation’s Infrastructure Needs to Be “Our Shared Responsibility”
Safeguarding the Nation’s Infrastructure Needs to Be “Our Shared Responsibility”

Press
It’s Everyone’s Job to Ensure Online Safety at Work
It’s Everyone’s Job to Ensure Online Safety at Work

Press
The Severe Shortage of Cybersecurity Professionals is a Key Risk to Our Nation’s Security
The Severe Shortage of Cybersecurity Professionals is a Key Risk to Our Nation’s Security

Press
Make Your Home a Haven for Online Safety
Make Your Home a Haven for Online Safety

Press
Two Weeks and Counting Until National Cybersecurity Awareness Month Kicks Off on Oct. 1
Two Weeks and Counting Until National Cybersecurity Awareness Month Kicks Off on Oct. 1

Press
Higher Ed Joins Forces with Nonprofit and Business to Promote Cyber Safety on Campus
Higher Ed Joins Forces with Nonprofit and Business to Promote Cyber Safety on Campus

Press
All Systems Go: The 15th Annual National Cybersecurity Awareness Month Launches on October 1
All Systems Go: The 15th Annual National Cybersecurity Awareness Month Launches on October 1

Press
Stay #CyberAware on Mobile Devices during Internet Safety Month and All Year Round
Stay #CyberAware on Mobile Devices during Internet Safety Month and All Year Round

Press
National Cyber Security Alliance Executive Director Russ Schrader Addresses Cyber Challenges Facing Small Businesses at Senate Hearing
National Cyber Security Alliance Executive Director Russ Schrader Addresses Cyber Challenges Facing Small Businesses at Senate Hearing

Press
The National Cyber Security Alliance and Better Business Bureau Encourage “Digital Spring Cleaning” for Everyone
The National Cyber Security Alliance and Better Business Bureau Encourage “Digital Spring Cleaning” for Everyone

Press
NCSA and Nasdaq Cybersecurity Summit Examines How to Better Protect the Expanding Cloud Ecosystem From Security Threats
NCSA and Nasdaq Cybersecurity Summit Examines How to Better Protect the Expanding Cloud Ecosystem From Security Threats

Press
National Cyber Security Alliance Supports RSA® Conference’s Mission to Inspire All Digital Citizens to Take Action and Help Secure the World Against Cyber Threats
National Cyber Security Alliance Supports RSA® Conference’s Mission to Inspire All Digital Citizens to Take Action and Help Secure the World Against Cyber Threats

Press
The National Cyber Security Alliance Appoints Russell Schrader as Interim Executive Director
The National Cyber Security Alliance Appoints Russell Schrader as Interim Executive Director

Press
Data Privacy Day Reminds Everyone About the Value of Their Personal Information and How to Manage Online Privacy
Data Privacy Day Reminds Everyone About the Value of Their Personal Information and How to Manage Online Privacy

Press
New Video Showcases How Financial Institutions Work with Government Agencies to Remediate Phishing Cyber Attack
New Video Showcases How Financial Institutions Work with Government Agencies to Remediate Phishing Cyber Attack

Press
National Cyber Security Awareness Month Highlights Strengthening the Cyber Workforce as a Starting Point to a Safer, More Secure Online Future
National Cyber Security Awareness Month Highlights Strengthening the Cyber Workforce as a Starting Point to a Safer, More Secure Online Future

Press
Second Annual National Cyber Security Alliance Survey Reveals Complex Digital Lives of American Teens and Parents, Highlights Gender Divide
Second Annual National Cyber Security Alliance Survey Reveals Complex Digital Lives of American Teens and Parents, Highlights Gender Divide

Press
National Cyber Security Awareness Month Reminds Everyone That Smart Devices Are Fueled By Our Personal Information
National Cyber Security Awareness Month Reminds Everyone That Smart Devices Are Fueled By Our Personal Information

Press
Organization Leaders and Employees Reminded That “Cybersecurity in the Workplace Is Everyone’s Business” This National Cyber Security Awareness Month
Organization Leaders and Employees Reminded That “Cybersecurity in the Workplace Is Everyone’s Business” This National Cyber Security Awareness Month

Press
National Cyber Security Alliance Statement Following Report on Three Billion Accounts Hacked in 2013 Yahoo Breach
National Cyber Security Alliance Statement Following Report on Three Billion Accounts Hacked in 2013 Yahoo Breach

Press
National Cyber Security Awareness Month Launches With a Call to STOP. THINK. CONNECT.™ Online
National Cyber Security Awareness Month Launches With a Call to STOP. THINK. CONNECT.™ Online

Press
On October 1, Digital Citizens Worldwide Will Be Reminded of Our Shared Global Responsibility to Secure the Internet
On October 1, Digital Citizens Worldwide Will Be Reminded of Our Shared Global Responsibility to Secure the Internet

Press
National Cyber Security Alliance Responds to Equifax Breach
National Cyber Security Alliance Responds to Equifax Breach

Press
The Countdown to National Cyber Security Awareness Month Begins!
The Countdown to National Cyber Security Awareness Month Begins!

Press
SC Magazine’s Women in IT Security: Influencers Honors NCSA Director of Special Projects and Government Affairs Kristin Judge
SC Magazine’s Women in IT Security: Influencers Honors NCSA Director of Special Projects and Government Affairs Kristin Judge

Press
National Cyber Security Alliance Statement on International Cyber Attack
National Cyber Security Alliance Statement on International Cyber Attack

Press
NCSA and Nasdaq Cybersecurity Summit Tackles Cyber-Related “People Problems” in the Workplace
NCSA and Nasdaq Cybersecurity Summit Tackles Cyber-Related “People Problems” in the Workplace

Press
The National Cyber Security Alliance and Thatcher & Company Awarded Two Silver Anvils from PRSA
The National Cyber Security Alliance and Thatcher & Company Awarded Two Silver Anvils from PRSA

Press
NCSA Statement on the Ransomware Attack
NCSA Statement on the Ransomware Attack

Press
National Cyber Security Alliance and Better Business Bureau Remind All Internet Users to Do a Digital Spring Cleaning and Clear Out Cyber Clutter
National Cyber Security Alliance and Better Business Bureau Remind All Internet Users to Do a Digital Spring Cleaning and Clear Out Cyber Clutter

Press
The National Cyber Security Alliance and Nasdaq Host Timely, Enterprise-focused Discussion about Cybersecurity Risk Management and Emerging Threats
The National Cyber Security Alliance and Nasdaq Host Timely, Enterprise-focused Discussion about Cybersecurity Risk Management and Emerging Threats

Press
NCSA Tribute to Howard Schmidt
NCSA Tribute to Howard Schmidt

Press
Data Privacy Day Reminds Organizations That Protecting Customers’ Privacy is Critical to Their Business
Data Privacy Day Reminds Organizations That Protecting Customers’ Privacy is Critical to Their Business

Press
The National Cyber Security Alliance Recommends “Five Digital To Do's” for 2017
The National Cyber Security Alliance Recommends “Five Digital To Do's” for 2017

Press
Response Statement: Mark Zuckerberg’s Hacked Pinterest Account
Response Statement: Mark Zuckerberg’s Hacked Pinterest Account

Press
Industry Leaders from NXP Semiconductors and Salesforce Join the National Cyber Security Alliance’s Board of Directors
Industry Leaders from NXP Semiconductors and Salesforce Join the National Cyber Security Alliance’s Board of Directors

Press
As National Cyber Security Awareness Month Comes to a Close, Focus Shifts to Securing Our Nation’s Critical Infrastructure
As National Cyber Security Awareness Month Comes to a Close, Focus Shifts to Securing Our Nation’s Critical Infrastructure

Press
Continued Growth of the “Internet of Me” Has 88 Percent of Consumers Considering the Risks of Using Connected Devices
Continued Growth of the “Internet of Me” Has 88 Percent of Consumers Considering the Risks of Using Connected Devices

Press
Fight Cybercrime During National Cyber Security Awareness Month: It’s Time to Take Action, Safeguard Devices and Protect Personal Information
Fight Cybercrime During National Cyber Security Awareness Month: It’s Time to Take Action, Safeguard Devices and Protect Personal Information

Press
Businesses of All Sizes Urged to Create Culture of Cybersecurity and Protect Assets This National Cyber Security Awareness Month
Businesses of All Sizes Urged to Create Culture of Cybersecurity and Protect Assets This National Cyber Security Awareness Month

Press
White House and the National Cyber Security Alliance Join Forces to Launch
White House and the National Cyber Security Alliance Join Forces to Launch

Press
National Cyber Security Awareness Month Launches with a Call to Action for All Digital Citizens to STOP. THINK. CONNECT.™
National Cyber Security Awareness Month Launches with a Call to Action for All Digital Citizens to STOP. THINK. CONNECT.™

Press
Fast-Approaching National Cyber Security Awareness Month Reminds All Digital Citizens That Cybersecurity is a Shared Responsibility
Fast-Approaching National Cyber Security Awareness Month Reminds All Digital Citizens That Cybersecurity is a Shared Responsibility

Press
Tips for Securing Frequent Flier Miles
Tips for Securing Frequent Flier Miles
Press
National Cyber Security Alliance Statement Following Reported Massive Data Breach at Yahoo! Inc.
National Cyber Security Alliance Statement Following Reported Massive Data Breach at Yahoo! Inc.

Press
National Cyber Security Awareness Month Is Only A Month Away!
National Cyber Security Awareness Month Is Only A Month Away!

Press
Beware of Ransomware
Beware of Ransomware

Press
Statement following report of massive data breach at major email providers
Statement following report of massive data breach at major email providers

Press
National Cyber Security Alliance Survey Reveals the Complex Digital Lives of American Teens and Parents
National Cyber Security Alliance Survey Reveals the Complex Digital Lives of American Teens and Parents

Press
National Cyber Security Alliance and Better Business Bureau Urge Digital Spring Cleaning for All Internet Users
National Cyber Security Alliance and Better Business Bureau Urge Digital Spring Cleaning for All Internet Users

Press
State Legislators Identify Major Opportunities to Address Cybersecurity Gaps
State Legislators Identify Major Opportunities to Address Cybersecurity Gaps

Press
National Cyber Security Alliance Returns to RSA® Conference with a Mission to Educate and Empower Digital Citizens of All Ages about Cybersecurity and Privacy Awareness
National Cyber Security Alliance Returns to RSA® Conference with a Mission to Educate and Empower Digital Citizens of All Ages about Cybersecurity and Privacy Awareness

Press
National Cyber Security Alliance Announces Expansion of Multi-Factor Authentication-Focused Education
National Cyber Security Alliance Announces Expansion of Multi-Factor Authentication-Focused Education

Press
White House Fact Sheet: Cybersecurity National Action Plan
White House Fact Sheet: Cybersecurity National Action Plan

Press
British Internet Users Concerned About Data Privacy Than Losing Their Income
British Internet Users Concerned About Data Privacy Than Losing Their Income

Press
Cisco Joins the National Cyber Security Alliance’s Board of Directors
Cisco Joins the National Cyber Security Alliance’s Board of Directors

Press
Digital New Year’s Resolutions To Keep Everyone Safer And More Secure Online
Digital New Year’s Resolutions To Keep Everyone Safer And More Secure Online

Press
National Cyber Security Awareness Month Seeks #TalentHack Solutions to Overcome the Cybersecurity Skills Gap
National Cyber Security Awareness Month Seeks #TalentHack Solutions to Overcome the Cybersecurity Skills Gap

Press
As the Internet of Things Grows Exponentially, National Cyber Security Awareness Month Focuses on Securing our Connected Devices and Networks
As the Internet of Things Grows Exponentially, National Cyber Security Awareness Month Focuses on Securing our Connected Devices and Networks

Press
Connected Families And Communities In The Spotlight During National Cyber Security Awareness Month
Connected Families And Communities In The Spotlight During National Cyber Security Awareness Month

Press
ESET and National Cyber Security Alliance Study Reveals Almost 80 Percent of American Homes Feel Cyber Secure Despite Unsecured Digital Doors
ESET and National Cyber Security Alliance Study Reveals Almost 80 Percent of American Homes Feel Cyber Secure Despite Unsecured Digital Doors

Press
Small And Midsized Businesses Learn To Protect Their Digital Assets During National Cyber Security Awareness Month
Small And Midsized Businesses Learn To Protect Their Digital Assets During National Cyber Security Awareness Month

Press
NCSA statement following report of data breach at Experian, Exposing T-Mobile Customer Data
NCSA statement following report of data breach at Experian, Exposing T-Mobile Customer Data

Press
National Cyber Security Awareness Month Kicks Off As Growing Global Coalition Urges Internet Users Everywhere To STOP. THINK. CONNECT.
National Cyber Security Awareness Month Kicks Off As Growing Global Coalition Urges Internet Users Everywhere To STOP. THINK. CONNECT.

Press
As National Cyber Security Awareness Month Approaches, Internet Users Are Reminded Why Being Cyber Smart is Critical to Our Lives
As National Cyber Security Awareness Month Approaches, Internet Users Are Reminded Why Being Cyber Smart is Critical to Our Lives

Press
One-Month Countdown to National Cyber Security Awareness Month Begins
One-Month Countdown to National Cyber Security Awareness Month Begins

Press
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy
National Cyber Security Alliance Encourages Digital Citizens to Better Understand How to Manage Their Privacy

Press
Council of Anti-Phishing Japan Launches STOP.THINK.CONNECT. Cybersecurity Awareness Campaign with National Public-Private Coalition
Council of Anti-Phishing Japan Launches STOP.THINK.CONNECT. Cybersecurity Awareness Campaign with National Public-Private Coalition

Press
STOP.THINK.CONNECT.™: Broad Government, Industry and Non-Profit Coalition Unveils First-Ever Coordinated Online Safety Message
STOP.THINK.CONNECT.™: Broad Government, Industry and Non-Profit Coalition Unveils First-Ever Coordinated Online Safety Message
